
Empowering Your Cybersecurity With the NIST Cybersecurity Framework (CSF)
The National Institute of Standards and Technology Cybersecurity Framework (NIST CSF) consists of standards, guidelines, and best practices that organizations can use to manage cybersecurity risk. NIST is part of the U.S. Department of Commerce and has the charter to help organizations reduce their cybersecurity risk.
Cybersecurity Framework Primer
A cybersecurity framework is a comprehensive approach to protect information assets from cyber threats. It is a set of guidelines, policies, procedures, and best practices that help organizations manage and mitigate risks to their data and systems. A typical cybersecurity framework includes risk assessment, vulnerability management, incident response, and continuous monitoring. It also covers areas such as access controls, authentication, encryption, and data backup and recovery. Implementing a cybersecurity framework helps organizations establish a strong defense against cyberattacks and reduce the likelihood of data breaches. By adopting a comprehensive cybersecurity framework, businesses can safeguard their reputation, brand, and sensitive information.
Understanding the National Institute of Standards and Technology (NIST): An Introduction
The National Institute of Standards and Technology, or NIST, is the federal government’s central technology and security standards authority. It was founded in 1901 as the Bureau of Standards, a national agency for weights, measures, and scientific standards. In 1988, the agency adopted the NIST name to reflect its evolving mission as an agency geared toward technological and scientific advancement.
In modern government operations, the NIST mission mandates that it covers a few critical areas around technology. These areas include standards and requirements that federal agencies and contractors must meet, as outlined in “Special Publication,” freely available through the NIST website.
Some important areas that NIST covers include:
- Federal Cybersecurity: As federal agencies adopt new technologies, the demand to protect sensitive information is paramount. Additionally, the Federal Information Security Modernization Act of 2014 outlines strict technical and risk-based security requirements that agencies and their partners must meet. These requirements are researched, created, maintained, and updated or retired by the NIST as part of its Special Publication series, specifically, the NIST 800 series and the Federal Information Processing Standards (FIPS) documentation. Executive Order 14028 and subsequent memorandums spell out zero trust as a mandate across federal agencies.
- Federal Cloud Service Provision: Alongside the day-to-day technologies that most agencies use, more agencies and contractors use cloud or managed services to handle data processing. To support such partnerships, NIST has also developed particular standards to regulate the use of cloud computing in federal contexts.
- Maturity: Some areas, like cloud management and technology deployment in the defense sector, have been arranged into maturity levels where different organizations can meet different maturity levels depending on their requirements, stakeholders, and constituents.
- Cryptography: Cryptography is a central part of most security standards, and through FIPS publications, NIST sets the minimum requirements for encryption.
- Identity and Access Management: As part of the NIST 800 series, the organization sets standards for the proper use of authentication technologies (Authentication Assurance Levels) and identity verification (Identity Assurance Levels)—otherwise known as identity and access management.
- Risk: With the increasing complexity and sophistication of modern cybersecurity threats, NIST is working hard to push compliance standards toward a risk-informed model where knowledge of vulnerabilities and systems supplants checklist approaches to security. This results in an integrated risk management approach.
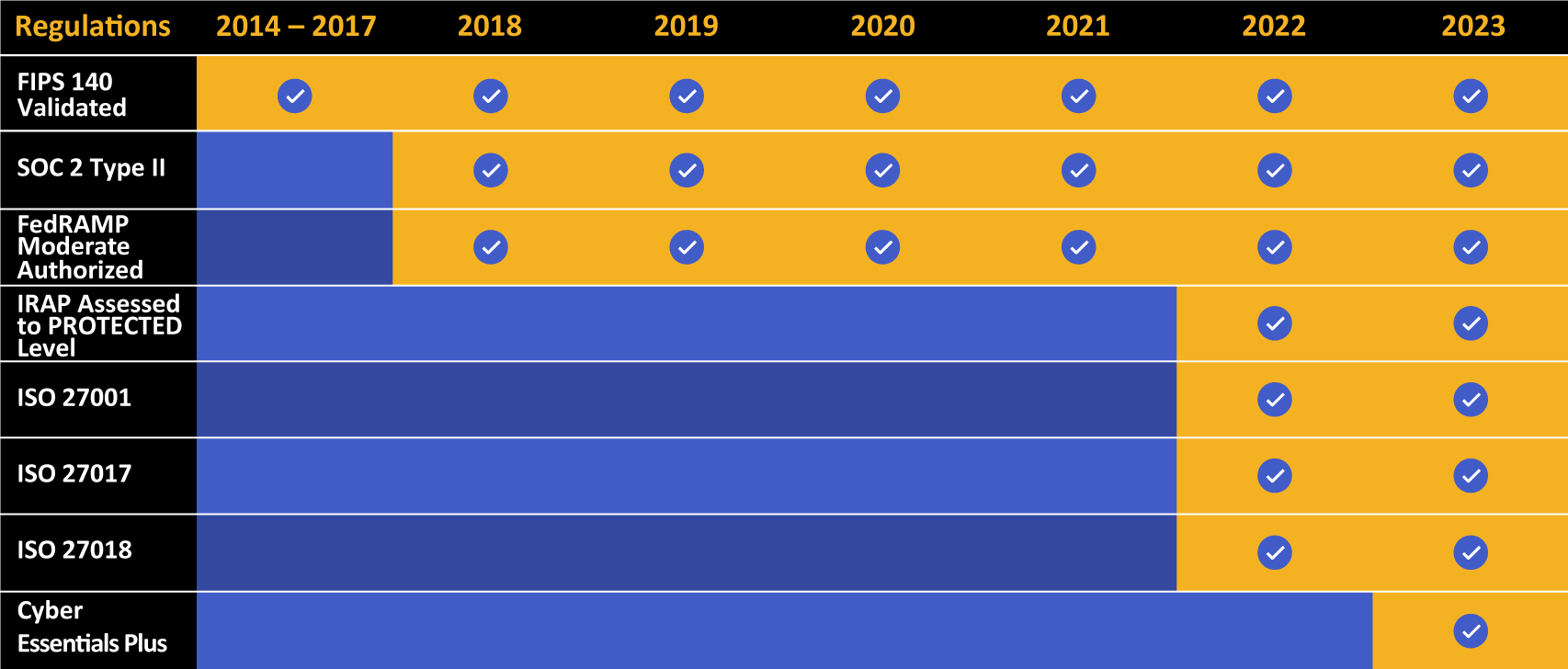
Kiteworks touts a long list of compliance and certification achievements.
As such, NIST standards inform some effective national regulations, including:
- FISMA: All federal agencies must meet Federal Information Security Management Act (FISMA) standards for security, and this includes implementing digital security and security policies and procedures. These standards derive explicitly from NIST standards like NIST Special Publication 800-53, NIST SP 800-18, FIPS 200, and FIPS 140 (among many others).
- FedRAMP: Any cloud service provider answering an RFP from a federal agency must meet minimum requirements under the Federal Risk and Authorization Management Program (FedRAMP), which is organized in a maturity level defined by FIPS 199 and NIST SP 800-60. FedRAMP draws its security controls from NIST SP 800-53 and NIST SP 800-53B.
- CMMC: The Cybersecurity Maturity Model Certification (CMMC) is a maturity-based model for handling controlled unclassified information (CUI) in the defense sector. This standard aligns with NIST SP 800-171 and NIST SP 800-172.
- HIPAA: The Health Insurance Portability and Accountability Act (HIPAA) isn’t technically a federal security standard in the same way as FISMA or FedRAMP. It governs healthcare providers and partners, but it’s managed and run by the Department of Health and Human Services (HHS). The standard is open-ended to promote flexibility, and concrete suggestions for implementing guidelines under the HIPAA Security Rule are found in NIST SP 800-66.
- Risk Management: Risk isn’t a catch-all requirement for agencies, but assessing risk is a smaller part of almost any regulation, and its importance is only increasing. The NIST Risk Management Framework (RMF) guides security risk management and compliance as detailed in several publications, namely SP 800-37 and SP 800-39.
What Is the NIST Cybersecurity Framework?
Outside of federal and defense work, NIST regulations aren’t required. Furthermore, having a library of publications doesn’t help organizations better understand the ins and outs of their cybersecurity posture.
Thus, the Cybersecurity Framework (CSF) is a bigger-picture approach to cybersecurity that helps organizations inside and outside the government take control of their security more comprehensively. This means understanding potential risks, integrating risk assessment as an organization-wide procedure, and reducing threats to their infrastructure.
The NIST CSF Core Priorities
At the heart of the CSF is the “core,” or a set of five priorities around which all concerns revolve. These include:
- Identify: An organization should be able to identify, inventory, and categorize all its relevant content assets as well as systems. This includes software, hardware, networks, data, users, and any unique systems or third-party services. Additionally, an organization must identify key roles and responsibilities related to cybersecurity and how they play a role in policies, procedures, and decision-making.
- Protect: Organizations should implement security safeguards around inventoried (identified) content assets and systems. This includes implementing identity and access management (IAM), establishing protection around data to ensure integrity and confidentiality (like encryption), establishing access controls to the folder and file level and reflective of individual user roles and privileges, and developing policies around training, equipment upgrading and patching, and governance.
- Detect: Protection is critical, but detection is just as important. Secure systems should implement automated auditing and logging measures, continuous monitoring technologies (including scans of all physical and digital networks), and ongoing detection of security anomalies.
- Respond: Once an issue is discovered, the system and responsible parties need to snap into action to respond to it. This includes that, once anomalies are detected, mitigation efforts are underway. These can consist of deploying countermeasures and closing off vulnerabilities, conducting assessments of issues, and making changes to the system based on those assessments.
- Recover: Any organization must be able to recover from a security anomaly rapidly and securely. “Recovery” means restoring any systems that were taken offline, guaranteeing the security of affected systems, implementing post-incident improvements, and communicating issues and recovery requirements to relevant stakeholders inside and outside the organization.
Why Should Organizations Implement the NIST Cybersecurity Framework?
Organizations should use the NIST Cybersecurity Framework for the following reasons:
- NIST CSF Provides a Common Language: The framework provides a common language and standardized approach to cybersecurity, allowing organizations to communicate more effectively about their cybersecurity posture.
- NIST CSF Is Customizable: The framework can be tailored to an organization’s specific needs, allowing them to prioritize and focus on the areas that are most important to their business.
- NIST CSF Helps With Risk Management: The framework is based on risk management principles, helping organizations identify, assess, and mitigate cybersecurity risks.
- NIST CSF Helps With Regulatory Compliance: The framework is aligned with industry standards and regulations, making it easier for organizations to achieve compliance with applicable laws and regulations.
- Continuous Improvement: The framework is designed to be flexible and adaptable, encouraging organizations to continuously improve their cybersecurity posture over time.
- NIST CSF Helps Organizations Enhance Reputation: Implementing the NIST Cybersecurity Framework can enhance an organization’s reputation and demonstrate its commitment to cybersecurity to stakeholders, customers, and partners.
- It Is Cost-effective: The framework can help organizations identify cost-effective cybersecurity solutions and avoid unnecessary expenditures on ineffective or redundant security measures.
How to Implement the Cybersecurity Framework
The advantage of the NIST CSF is that it gives you a way to take control of your security posture. In that way, implementing it isn’t an incredibly technical endeavor. Rather, it’s about taking stock of where your organization is and where it needs to be.
With that in mind, there are some basic, fundamental steps you can take when implementing the NIST CSF:
| Understand NIST Requirements | You don’t need an encyclopedic knowledge of NIST standards—that’s what security experts are for. Instead, you need to have a basic idea of modern security, from IAM to encryption and risk assessment. |
| Audit Company Resources | Get comfortable inventorying your systems and people. Have clearly defined and updated org charts, data flowcharts, and catalogs of hardware used in the organization, from servers and workstations to tablets and routers. |
| Implement Secure File Management and Communication Standards | Use content management and secure file sharing platforms that can meet your security needs. You don’t need to reinvent the wheel in terms of implementing technology. Simply work with a provider that can meet your operational and regulatory compliance. |
| Shift to a Risk-based Compliance Profile | Forget the idea that you can work from a checklist to implement reasonable security. By developing risk assessment and management practices, many CSF expectations (identifying assets, monitoring, etc.) follow naturally. |
| Maintain Regular Audits | You should always have auditing and continuous monitoring to cover user, system, and file access events. These are crucial for data compliance in any industry and are essential to protecting IT systems, responding to anomalies, and recovering from attacks. |
NIST Cybersecurity Framework Implementation Tiers
The NIST Cybersecurity Framework Implementation Tiers provide organizations with a structured approach for assessing and improving their cybersecurity posture. Each tier is a set of guidelines, use cases, and data points that can be used to evaluate, plan, and implement a security program.
Tier 1 includes the establishment of a cybersecurity program and begins with basic risk management and asset management.
Tier 2 focuses on the implementation of cybersecurity controls.
Tier 3 emphasizes monitoring security activities and responding to incidents.
Tier 4 is a continuous improvement process that encourages organizations to assess, plan, and adapt their cybersecurity efforts in response to changes in the environment and advances in technology. This tier encourages a cycle of assessment and improvement that can be used to move an organization toward a mature security posture and to address the ever-evolving risks of today’s digital world.
How the Financial Services Industry Can Leverage NIST for Cybersecurity Compliance
NIST provides the framework and resources that companies in the financial services industry can use to become more secure and compliant with cybersecurity regulations. NIST provides recommended controls and practices for organizations to develop and maintain a secure IT infrastructure.
It provides guidance on how to identify, assess, and mitigate risks, as well as implementing cybersecurity measures and monitoring for compliance. NIST also offers guidance on how to develop secure procedures for collecting, storing, and sharing customer data. Leveraging NIST’s framework, financial services organizations can implement best practices and mitigate potential risks to customer data and transactions.
Another Consideration: The NIST CSF Maturity Assessment Tool
The NIST Cybersecurity Framework (CSF) Maturity Assessment Tool is a tool designed to help organizations assess their current cybersecurity maturity. The tool is designed to help organizations identify gaps in their cybersecurity readiness, prioritize and plan for improvements, and measure progress.
The tool assesses an organization’s current stage of cybersecurity maturity in five areas: governance
and risk management, asset management, identity and access management, detection and response, and continuous monitoring. The maturity assessment tool is designed to provide an understanding of an organization’s strengths and weaknesses and inform a roadmap for improvement.
Organizations can use the tool to identify areas of focus and as a benchmark for measuring progress. The results of the assessment can be used to develop a roadmap for implementing cybersecurity best practices and technologies. Additionally, the results can be used to inform the allocation of resources to further improve an organization’s cybersecurity posture.
Kiteworks Helps Organizations Adhere to the NIST CSF
The heart of the CSF is a base level of data security for stored information and data in transit. This requires a cybersecurity risk management approach focused on ensuring that sensitive information is managed by administrative, technical, and physical safeguards to maintain its integrity and confidentiality. Many IT, security, and compliance leaders today plan their risk management roadmaps and communicate to their boards through the lens of NIST CSF.
The Kiteworks Private Content Network enables organizations to apply NIST CSF principles to the containers of content, such as folders, files, and email. This includes setting global policies such as disabling the transfer of sensitive content to and from certain domains and countries (geofencing). The email policy engine in Kiteworks takes Microsoft MIP sensitivity levels like “public,” “confidential,” or “secret” into account.
Leveraging the above access controls, Kiteworks empowers organizations to enforce data protection policies on groups of content to individual files in the Kiteworks platform. This plays an important role in their broader cybersecurity risk management strategy, including the ability to manage third-party risk (TPRM). Kiteworks risk management governance also extends to regulatory compliance requirements such as the Health Insurance Portability and Accountability Act (HIPAA), General Data Protection Regulation (GDPR), and Payment Card Industry Data Security Standard (PCI DSS), among others.
For more on the Kiteworks Private Content Network and NIST CSF, book a custom demo today.
Additional Resources
- Webinar How Federal Agencies Can Comply With the Zero-trust Data Requirement in EO 14028
- Case Study How Mandiant Uses Kiteworks to Protect the Sensitive Content That Helps Protect Businesses Worldwide
- Report Benchmark Your Sensitive Content Communications Privacy and Compliance
- Blog Post What Are Data Compliance Standards?
- Blog Post What Is NIST-compliant File Sharing?

