The Tennessee Information Protection Act
The Tennessee Information Protection Act (TIPA) is a comprehensive data privacy law that is designed to protect the privacy of Tennessee residents. The bill was approved by lawmakers in 2023, and it is part of a growing trend of state-level privacy regulation legislation. In this article, we will delve into the specifics of TIPA, its requirements, and its implications for businesses in the new regulatory compliance paradigm.

The Trend of State Privacy Laws in the United States
Tennessee’s legislature passed the Tennessee Information Protection Act on April 21, 2023. This legislation is part of a trend among an increasing number of states passing data privacy laws to protect their citizens’ privacy. Four states have passed data privacy laws this spring alone. There are currently nine states with data privacy laws, including California, Colorado, Connecticut, Indiana, Iowa, Montana, Virginia, and Utah. Although TIPA will not take effect until July 1, 2025, its approval marks another significant step forward in states’ efforts to protect their residents’ privacy rights.
What Is the Tennessee Information Protection Act (TIPA)?
The Tennessee Information Protection Act mandates businesses to take necessary measures to protect the personally identifiable information (PII) of Tennessee residents in the event of a data breach. TIPA applies to any person or entity that owns, licenses, or maintains personal information of Tennessee residents in the regular course of business. Compliance with TIPA is essential for businesses that risk financial and reputational damage from a data breach, but it can also help businesses build trust with their customers.
How TIPA Compares to Virginia Consumer Data Protection Act
TIPA draws heavily on the recently enacted Virginia Consumer Data Protection Act (VCDPA). Both frameworks share similar definitions, obligations, and core consumer rights, such as the requirement to obtain consent for the processing of sensitive personal data and the right of consumers to opt out of data sales, targeted advertising, and significant profiling decisions.
However, there are several ways in which TIPA deviates from the VCDPA, making it a less protective privacy rule overall. These include coverage thresholds that are likely to apply to fewer businesses, broad carve-outs for pseudonymous data that could limit the impact of opt-out rights, and an insurance industry exemption.
One area where TIPA is stronger than the VCDPA is in providing a longer right to cure for alleged violations of the law. TIPA also establishes a first-of-its-kind affirmative defense for businesses that reasonably conform to the National Institute of Standards and Technology (NIST) Privacy Framework or other documented policies, standards, and procedures designed to safeguard consumer privacy. However, it is unclear how this defense would work in practice.
Another distinction is that TIPA allows courts to award treble damages for willful or knowing violations, whereas the VCDPA only allows for a maximum civil penalty of $7,500 per violation.
The Tennessee Information Protection Act Scope
TIPA applies to certain entities operating in Tennessee that handle the personal information of Tennessee residents. To be subject to TIPA, an entity (referred to as a “controller”) must meet the following criteria:
- Have an annual revenue of over $25,000,000
- Either (a) process the personal information of 175,000 or more Tennessee residents during a calendar year, or (b) process the personal information of at least 25,000 consumers and derive more than half of its gross revenue from selling personal information
The term “revenue” is not defined by TIPA, but it is likely to refer to the entity’s annual gross revenue worldwide, as in California and Utah.
Also, TIPA defines a “consumer” as a natural person who is a Tennessee resident acting in a personal capacity. This means that employees and business-to-business contacts are not considered consumers under TIPA.
Lastly, TIPA also covers vendors and other parties (known as “processors”) that handle personal information on behalf of a controller. This can include service providers and software providers.
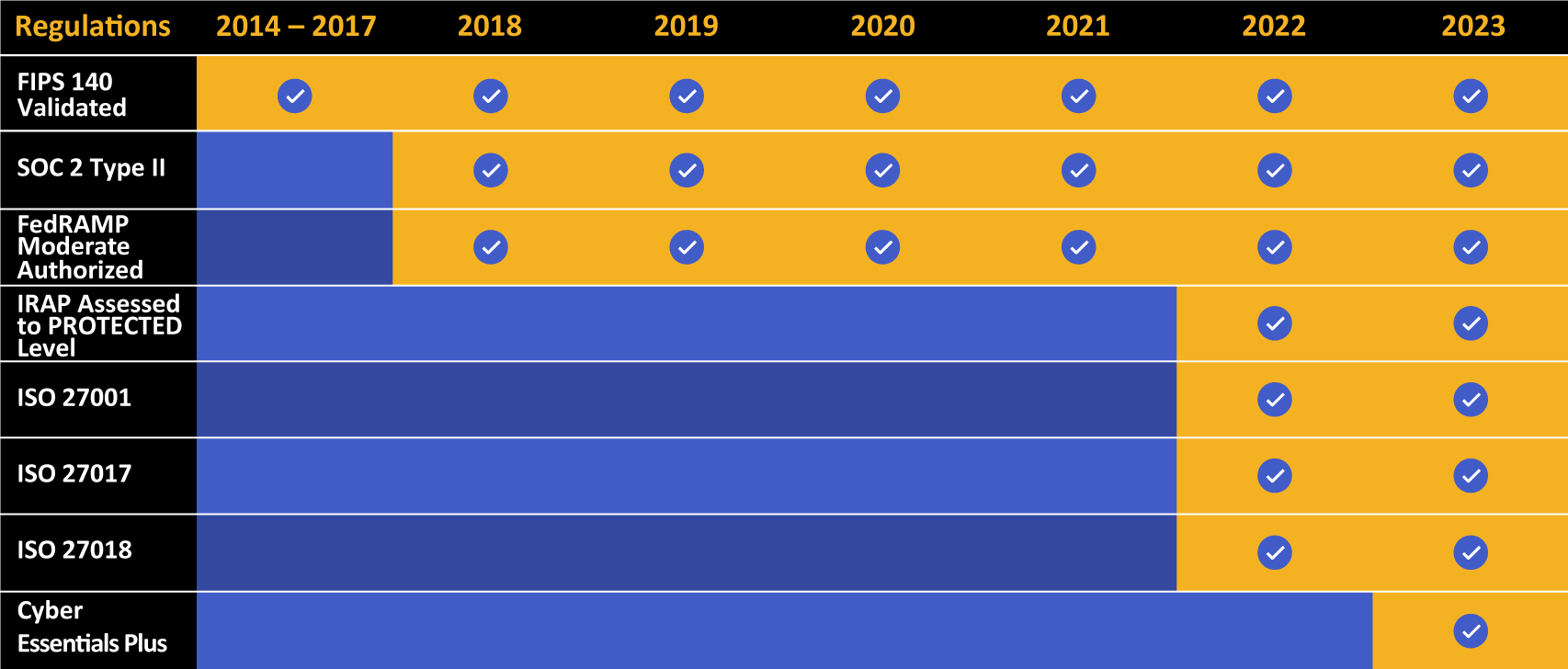
Kiteworks touts a long list of compliance and certification achievements.
What Is Considered Personal Information Under TIPA?
TIPA defines personal information as a combination of a resident’s first name or initial and last name, along with any of the following:
- Social Security number
- Driver’s license number or government-issued identification card number
- Account number, credit or debit card number, in combination with any required security code, access code, or password that would permit access to a resident’s financial account
- Health insurance policy number or health insurance subscriber identification number in combination with any other unique identifier used by a health insurer to identify the resident
- Username or email address, in combination with a password or security question and answer that would permit access to an online account
Consumer Rights and Opt-outs Under TIPA
TIPA establishes certain rights for consumers whose personal information is processed by controllers subject to TIPA. Specifically, consumers have the following rights under TIPA:
- The right to access their personal information, including the right to confirm whether a controller is processing their personal information
- The right to request deletion of personal information provided by or obtained about them
- The right to obtain a copy of their personal information in a portable format, but only to the extent the data was previously provided by the consumer
- The right to correct inaccuracies in their personal information, but only to the extent the data was previously provided by the consumer
- The right to appeal any denial of a consumer request relating to the above rights
In addition, TIPA requires controllers to give consumers the ability to opt out of the following practices:
- Profiling that produces legal or similarly significant effects concerning the consumer
- Targeted advertising
- The sale of personal information
However, it’s important to note that TIPA provides that these opt-out rights do not apply to “pseudonymous” data (i.e., data that is subject to controls preventing the controller from accessing identifiers), or to de-identified data (i.e., data that cannot be attributed to a specific natural person or device linked to a person).
Controller and Processor Responsibilities Under TIPA
TIPA places certain obligations on controllers and processors that handle the personal information of Tennessee residents. Controllers, for instance, must ensure that the processing of personal information is limited to what is reasonably necessary and proportional for the purposes identified in their privacy notices. They must also implement reasonable technical and organizational measures to protect the security of personal information, avoid unlawful discrimination against consumers who exercise their rights under TIPA, and be transparent in their privacy notices.
In addition, controllers must ensure that their contracts with processors include provisions to control the relationship and require the processor to assist the controller in meeting its obligations to respond to consumer requests related to their personal information.
Processors, for their part, must follow the processing instructions of the controller and provide necessary information to assist the controller in meeting its obligations under TIPA.
Controllers must obtain the consumer’s consent to process sensitive data, or in the case of sensitive data concerning a known child, process the data in accordance with federal law.
Furthermore, TIPA requires controllers to conduct data protection assessments for processing activities created or generated on or after July 1, 2024. These assessments must consider the benefits of the processing activity to the controller, consumers, and other stakeholders, as well as any potential risks to consumer rights. The assessments must take into account the use of de-identified data, the reasonable expectations of consumers, and the context of the processing activity. Processors must reasonably assist controllers with undertaking these assessments.
It’s important to note that the data protection assessment requirement does not apply retroactively to processing activities conducted before July 1, 2024.
Notable Provisions in TIPA
TIPA contains several notable provisions, including specific exclusions for certain entities such as financial institutions covered by the Gramm-Leach-Bliley Act (GLBA) and those subject to Health Insurance Portability and Accountability Act (HIPAA) and Family Educational Rights and Privacy Act (FERPA) regulations. The statute defines “consumers” as only natural persons who are residents of Tennessee and who are acting in a personal context.
Consumers have the right to demand deletion, access, correction, and data portability of their personal information, as well as the right to opt out of the sale of personal data and targeted advertising.
Data protection assessments are required for certain processing activities involving personal information, including targeted advertising, the sale of personal data, and processing of sensitive data, among others.
The statute allows for civil penalties of up to $7,500 for each violation, with a 60-day cure period for violations. Businesses must also create and maintain a written privacy program that conforms to the NIST Privacy Framework in order to receive an affirmative defense against alleged violations of TIPA.
TIPA Enforcement
TIPA grants the exclusive authority to enforce its provisions to the Tennessee Attorney General (AG), and no private right of action is permitted. If a violation is alleged, controllers and processors have a 60-day right-to-cure period to remedy any noncompliance. Compared to other state privacy laws, this cure period does not sunset. If the controller or processor fails to cure, the AG may impose a civil penalty of up to $7,500 per violation.
A controller or processor accused of violating TIPA may assert an affirmative defense if they have implemented and complied with a written privacy program that meets the requirements of the NIST Privacy Framework titled “A Tool for Improving Privacy through Enterprise Risk Management Version 1.0,” or “other documented policies, standards, and procedures designed to safeguard consumer privacy.” If the NIST or a comparable privacy framework issues a revised version of its privacy framework, the controller or processor must update its privacy program to conform with the revised framework within two years of the publication date.
TIPA Compliance
Businesses that collect personal information about Tennessee residents must take several steps to comply with TIPA. These include:
- Develop and implement a written information security program that includes administrative, technical, and physical safeguards to protect personal information
- Conduct periodic risk assessments to identify and address potential security vulnerabilities
- Train employees on the proper handling of personal information
- Implement procedures for securely disposing of personal information when it is no longer needed
- Respond promptly to data breach incidents and provide notifications to affected Tennessee residents as required by law
Businesses that fail to comply with TIPA may face significant legal and financial consequences. It is essential for businesses therefore to understand the requirements of the law and take steps to ensure compliance.
Demonstrate Compliance With TIPA Using Kiteworks
Kiteworks helps businesses demonstrate compliance with the Tennessee Information Protection Act by providing a Private Content Network for the handling and sharing of Tennesseans’ personal information. TIPA imposes significant obligations on businesses when handling personal information, and failure to comply can result in severe penalties and reputational damage.
Kiteworks uses a self-contained and preconfigured hardened virtual appliance to minimize the attack surface of an organization’s communication channels. Kiteworks employs extensive security controls, such as multi-factor authentication, granular policy controls, role-based permissions, security infrastructure integrations, and end-to-end encryption to ensure the privacy of personal information.
By using Kiteworks, businesses can properly track, control, and secure digital communications of sensitive content belonging to Tennessee citizens when they share it with trusted parties by email, file sharing, file transfer, and other channels.
Kiteworks’ comprehensive audit logs also enable organizations to demonstrate compliance with data privacy regulations like the Tennessee Information Protection Act, the General Data Protection Regulation (GDPR), and HIPAA.
For more information on how Kiteworks can be used to comply with the Tennessee Information Protection Act, schedule a custom-tailored demo today.

