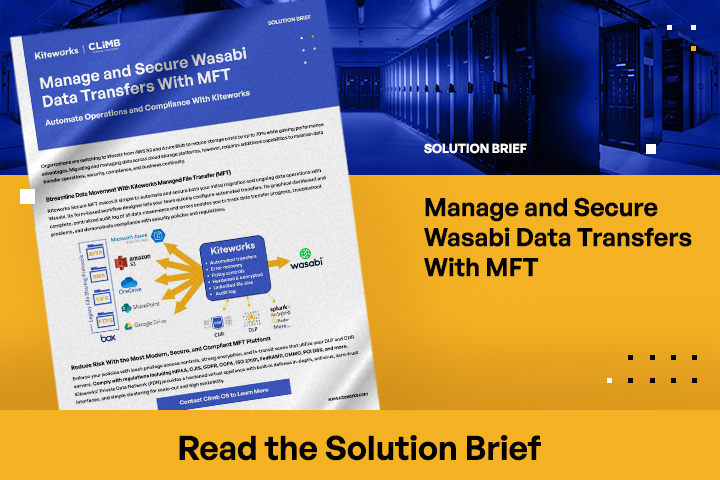
Resources
Achieve File and Email Data Communications Securely in the Compliance Era
Highlights From the Top 11 Data Breaches in 2024 Report


Highlights From the Top 11 Data Breaches in 2024 Report
Top 11 Data Breaches in 2024 and Their Risk Exposure Scores


Top 11 Data Breaches in 2024 and Their Risk Exposure Scores
Secure Your Critical Data With the Kiteworks Private Data Network


Secure Your Critical Data With the Kiteworks Private Data Network
State of CMMC 2.0 Preparedness in the DIB: Key Findings & Implementation Strategies


State of CMMC 2.0 Preparedness in the DIB: Key Findings & Implementation Strategies
Closing the Gap: Critical Insights on Achieving CMMC 2.0 Compliance


Closing the Gap: Critical Insights on Achieving CMMC 2.0 Compliance
Zero Trust Data Exchange: Secure Your Sensitive Data With Kiteworks


Zero Trust Data Exchange: Secure Your Sensitive Data With Kiteworks
2024 Data Security and Compliance Stats and Trends in Review


2024 Data Security and Compliance Stats and Trends in Review
2025 Managing Private Content Exposure Risk Forecast Report: Highlights


2025 Managing Private Content Exposure Risk Forecast Report: Highlights
2025 Cybersecurity Data Privacy and Compliance Prediction Highlights


2025 Cybersecurity Data Privacy and Compliance Prediction Highlights
2025 Forecast Report for Managing Private Content Exposure Risk


2025 Forecast Report for Managing Private Content Exposure Risk
Product Brief – Microsoft 365 Purview Comparison to Kiteworks Product Brief – Microsoft 365 Purview Comparison to Kiteworks
Product Brief – Microsoft 365 Purview Comparison to Kiteworks Product Brief – Microsoft 365 Purview Comparison to Kiteworks
Kiteworks Preserves Content for eDiscovery
Kiteworks Preserves Content for eDiscovery
Seamless eDiscovery of Encrypted Email Across Archiving Platforms With Kiteworks and Bluesource
Seamless eDiscovery of Encrypted Email Across Archiving Platforms With Kiteworks and Bluesource
Kiteworks Advanced Governance: Transform Compliance, Legal Hold & Threat Prevention
Kiteworks Advanced Governance: Transform Compliance, Legal Hold & Threat Prevention
Secure Children’s Data and Comply With COPPA Regulations
Secure Children’s Data and Comply With COPPA Regulations
Embedded Managed Detection and Response (MDR)
Embedded Managed Detection and Response (MDR)
Empowering Compliance With the DoD’s Defense Industrial Base Cybersecurity Strategy 2024
Empowering Compliance With the DoD’s Defense Industrial Base Cybersecurity Strategy 2024
The Financial Services Solution Guide to DORA Regulation UK
The Financial Services Solution Guide to DORA Regulation UK
CMMC Mapping: Sensitive Content Communications for CMMC 2.0 Compliance
CMMC Mapping: Sensitive Content Communications for CMMC 2.0 Compliance
FedRAMP Private Cloud: 5 Reasons Why Security-first Businesses Choose FedRAMP
FedRAMP Private Cloud: 5 Reasons Why Security-first Businesses Choose FedRAMP
Kiteworks Private Content Networks in the Compliance Era
Kiteworks Private Content Networks in the Compliance Era
CISA Security-by-Design and Default: Requirements & Kiteworks Features
CISA Security-by-Design and Default: Requirements & Kiteworks Features
Kiteworks Advances NSA’s Zero Trust Maturity Model Across Data Layers
Kiteworks Advances NSA’s Zero Trust Maturity Model Across Data Layers
Data Sovereignty and GDPR [Understanding Data Security]
Data Sovereignty and GDPR [Understanding Data Security]
How Kiteworks Helps Advance the NSA’s Zero Trust at the Data Layer Model