
Mastering FIPS 140-2: Essential Guide for IT and Cybersecurity Professionals
As an IT or cybersecurity professional, you understand the importance of maintaining robust security measures to protect sensitive data and systems. One crucial aspect of cybersecurity is ensuring compliance with industry standards and regulations. FIPS 140-2 is a key compliance requirement that organizations need to understand and implement to enhance their security posture.
What Data Compliance Standards Matter?
In today’s digital landscape, Managed File Transfer (MFT) plays a vital role in secure data exchange. FIPS 140-2 compliance ensures that encryption algorithms, such as the advanced encryption standard (AES), are used to protect data at rest and in transit. Additionally, technologies like Encrypting File System (EFS), File Transfer Protocol (FTP), Secure Hypertext Transfer Protocol (HTTPS), and secure FTP (SFTP) provide secure file transfer capabilities.
Risk management compliance is another critical aspect of cybersecurity. Familiarize yourself with terms like Federal Risk and Authorization Management Program, CMMC, GDPR, HTTP, Health Insurance Portability and Accountability Act (HIPA), and FISMA. Understanding these terms will help you navigate the complex landscape of compliance requirements.
| Topics | Discussions |
|---|---|
| All About FIPS 140-2 | Unlock the power of FIPS 140-2 compliance and enhance your organization’s cybersecurity posture. Learn about FIPS, FIPS compliance, and FIPS 140-2 in this comprehensive guide for IT and cybersecurity professionals. |
| Unlocking the Power of FIPS 140-2: A Game Changer for Enterprise Security Across Industries | Discover how FIPS 140-2 compliance can revolutionize enterprise security across various industries. Explore the benefits and implementation strategies to strengthen your organization’s cybersecurity defenses. |
| Key FIPS Compliance Features and Technical Specifications for Enhanced Security | Explore the essential features and technical specifications of FIPS compliance. Learn how these standards can enhance your organization’s security and protect against potential threats. |
| Uncovering FIPS Challenges: Navigating Non-Compliant Protocols in Cybersecurity | Understand the challenges associated with non-compliant protocols in cybersecurity. Learn how to navigate these obstacles and ensure your organization’s adherence to FIPS compliance. |
| Unlocking Key Compliance Advantages with FIPS 140-2 for Enhanced Cybersecurity | Discover the advantages of FIPS 140-2 compliance for enhanced cybersecurity. Learn how implementing these standards can strengthen your organization’s security posture and protect against evolving threats. |
| Essential Business Cybersecurity Statistics: A Must-Read for IT Professionals and CISOs | Stay informed about the latest cybersecurity statistics and trends. Gain valuable insights to make informed decisions and develop effective strategies to safeguard your organization’s data and systems. |
| Mastering FIPS Workflows: Essential Industry Standards for Optimal Cybersecurity | Learn about the workflows and industry standards associated with FIPS compliance. Gain a comprehensive understanding of the best practices to ensure optimal cybersecurity within your organization. |
| Kiteworks Private Content Network for FIPS 140-2 | Discover how Kiteworks Private Content Network can help organizations achieve FIPS 140-2 compliance. Explore the features and benefits of this secure file sharing solution. |
| FAQs About FIPS Compliance | Find answers to frequently asked questions about FIPS compliance. Get clarity on common queries and gain a deeper understanding of the requirements and implications of FIPS 140-2. |
| Additional Resources | Access additional resources to further enhance your knowledge of FIPS compliance and cybersecurity best practices. Explore articles, whitepapers, and case studies to stay up-to-date with the latest industry insights. |
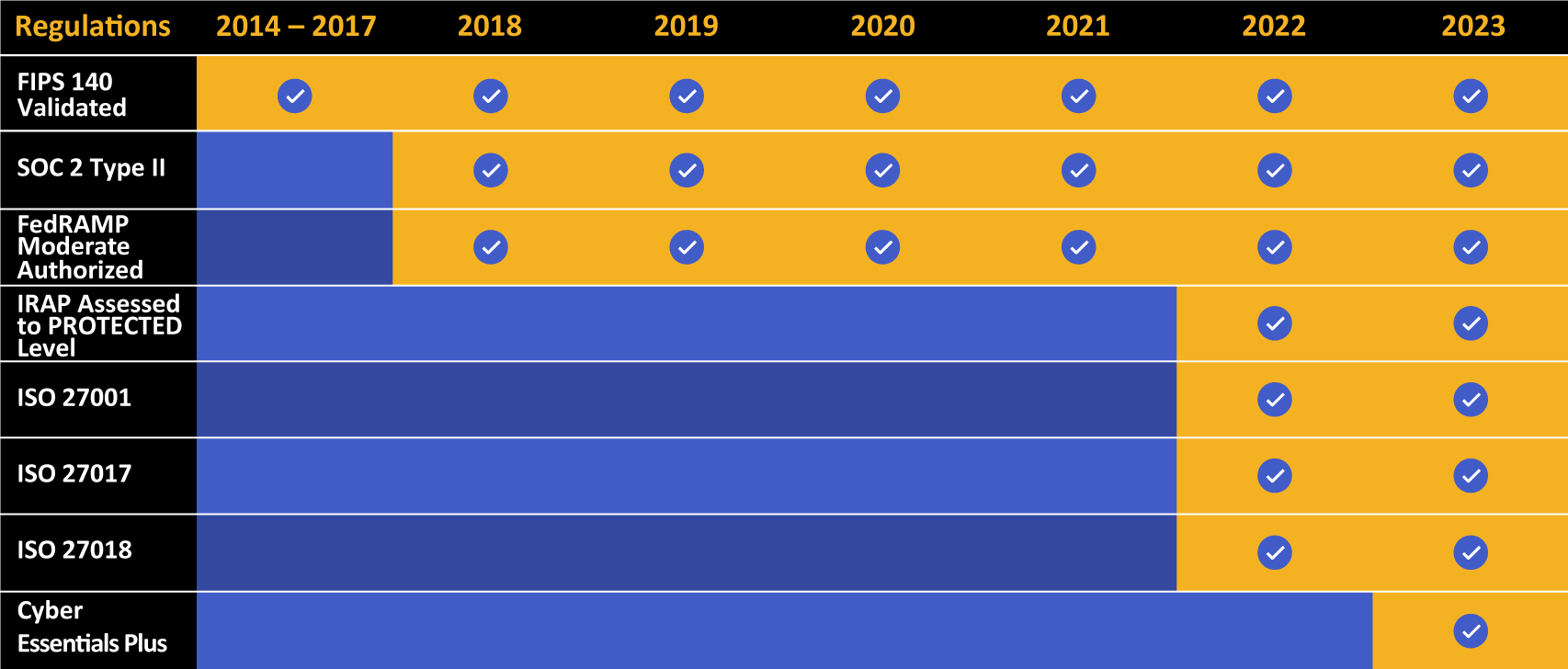
Kiteworks touts a long list of compliance and certification achievements.
All About FIPS 140-2
The FIPS 140-2 is a crucial certification for IT and cybersecurity professionals. It ensures that cryptographic modules meet the necessary security requirements for protecting sensitive information. To master FIPS 140-2, professionals need to have a deep understanding of encryption algorithms and their strengths. One such aspect is the difference between AES-128 and AES-256 encryption.
AES is a widely adopted encryption algorithm used to ensure the security of data and communications. The strength of AES encryption is determined by the length of the key used. AES-128 employs a 128-bit key, while AES-256 utilizes a 256-bit key, offering a higher level of security.
The larger key space provided by AES-256 makes it more resistant to brute-force attacks compared to AES-128. It’s worth noting that both AES-128 and AES-256 have been approved by the National Institute of Standards and Technology and are considered secure.
When implementing FIPS 140-2, it is crucial for IT and cybersecurity professionals to thoroughly assess their encryption requirements and the sensitivity of the data being protected. While AES-256 provides enhanced encryption, it may necessitate additional computational resources, potentially impacting system performance. Therefore, a comprehensive risk evaluation is imperative to strike the optimal balance between security and operational efficiency.
Key points
- FIPS 140-2 certification is essential for IT and cybersecurity professionals.
- AES-128 and AES-256 are encryption algorithms used to secure data.
- AES-256 provides a higher level of security due to its larger key size.
- Both AES-128 and AES-256 are approved by NIST.
- Choosing between AES-128 and AES-256 requires considering the trade-off between security and performance.
Unlocking the Power of FIPS 140-2: A Game Changer for Enterprise Security Across Industries
Having a solid understanding of FIPS (Federal Information Processing Standards) and achieving FIPS compliance can provide numerous advantages and benefits for cybersecurity professionals. FIPS compliance ensures that organizations adhere to rigorous security standards, specifically FIPS 140-2, which governs the use of cryptographic modules. By possessing technical knowledge about FIPS, CISOs, IT management executives, and cybersecurity compliance leaders can effectively implement and maintain robust security measures to protect sensitive data and systems. This knowledge empowers them to make informed decisions regarding encryption algorithms, key management, and secure communication protocols. Additionally, FIPS compliance enhances an organization’s reputation, instills trust among clients and partners, and helps mitigate the risk of data breaches and regulatory non-compliance. With a deep understanding of FIPS, cybersecurity professionals can confidently navigate the complex landscape of information security and safeguard their organization’s critical assets.
Implementing FIPS 140-2 for enhanced sustainability in healthcare cybersecurity
The implementation of FIPS 140-2, a critical security standard for cryptographic modules, is paramount in ensuring the sustainability of healthcare cybersecurity. By adhering to FIPS 140-2, which stands for Federal Information Processing Standard 140-2, healthcare organizations can effectively protect sensitive patient data and uphold the integrity of their systems.
Implementing FIPS 140-2 is crucial for healthcare organizations to ensure the highest level of security for their cryptographic modules. This standard provides comprehensive guidelines for designing, implementing, and testing cryptographic algorithms and modules, making them resilient against a wide range of attacks and vulnerabilities. By achieving FIPS 140-2 compliance, healthcare organizations can have complete confidence in the encryption methods employed to safeguard patient data, significantly mitigating the risk of unauthorized access and data breaches.
Streamline your FIPS 140-2 implementation for efficient corporate law and paralegal operations
Efficient corporate law and paralegal operations require a streamlined implementation of FIPS 140-2. This government standard sets the security requirements for cryptographic modules used in information systems, ensuring the confidentiality and integrity of sensitive data.
Implementing FIPS 140-2 requires careful consideration of various factors, and one crucial aspect is the utilization of AES-256 encryption. AES-256, an abbreviation for AES with a robust key size of 256 bits, is an extensively recognized and trusted encryption algorithm. It offers a superior level of security and holds the approval of the National Institute of Standards and Technology for safeguarding sensitive information.
Achieve seamless business and ecommerce operations with fully compliant FIPS
FIPS encryption is an absolute necessity for ensuring seamless business and ecommerce operations. It guarantees the utmost level of security for sensitive data, shielding it from any unauthorized access or potential breaches. By implementing FIPS encryption, organizations can effectively safeguard their data and maintain compliance with industry regulations.
FIPS encryption offers a range of significant advantages, with one standout benefit being its utilization of robust cryptographic algorithms. Take, for instance, AES-256, a widely recognized and highly secure encryption algorithm. AES-256 employs an impressive 256-bit key length, rendering unauthorized decryption of encrypted data an exceedingly challenging task for potential attackers.
Implementing fully compliant FIPS encryption is essential for businesses to securely transmit and store sensitive information. This includes customer data, financial records, and intellectual property. The organization’s reputation and customer trust rely on this level of security. By adopting FIPS encryption, businesses can effectively mitigate the risk of data breaches and potential financial losses.
FIPS encryption goes beyond just data protection. It ensures seamless interoperability and compatibility across diverse systems and platforms. This means that organizations can securely exchange data with their partners, suppliers, and customers, regardless of the systems they rely on. FIPS encryption establishes a standardized approach to data security, enabling uninterrupted collaboration and communication while upholding the highest level of protection.
Achieve superior FIPS compliance performance for your industrial manufacturing needs
Implementing AES-256 encryption is an essential step in achieving superior FIPS compliance performance for your industrial manufacturing needs. AES-256, also known as AES with a 256-bit key, is a widely recognized and trusted encryption algorithm that offers a robust level of security for safeguarding sensitive data.
Research indicates that AES-256 encryption is a robust security measure that safeguards your data from unauthorized access and potential cyber threats. This encryption method employs a symmetric key approach, where the same key is used for both encryption and decryption, ensuring efficiency and high-level security. By implementing AES-256 encryption, your industrial manufacturing operations can effectively meet the stringent FIPS compliance requirements, guaranteeing the confidentiality, integrity, and availability of your valuable data.
Unlocking the power of premium grade FIPS for enhanced government cybersecurity
Government agencies face unique cybersecurity challenges due to the sensitive nature of the data they handle. To tackle these challenges head-on, government agencies can leverage the immense power of premium-grade FIPS encryption. FIPS-compliant encryption algorithms, such as the highly regarded AES-256, offer an unparalleled level of security for safeguarding government data. Research indicates that AES-256 encryption stands as one of the most robust and secure encryption standards available today. By implementing AES-256 encryption, government agencies can fortify their security posture and protect their sensitive information with the utmost confidence.
When it comes to safeguarding sensitive data, premium-grade FIPS encryption stands out as a formidable defense mechanism. Its unparalleled ability to protect data at rest and in transit makes it an indispensable tool for organizations. By employing AES-256 encryption, data is shielded with a robust 256-bit key, rendering it virtually impenetrable to unauthorized access. This level of encryption ensures that even if data falls into the wrong hands, it remains secure and unintelligible. The implementation of premium-grade FIPS encryption empowers government agencies to fortify their cybersecurity posture and effectively mitigate the risk of data breaches.
Government agencies can benefit from the robust security features and compliance advantages of premium-grade FIPS encryption. Federal regulations mandate FIPS encryption standards, ensuring that agencies meet the necessary security requirements. By implementing FIPS-compliant encryption, government organizations can demonstrate their unwavering commitment to data protection and compliance. This not only fosters trust with citizens and stakeholders but also guarantees the utmost security of sensitive government information.
Easily customize FIPS for enhanced banking and finance security
FIPS is a crucial set of security standards established by the National Institute of Standards and Technology. Its primary objective is to safeguard sensitive information within federal computer systems. In the banking and finance industry, where data security holds paramount importance, organizations can effortlessly tailor FIPS to fortify their existing security measures.
Implementing AES-256 encryption is a crucial step towards achieving robust security. This widely recognized and trusted encryption algorithm ensures that your data remains protected by utilizing a 256-bit key. With AES-256 encryption, unauthorized individuals face an arduous challenge when attempting to access or decipher your encrypted information.
By incorporating AES-256 encryption into the FIPS, banking and finance institutions can significantly enhance their security posture and fortify the protection of sensitive financial data. This robust level of encryption acts as an impenetrable shield against potential threats, including data breaches and unauthorized access, thereby ensuring the utmost security and confidentiality of customer information.
Key FIPS Compliance Features and Technical Specifications for Enhanced Security
Ensuring compliance with FIPS is of utmost importance for organizations entrusted with sensitive data and seeking to bolster their security measures. It is imperative to consider a range of key features and technical specifications pertaining to FIPS compliance:
1. Robust Encryption: To ensure the highest level of data security, it is imperative to adhere to FIPS compliance standards. This entails utilizing approved encryption algorithms, such as AES and RSA (Rivest-Shamir-Adleman). These algorithms offer unparalleled protection for data both at rest and in transit, guaranteeing utmost confidentiality and integrity.
2. Secure Key Management: Compliance with the FIPS is crucial for ensuring robust key management practices. It is imperative to generate and store encryption keys securely, safeguarding them against unauthorized access or disclosure. To maintain the integrity of encrypted data, organizations must implement key rotation and revocation processes.
3. Physical Security: FIPS compliance goes beyond just digital security and encompasses physical security as well. It is imperative for organizations to implement robust measures to safeguard the hardware and infrastructure that store or process sensitive data. This entails the establishment of highly secure data centers, stringent access controls, comprehensive video surveillance systems, and advanced environmental controls to prevent any unauthorized physical access or tampering attempts.
4. Audit and Monitoring: To achieve FIPS compliance, organizations must establish robust audit and monitoring capabilities. This entails logging and analyzing security events, promptly detecting and responding to security incidents, and generating comprehensive audit reports. By implementing these measures, organizations can effectively identify and mitigate security risks, ensuring uninterrupted adherence to FIPS standards.
5. Robust Authentication: FIPS compliance places a strong emphasis on implementing secure authentication mechanisms. This entails leveraging multi-factor authentication (MFA) alongside the utilization of cryptographic tokens or smart cards. By adopting these measures, organizations can significantly bolster the security of user access and fortify their defenses against unauthorized entry to sensitive data.
Implementing these critical FIPS compliance features and technical specifications is paramount for organizations to fortify their security posture and safeguard sensitive data. Staying abreast of the latest FIPS standards and conducting regular compliance assessments are imperative measures to mitigate security risks.
Uncovering FIPS Challenges: Navigating Non-Compliant Protocols in Cybersecurity
FIPS 140-2 compliance is an essential requirement for cryptographic modules used in the realm of cybersecurity. However, there is significant controversy surrounding this standard due to the intricate challenges associated with navigating non-compliant protocols. One of the primary concerns revolves around the utilization of non-approved algorithms or cryptographic techniques that fail to meet the stringent FIPS 140-2 requirements.
Implementing non-compliant protocols can introduce significant vulnerabilities and severely weaken an organization’s overall security posture. These protocols often lack the necessary safeguards and rigorous testing mandated by FIPS 140-2, making them highly susceptible to attacks and compromising sensitive data.
One of the key obstacles when dealing with non-compliant protocols is the potential for encountering interoperability issues. When different systems or devices utilize incompatible cryptographic algorithms or protocols, it can severely impede secure communication and data exchange. This, in turn, can result in operational inefficiencies and significantly heighten the risk of data breaches.
It is imperative for organizations to conduct a thorough assessment of the risks associated with non-compliant protocols. This critical step involves identifying vulnerabilities through comprehensive security assessments and implementing appropriate remediation measures. In some cases, organizations may need to replace or update cryptographic modules to ensure compliance with the stringent FIPS 140-2 standards.
Unlocking Key Compliance Advantages with FIPS 140-2 for Enhanced Cybersecurity
When CISOs, IT management professionals, CIOs, cybersecurity risk management engineers, and user privacy compliance leaders of enterprise-level organizations in various industry sectors possess a deep understanding of the advantages of complying with data security standards and user privacy regulations, they gain a significant edge in safeguarding their organizations’ sensitive information. By leveraging their enhanced technical knowledge, these professionals can effectively implement robust cybersecurity measures, mitigate risks, and ensure regulatory compliance.
Staying informed about the latest industry trends and best practices allows these professionals to proactively identify vulnerabilities, develop comprehensive security strategies, and protect their organizations from potential data breaches and privacy violations. This technical expertise empowers them to make informed decisions, allocate resources efficiently, and maintain a strong security posture in an ever-evolving threat landscape.
Affordable FIPS 140-2 solutions for enhancing security in healthcare facilities
Healthcare facilities face a myriad of unique challenges in safeguarding the security of sensitive patient data. The healthcare industry is increasingly targeted by a growing number of cyber threats, making it imperative for these facilities to implement robust security measures. One highly effective solution for bolstering security in healthcare facilities is the adoption of affordable solutions that comply with the FIPS 140-2.
The National Institute of Standards and Technology has developed a standard known as FIPS 140-2. This standard outlines the security requirements for cryptographic modules, which play a crucial role in encrypting and decrypting sensitive data. By adhering to FIPS 140-2 compliant solutions, healthcare facilities can ensure the protection of their data using industry-recognized encryption algorithms like AES-256.
AES-256 encryption, also referred to as the AES with a robust key size of 256 bits, stands as one of the most formidable encryption algorithms available today. Renowned for its exceptional security capabilities, it offers an elevated level of defense against unauthorized access and potential data breaches. By incorporating AES-256 encryption into their security solutions, healthcare facilities can significantly fortify the protection of their sensitive patient data.
Moreover, healthcare facilities can benefit from the implementation of affordable FIPS 140-2 solutions, which provide a cost-effective means to meet regulatory compliance requirements. It is crucial for healthcare organizations to adhere to regulations such as the Health Insurance Portability and Accountability Act in order to avoid penalties and maintain the trust of their patients. By incorporating FIPS 140-2 compliant solutions, healthcare facilities can effectively showcase their dedication to data security and compliance.
Fast and efficient FIPS compliance scalability for US government and contractors
The importance of rapid and effective scalability for FIPS compliance cannot be overstated, particularly for government agencies and contractors in the United States. FIPS compliance, which stands for FIPS, plays a critical role in safeguarding sensitive information and ensuring its security. One key element of FIPS compliance revolves around AES-256 encryption, a widely recognized and secure encryption standard.
AES-256 encryption, also referred to as the AES with a robust key size of 256 bits, offers an exceptional level of security for safeguarding data both at rest and in transit. This encryption standard has received the seal of approval from the National Institute of Standards and Technology and is extensively utilized by government agencies and contractors to fortify the protection of highly sensitive information.
Ensuring the utmost protection of systems and data is paramount for government agencies and contractors. By leveraging fast and efficient FIPS compliance scalability, they can achieve this goal without compromise. This remarkable scalability empowers them to encrypt and decrypt substantial volumes of data, all while maintaining optimal performance and unwavering security.
Implementing robust and highly scalable FIPS compliance measures is crucial for government agencies and contractors. It enables them to meet the stringent security requirements mandated by regulatory bodies, ensuring the utmost protection and confidentiality of sensitive information. By doing so, unauthorized access is effectively prevented, providing peace of mind for both the government and its contractors.
Simplifying FIPS 140-2 compliance for businesses and ecommerce success
FIPS 140-2 compliance is an absolute necessity for businesses and e-commerce to thrive in the digital landscape. This critical standard ensures that cryptographic modules utilized to safeguard sensitive information adhere to the most stringent security protocols. A key component of FIPS 140-2 compliance lies in the implementation of AES-256 encryption, which offers unparalleled protection against unauthorized access and potential data breaches.
AES-256 encryption, also referred to as the AES with a 256-bit key length, stands as one of the most robust encryption algorithms available today. Its unparalleled security has gained recognition from the National Institute of Standards and Technology, making it the preferred choice for government agencies, financial institutions, and businesses worldwide.
Implementing AES-256 encryption can be a daunting task, requiring significant time and expertise, especially for businesses that lack familiarity with cryptographic standards. However, there are robust solutions available that streamline FIPS 140-2 compliance, empowering businesses to achieve e-commerce success while upholding uncompromising security measures.
One effective solution for meeting FIPS 140-2 requirements is the implementation of encryption software specifically designed for this purpose. These software solutions offer a user-friendly interface and streamline the encryption process, enabling businesses to easily achieve and maintain compliance. By leveraging these solutions, organizations can safeguard their sensitive data while reducing the compliance burden.
When it comes to safeguarding sensitive data, encryption software is just the tip of the iceberg. To truly fortify their defenses, businesses should consider partnering with cybersecurity experts who specialize in FIPS 140-2 compliance. These seasoned professionals possess the knowledge and experience to guide organizations through the intricate compliance process, ensuring that their encryption systems meet the stringent standards.
Enhancing global industrial supply with stable FIPS for manufacturers and distributors
Manufacturers and distributors recognize the utmost importance of enhancing global industrial supply chains. In order to achieve this, it is imperative to prioritize stable compliance with the FIPS. FIPS ensures that cryptographic algorithms utilized for data protection meet rigorous security requirements, guaranteeing the utmost protection for sensitive information.
AES-256 encryption, also referred to as AES with a 256-bit key, is widely acknowledged as one of the most robust encryption methods available today. It employs a symmetric key algorithm, which means that the same key is used for both encryption and decryption processes. This ensures that only authorized individuals possessing the correct key can gain access to the encrypted data, thereby establishing a formidable barrier against unauthorized intrusion.
When it comes to securing sensitive data in a global supply chain, manufacturers and distributors can rely on the robust protection offered by AES-256 encryption. This advanced encryption algorithm plays a crucial role in safeguarding critical information, including intellectual property, customer data, and financial records. By implementing AES-256 encryption, organizations can ensure the confidentiality and integrity of their data, especially when sharing it with partners, suppliers, and customers across different geographical locations.
First and foremost, the implementation of AES-256 encryption plays a crucial role in meeting stringent compliance requirements, particularly in industries governed by rigorous data protection regulations. By adopting FIPS-compliant encryption, manufacturers and distributors can effectively showcase their unwavering dedication to safeguarding sensitive information, mitigating potential legal liabilities, and preserving their hard-earned reputation.
Boost your bank’s efficiency with customizable FIPS 140-2 workflow solutions
Efficiency is a paramount concern for banks operating in today’s rapidly evolving digital landscape. To achieve this, banks can implement customizable workflow solutions that adhere to the FIPS 140-2 (FIPS 140-2). FIPS 140-2 is a security standard that ensures cryptographic modules meet specific requirements for safeguarding sensitive information. By leveraging FIPS 140-2 compliant solutions, banks can bolster their security posture and streamline their operations.
Customizable FIPS 140-2 workflow solutions empower banks to tailor their security protocols, ensuring they meet their unique requirements. These solutions offer a comprehensive range of features, including the highly trusted AES-256 encryption algorithm. By leveraging AES-256 encryption, data transmission and storage are fortified, safeguarding against unauthorized access. Banks can seamlessly configure encryption settings, access controls, and other security measures within these customizable workflow solutions, aligning them precisely with their specific needs.
Implementing customizable workflow solutions that comply with the FIPS 140-2 can revolutionize a bank’s operations, enhancing efficiency through automated and streamlined processes. These solutions empower banks to establish standardized workflows, minimizing the need for manual intervention and reducing the risk of human error. By automating critical tasks like secure file transfers, document approvals, and compliance checks, banks can optimize their time and resources, enabling employees to focus on strategic initiatives. Moreover, these customizable workflow solutions offer real-time visibility into process statuses, facilitating informed decision-making and expediting response times.
Moreover, banks can effectively address regulatory compliance requirements by leveraging highly customizable FIPS 140-2 workflow solutions. The protection of customer data and the preservation of trust are paramount for banks, necessitating adherence to industry standards and regulations such as the Payment Card Industry Data Security Standard (PCI DSS) and the GDPR. FIPS 140-2 compliant solutions offer the essential security controls and encryption capabilities needed to fulfill these requirements, ensuring the safeguarding of sensitive information and the maintenance of privacy.
Effortless FIPS solutions for efficient law firms and paralegal services
Effortless FIPS Solutions for Efficient Law Firms and Paralegal Services
Securing sensitive data efficiently is of utmost importance for law firms and paralegal services. It is crucial to protect client confidentiality and comply with industry regulations. One highly effective solution to achieve this is the implementation of encryption that is compliant with the FIPS. FIPS 140-2, a widely recognized standard, ensures the security of cryptographic modules used for encryption. By adopting FIPS-compliant encryption, law firms and paralegal services can significantly enhance their data protection measures and effectively mitigate the risk of unauthorized access or data breaches.
FIPS-compliant encryption offers a crucial advantage: compatibility with the highly secure AES-256 encryption. AES-256, a widely used symmetric encryption algorithm, ensures a robust defense against brute-force attacks and unauthorized decryption attempts. This level of security is particularly valuable in industries such as the legal sector, where confidentiality is paramount.
By leveraging the power of AES-256 encryption within a FIPS-compliant framework, law firms and paralegal services can safeguard the confidentiality and integrity of their sensitive data. This encryption standard provides a strong shield against potential threats, ensuring that unauthorized individuals cannot access or decipher the protected information.
Implementing FIPS solutions effortlessly can be accomplished by leveraging encryption software that fully supports FIPS 140-2 compliance. This robust software empowers law firms and paralegal services to seamlessly integrate FIPS-compliant encryption into their existing workflows and systems. By offering user-friendly interfaces and intuitive controls, these solutions streamline the encryption process, enabling legal professionals to prioritize their core tasks while upholding data security.
FIPS solutions go beyond just data encryption. They encompass a range of security measures, including access controls, authentication mechanisms, and secure storage. These comprehensive solutions take a layered approach to data protection, ensuring that sensitive information remains secure throughout its entire lifecycle. By implementing FIPS-compliant solutions, law firms and paralegal services can demonstrate their unwavering commitment to safeguarding client data and maintaining compliance with industry regulations.
The adoption of FIPS-compliant encryption solutions, particularly those supporting AES-256 encryption, presents a seamless way for law firms and paralegal services to bolster data security and safeguard sensitive information. By leveraging FIPS 140-2 compliant encryption software, legal professionals can effortlessly integrate robust encryption measures into their workflows, ensuring the confidentiality and integrity of client data. With comprehensive security features and user-friendly interfaces, FIPS solutions offer an efficient and effective means of fortifying sensitive data protection in the legal sector.
Essential Business Cybersecurity Statistics: A Must-Read for IT Professionals and CISOs
Understanding the implications of cybersecurity compliance and risk management strategy is vital for enterprise-level organizations across various industry sectors. By closely monitoring and analyzing relevant statistics, organizations can gain valuable insights into data security, risk management, and compliance of sensitive content communications.
-
According to the Sensitive Content Communications Privacy and Compliance Report for 2023 by Kiteworks, a staggering 90% of large enterprises engage in the sharing of sensitive content with over 1,000 third parties. Moreover, an overwhelming 90% of organizations utilize four or more channels to transmit this sensitive information. The report draws its insights from a comprehensive global survey conducted among IT, cybersecurity, and compliance professionals hailing from enterprise-level organizations. The respondents represent a diverse array of industries, geographies, and job grades.
-
One striking finding from the report is that a significant number of organizations still have a considerable distance to cover when it comes to fortifying their security efforts around sensitive content communications. Merely a quarter of the survey respondents express confidence in their security measurement and management practices being up to par. Similarly, a comparable percentage of participants have successfully aligned their corporate risk management strategy with the measurement and management of sensitive content security. These results underscore the substantial amount of work that lies ahead for the majority of organizations.
-
The report also emphasizes the significant risks associated with different communication channels. While traditional concerns such as email, file sharing, and file transfer systems remain prominent, it is crucial to acknowledge the emerging channels like mobile apps, texting, and APIs (application programming interfaces) as potential sources of risk. Moreover, organizations must comply with data privacy regulations and industry standards, especially considering that 99% of respondents engage in business with government entities. This necessitates adherence to special requirements for securely sharing private data and sensitive content.
For a comprehensive understanding of the subject matter, we highly recommend reviewing Kiteworks’ Sensitive Content Communications Privacy and Compliance Report.
Mastering FIPS Workflows: Essential Industry Standards for Optimal Cybersecurity
Implementing and understanding FIPS workflows is an essential element in maintaining a robust cybersecurity framework within any organization. These industry standards, developed by the U.S. federal government, are specifically designed to ensure the utmost security and integrity of information processed by computer systems. By mastering FIPS workflows, organizations can significantly bolster their cybersecurity posture, effectively reducing vulnerabilities, mitigating risks, and ensuring compliance with stringent regulatory requirements.
One of the primary advantages of FIPS workflows lies in their comprehensive approach to cybersecurity. These workflows encompass a wide array of critical areas, such as cryptographic modules, secure network communications, and data protection. By adopting this holistic approach, organizations can effectively address potential security gaps and establish a robust defense against a diverse range of cyber threats. Additionally, FIPS workflows remain consistently updated to align with the ever-evolving cybersecurity landscape, ensuring that enterprises are constantly prepared to combat the latest threats.
Mastering FIPS workflows is a complex and challenging endeavor. It requires a deep understanding of the standards and the ability to effectively implement them within the intricate organizational landscape. This is where the invaluable guidance of cybersecurity experts comes into play. By leveraging their knowledge and experience, organizations can navigate the intricate complexities of FIPS workflows, ensuring optimal security and compliance. In the realm of cybersecurity, knowledge is power, and the mastery of FIPS workflows serves as a formidable weapon against cyber threats.
Kiteworks Private Content Network for FIPS 140-2
Streamlining data transfer methods and ensuring security is a critical priority for enterprise-level organizations. The Private Content Network provides a comprehensive solution by integrating multiple functionalities onto a single platform. This includes email, file sharing, web forms, and MFT. By consolidating these capabilities, organizations can enhance control, protection, and visibility of all incoming and outgoing files. This robust approach to data management empowers CISOs, IT management executives, CIOs, and cybersecurity risk management and data security compliance leaders to maintain the highest levels of security and compliance.
Discover the unparalleled capabilities of Kiteworks—a robust solution that empowers you to take full control of your sensitive content. With Kiteworks, you have the authority to regulate access, ensuring that only authorized individuals can gain entry. But it doesn’t stop there. Kiteworks goes above and beyond by providing automated end-to-end encryption and multi-factor authentication when sharing your content externally. Seamlessly integrating with your existing security infrastructure, Kiteworks fortifies your defenses, offering an additional layer of protection.
One of the standout features of Kiteworks is its ability to provide complete visibility into all file activity. You can effortlessly monitor and report who is sending what, to whom, when, and how. This level of transparency allows you to stay on top of your content, ensuring compliance and mitigating any potential risks.
Experience the power of Kiteworks, where you’re not just managing your content—you’re mastering it.
Take advantage of the peace of mind that comes from aligning with critical regulations and standards. Navigate the intricacies of GDPR, confidently meet the stringent requirements of HIPAA, and ensure preparedness for CMMC. Additionally, achieve the robust security standards of Cyber Essentials Plus and fulfill the rigorous criteria of IRAP. These are just a few examples of the numerous regulatory frameworks that can be mastered with the right approach and resources.
Experience the true power of a Kiteworks-enabled Private Content Network and unlock its full potential. Don’t miss out on this exclusive opportunity—take the first step and book a custom demo today.
FAQs About FIPS Compliance
Knowing the answers to these questions can provide helpful benefits to US businesses. First, understanding the best practices for FIPS compliance ensures that businesses can implement the necessary security measures to protect sensitive data and maintain regulatory compliance. Second, adhering to FIPS standards helps businesses avoid penalties, such as fines and legal consequences, which can have a significant impact on their reputation and financial stability. Third, taking proactive steps to ensure compliance with FIPS standards allows businesses to mitigate the risk of data breaches and cyberattacks, safeguarding their assets and customer trust. Fourth, leveraging available resources, such as official documentation and guidance, helps businesses gain a comprehensive understanding of the requirements for FIPS compliance and stay up to date with any changes or updates. Finally, non-compliance with FIPS can have serious implications, including reputational damage, loss of customer trust, and potential legal liabilities, underscoring the importance of prioritizing FIPS compliance efforts.
What best practices should US businesses follow to ensure FIPS compliance?
FIPS is absolutely essential for US businesses to guarantee the utmost security and integrity of their sensitive data. In order to achieve FIPS compliance, businesses must adhere to a number of critical best practices, including: Implementing strong encryption algorithms and protocols to protect data at rest and in transit, such as using FIPS-approved cryptographic modules and algorithms; Establishing strict access controls and authentication mechanisms to ensure only authorized individuals can access sensitive information, such as implementing multi-factor authentication and role-based access controls; Regularly conducting vulnerability assessments and penetration testing to identify and address any security weaknesses or vulnerabilities in the system; and Maintaining comprehensive documentation and records of security policies, procedures, and incident response plans to demonstrate compliance with FIPS requirements.
What penalties do US businesses face if they do not adhere to FIPS?
US businesses that fail to comply with FIPS face severe penalties. Organizations are warned that non-compliance with FIPS standards can lead to legal repercussions, financial losses, and damage to reputation. Such organizations may be subject to fines, legal action, and regulatory scrutiny from government agencies like the National Institute of Standards and Technology and the Federal Trade Commission (FTC). Moreover, non-compliant businesses may suffer data breaches, erosion of customer trust, and potential disruptions to their operations. Prioritizing FIPS compliance is crucial for organizations to mitigate these risks and safeguard the security of their sensitive data.
What steps can US businesses take to ensure compliance with FIPS?
FIPS represent these crucial security standards established by the esteemed National Institute of Standards and Technology, whose primary objective is to safeguard sensitive information within federal agencies and businesses: Implement strong access controls and authentication mechanisms, such as multi-factor authentication, to prevent unauthorized access to sensitive data; Encrypt data at rest and in transit using approved cryptographic algorithms and protocols, ensuring the confidentiality and integrity of information; Regularly update and patch systems and software to address vulnerabilities and protect against known security threats; and Conduct regular security assessments and audits to identify and address any non-compliance issues, ensuring continuous monitoring and improvement of security controls.
What resources can US businesses use to understand the requirements for FIPS compliance?
US businesses should familiarize themselves with FIPS to ensure compliance. FIPS publications offer detailed guidelines and standards for various aspects of information security, such as encryption algorithms, cryptographic modules, and security requirements for federal systems. The National Institute of Standards and Technology is responsible for developing and maintaining these standards, with NIST Special Publication 800-53 providing a comprehensive set of security controls and guidelines for federal information systems. Additionally, NIST Special Publication 800-171 outlines the requirements for protecting controlled unclassified information (CUI) in nonfederal systems. These publications serve as invaluable resources for US businesses aiming to achieve FIPS compliance and bolster their cybersecurity posture.
What implications do US businesses face if they do not comply with FIPS?
If US businesses fail to comply with FIPS, they will face significant implications. Initially, non-compliance with FIPS can lead to severe legal consequences, including substantial fines and penalties. Moreover, businesses risk losing the trust and confidence of their customers, partners, and stakeholders, resulting in substantial reputational damage. Additionally, non-compliance leaves businesses vulnerable to cyber threats and attacks since FIPS provides essential guidelines and standards for securing sensitive information. Lastly, failure to adhere to FIPS may hinder business opportunities, as many government contracts and partnerships require strict adherence to these standards. Therefore, it is imperative for US businesses to prioritize FIPS compliance to mitigate these potential risks and ensure the security and integrity of their operations.
Additional Resources
- Brief: Kiteworks Hardened Virtual Appliance
- Case Study: Mandiant Uses Kiteworks to Protect the Sensitive Content That Helps Protect Businesses Worldwide
- Top 5: Top 5 Ways Kiteworks Secures Microsoft 365 Third-party Communications
- Brief: Achieve Zero Trust Security with Kiteworks: A Comprehensive Approach to Data Protection
- Webinar: How Automated Email Encryption Delivers Improved Privacy Protection and Compliance


