
Protecting Your Business With NIST CSF Compliance
Today, the exchange of content is critical to any business’s bottom line. Collaboration with customers, partners, consultants, and other stakeholders has become critical to business success. Whenever content is shared externally, however, the risk of exposure increases. Managing that risk becomes even more difficult if the content is sensitive (and it often is). In addition to exposure risk, demonstrating regulatory compliance whenever sensitive content is shared, and therefore outside of your control, can be difficult to prove.
At Kiteworks, we understand there is an inherent business problem when it comes to sensitive content. Thus, I am excited to share how we are taking an approach within Kiteworks to help solve for this business pain point inside our Private Content Network.
The NIST Cybersecurity Framework and Kiteworks
Over the past decade, National Institute of Standards and Technology (NIST) has played a critical role in identifying and developing a cybersecurity framework for voluntary use to support overall cybersecurity risk management for any business in the United States. The purpose of this framework is to provide essential supporting structure for businesses to expand their current structure into something more useful in protecting themselves from a cyberattack.
For Kiteworks customers, we are applying this framework as it relates to protecting sensitive content so that the appropriate business group in charge of managing cybersecurity risk management has full control. Application of the NIST Cybersecurity Framework (NIST CSF) within the Kiteworks Private Content Network will complement existing capabilities and will be made available to all Enterprise Package customers.
The core tenets of NIST CSF include: Identify, Protect, Detect, Respond, and Recover. To appropriately manage cybersecurity risk, it is important for assets that must be managed to be IDENTIFIED so that appropriate measures can be set to PROTECT these assets. Once assets are identified and protected, only then can businesses DETECT any and all activity around those assets. This, in turn, enables timely RESPONSE and RECOVERY in the event of a cyberattack.
At the end of the day, risk management is an ongoing process of identifying, assessing, and responding to risk against the likelihood of an event occurring. Kiteworks supports our customers in identifying and protecting their most sensitive content by way of asset management, giving our customers a unique tool.
Core Tenets of NIST Cybersecurity Framework Aligned to Kiteworks
The following is an overview of the core tenets of NIST CSF and how Kiteworks capabilities will align.
Identification of Sensitive Content for Cyber Protection
Kiteworks employs a flexible approach that aids in the identification of what content needs to be identified as an asset. Kiteworks customers that have invested already in data classification (MIP, Titus, etc.) will maintain this classification method, enabling the classifier to be leveraged as a way to identify that content as an asset needing protection.
Even if data classification is not in place, Kiteworks can identify content as an asset based on other attributes, such as Folder Path, Content Owner, and File Type, among others. In addition, if the content is unknown specifically, you can identify who you know is working with sensitive content so that any content they touch is assumed to be an asset.
Kiteworks understands that customers are at different stages when it comes to asset classification. Our approach to asset classification aims to meet customer requirements regardless of their current use of data classification.
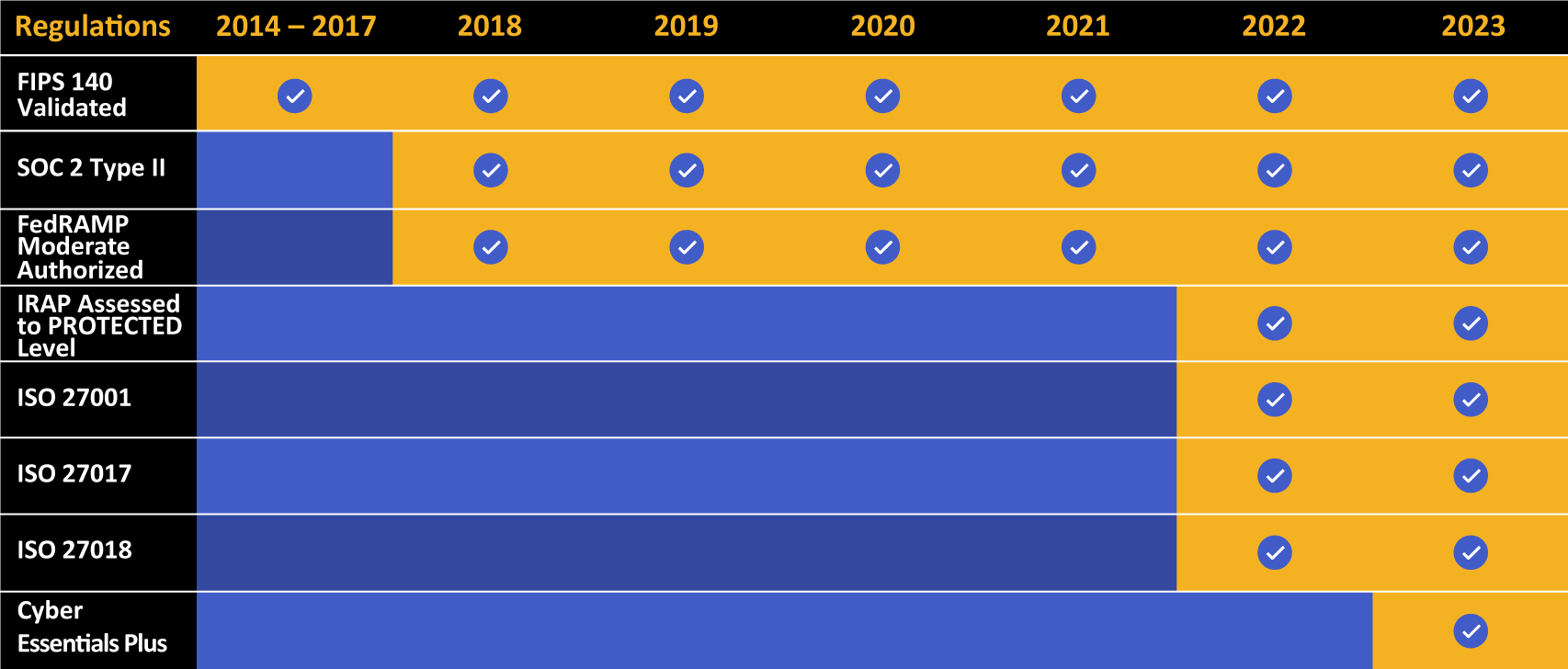
Kiteworks touts a long list of compliance and certification achievements.
Protecting Sensitive Content With Content-based Risk Policies
Once assets moving through Kiteworks are identified, the next step specifies and applies content-based risk policies to protect those assets appropriately. In speaking with customers, we understand each asset class inherits varying levels of risk depending on who is accessing the content; thus, varying levels of content control will be necessary.
In 2023, we are supporting three key content-based risk policies that can be fully customized to meet customer needs. For each policy, the user, action, and asset can be further defined:
- Collect Justification for Access
[POLICY] Allow someone to take action on the asset as long as their reason for access is collected and recorded in the asset audit log.
Current Kiteworks customers use this policy to collect the justification reason for taking an asset out of Kiteworks, which is recorded alongside the download event in the audit log. For compliance, this enhanced audit trail makes a huge impact when it comes time to collect and show proof for justified access to sensitive content.
- Modify Level of Access
[POLICY] Allow someone to take action on the asset as long as their level of access meets the compliance requirement, regardless of prior access level permissioned.
Kiteworks next-generation digital rights management is powered by SafeVIEW and SafeEDIT. SafeVIEW enables users to securely view documents within a controlled environment, enforcing access policies based on user and document attributes. It prevents unauthorized downloading, printing, or sharing of sensitive information. On the other hand, SafeEDIT allows authorized users to edit documents collaboratively while maintaining the same granular access control. It ensures that only users with the appropriate attributes can modify specific parts of a document. Both features rely on administrator-defined policies that dynamically control access based on attributes, ensuring that sensitive data remains secure throughout its lifecycle.
- Block Access and Allow Access To Be Requested
[POLICY] Allow someone to take action on the asset as long as they have received compliance approval for their access requested.
For Kiteworks customers seeking to have more managed control over deciding who can and cannot access an asset on an as-needed basis, this policy facilitates a channel for the access to be requested and later approved or denied by a compliance officer. Additional policy settings will help facilitate approved access to expire after a certain time period or passage of a specified number of views.
Detecting Movement of Sensitive Content Through Reporting Insights
As we build out the NIST CSF identification and protection capabilities in the Kiteworks Private Content Network, how asset management compliance is relayed in an audit log is at the forefront of our development process. This audit log includes full transparency around the assignment of an asset class, thus enabling full tracking and reporting on events around an asset class. In addition, any unique information collected as a part of the content policy will be collected and displayed in the audit trail.
This provides a level of transparency around the movement of sensitive content that is otherwise extremely difficult to produce for most companies.
How Organizations Can Become Development Partners
If this blog post resonates with business problems facing your organization, you can provide input to our product team by becoming a development partner. Benefits include early access to feature development and direct contact with our product and design team. Contact me at victoria.foster@kiteworks.com.
Additional Resources
- Report How to Manage Your Sensitive Content Exposure Risk in 2023
- Blog Post 8 Types of Data You Need to Encrypt
- Case Study Learn How Mandiant Protects the Sensitive Content That Helps Protect Businesses Worldwide
- Article What Is the NIST Cybersecurity Framework?
- Case Study NIST Privacy Framework for Protecting Sensitive Data


