
FedRAMP: The Short Path to Secure Content Communications
The Federal Risk and Authorization Management Program (FedRAMP) is a government-wide program that standardizes the approach to security assessments, authorization, and continuous monitoring for cloud products and services. As sensitive content communication becomes increasingly critical in today’s risk environment, understanding FedRAMP’s role and importance in ensuring secure and compliant communication is essential. In this comprehensive blog post, we will discuss FedRAMP in detail, highlighting its key components, benefits, and the steps organizations must take to achieve compliance.
Understanding FedRAMP and Its Role in Secure Content Communications
FedRAMP is a crucial program designed to provide a standardized approach to security for cloud services used by federal agencies. In an era where the exchange of sensitive information through email, file attachments, and other online means is common, ensuring the security and privacy of such content is paramount. FedRAMP helps achieve this by providing a framework for federal agencies and cloud service providers (CSPs) to follow, ensuring the security measures to protect sensitive content during communication.
FedRAMP, however, isn’t just for cloud service providers who currently work with, or hope to work with, the federal government. Private sector businesses are increasingly turning to FedRAMP authorized cloud storage providers for their file sharing needs because these solutions offer a higher level of security, compliance, and accountability. A FedRAMP authorized CSP undergoes strict security assessments and certifications to ensure that their infrastructure and operational controls are up to par with government standards. This includes continuous monitoring and regular security updates to mitigate potential risks and threats. In terms of compliance, a FedRAMP authorized cloud storage provider adheres to strict regulations and standards, such as HIPAA, FISMA, and NIST, to protect sensitive and confidential information. This ensures that private sector businesses can trust that their data is being handled in a compliant and legally accepted manner. Moreover, FedRAMP authorized cloud storage providers offer a high level of accountability, as they are required to report any security incidents or breaches promptly. This means that businesses can have peace of mind, knowing that their data is being closely monitored and any issues will be addressed quickly and efficiently.
The Essential Components of the FedRAMP Framework
The FedRAMP framework comprises several essential components that provide a standardized approach to security assessment, authorization, and continuous monitoring for cloud services. These components help ensure that federal agencies can securely adopt cloud services while maintaining compliance with federal regulations and protecting sensitive content, including federal contract information (FCI) and controlled unclassified information (CUI).
Security Assessment Framework
The Security Assessment Framework is a structured process that evaluates the security posture of a cloud service, ensuring that it meets the requirements of the selected FedRAMP authorization level. This process includes assessing security controls, documentation, and ongoing monitoring activities to maintain a secure environment and identify potential security risks.
Standardized Security Controls: FedRAMP and NIST CSF
FedRAMP adopts standardized security controls from the National Institute of Standards and Technology Special Publication 800-53 (NIST SP 800-53). These controls are tailored to address the risks associated with cloud services and are categorized into Low, Moderate, and High impact levels, in accordance with the three different FedRAMP authorization levels.
Third Party Assessor Organizations (3PAOs)
Third Party Assessor Organizations, or 3PAOs, are independent entities accredited by FedRAMP to perform security assessments of cloud service providers. Third Party Assessor Organizations evaluate the implementation and effectiveness of security controls, review documentation, and provide recommendations for authorization based on their findings. They play a crucial role in the FedRAMP framework, ensuring an unbiased and thorough evaluation of the cloud service’s security posture.
Evaluating Security Controls and Implementation
3PAOs are responsible for evaluating the implementation and effectiveness of a cloud service provider’s security controls. They assess the measures to protect sensitive information and ensure compliance with the specific requirements of the FedRAMP authorization level.
Reviewing Documentation Provided by CSP
As part of the assessment process, 3PAOs review the documentation provided by the cloud service provider, which includes policies, procedures, and other relevant information related to implementing security controls. This ensures that the CSP’s security posture is well-documented and follows the FedRAMP guidelines.
Providing Recommendations for Authorization
Upon completing the security assessment, 3PAOs provide recommendations to federal agencies regarding the authorization of the cloud service. Their findings help determine whether the CSP meets the necessary security requirements and should be granted an Authority to Operate (ATO).
Maintaining Accreditation and Compliance
3PAOs must maintain their accreditation with FedRAMP to continue conducting security assessments. This involves adhering to strict standards and guidelines set by FedRAMP, ensuring that 3PAOs maintain a high level of expertise and professionalism in their assessment activities.
Authorization Packages
Authorization packages are comprehensive documentation prepared by the cloud service provider and 3PAO, detailing the cloud service’s security controls, policies, and procedures. Federal agencies review these packages to determine whether to grant an ATO for the cloud service, allowing it to be used by the agency.
Continuous Monitoring Program
The Continuous Monitoring Program is an essential component of the FedRAMP framework that ensures authorized cloud services’ ongoing security and compliance. This program requires cloud service providers to regularly update their security documentation, perform vulnerability scanning, and report any security incidents. This proactive approach helps identify potential security risks and maintain a high level of security for cloud services used by federal agencies.
What Is FedRAMP Compliance?
Achieving and maintaining FedRAMP compliance, or authorization, is a necessary and systematic process for cloud service providers aiming to serve federal agencies. This process ensures that CSPs adhere to the stringent security requirements laid out by the FedRAMP framework. The steps toward compliance include preparing and documenting the necessary policies, procedures, and security controls; engaging a Third Party Assessor Organization for an independent security assessment; submitting an authorization package for review by the FedRAMP Program Management Office or the relevant federal agency; obtaining an Authority to Operate after a successful review; and continuously monitoring and maintaining security controls to ensure ongoing compliance. By following these steps, CSPs can demonstrate their commitment to providing secure cloud services and fostering trust with their government clients.
Benefits of FedRAMP for Federal Agencies and Cloud Service Providers
FedRAMP compliance provides numerous advantages for federal agencies and cloud service providers (CSPs) alike. By adhering to this standardized framework, both parties know the FCI and CUI shared and stored remains confidential.
Some of the critical benefits of FedRAMP compliance include:
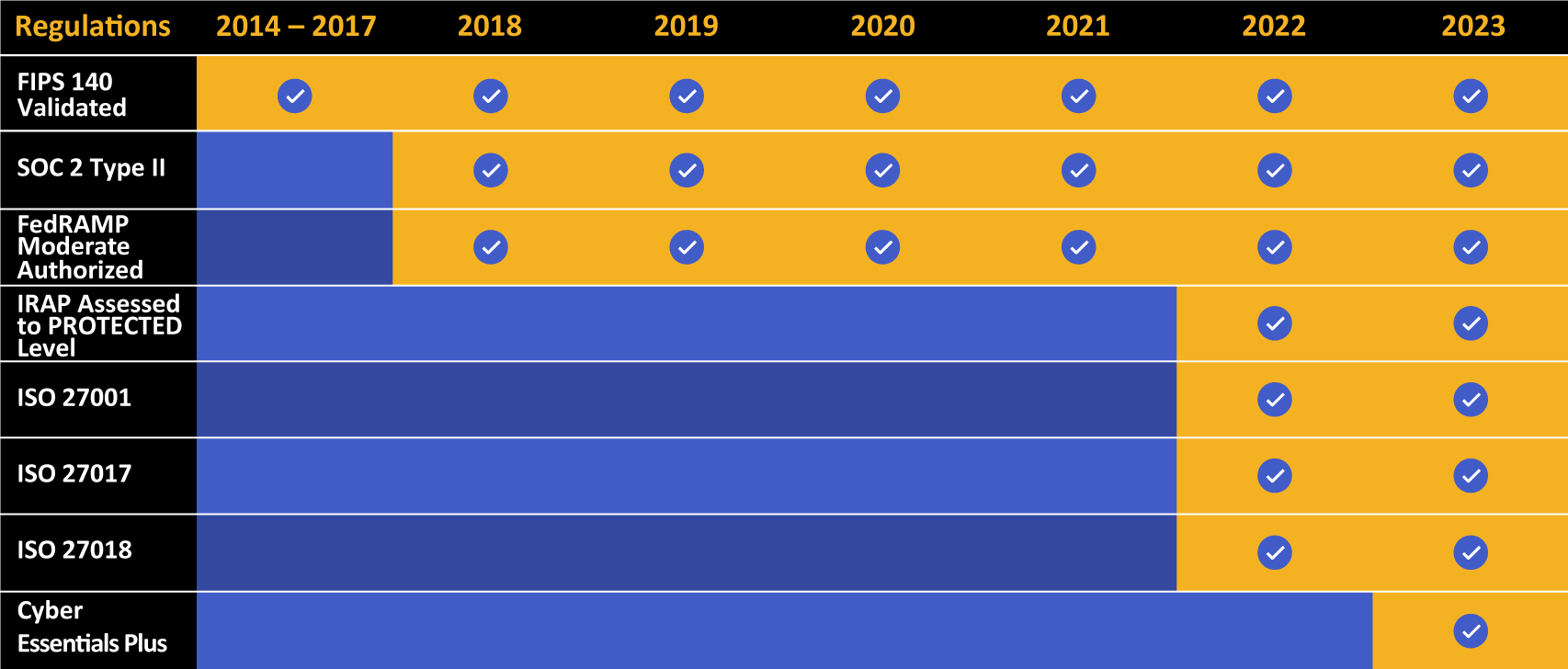
Kiteworks touts a long list of compliance and certification achievements.
Consistency in Security Assessments and Authorization
FedRAMP provides a consistent and standardized approach to security assessments and authorization for cloud services. This eliminates the need for individual agencies to conduct their inspections, saving time and resources and ensuring consistent security across all agencies.
Reduced Duplication of Efforts
Federal agencies can avoid duplicating efforts when assessing and authorizing cloud services using a standardized approach. This ensures that resources are used efficiently and reduces the likelihood of inconsistencies in security evaluations.
Cost Reduction Resulting From Secure File Sharing
The “do once, use many times” philosophy behind FedRAMP allows CSPs to undergo a single security assessment that multiple federal agencies can reuse. This reduces the overall cost of security assessments and enables secure file sharing between agencies and CSPs, resulting in cost savings for both parties.
Efficient Resource Allocation
The cost savings achieved through FedRAMP’s streamlined process enables federal agencies to allocate their resources more efficiently, focusing on mission-critical tasks and projects while ensuring the secure adoption of cloud services.
Enhanced Data Security and Privacy
By adhering to the stringent security controls outlined in the FedRAMP framework, CSPs can provide FCI and CUI security and privacy to federal agencies. This reduces the risk of data breaches and ensures the secure exchange of sensitive content between agencies and CSPs, such as emails and file attachments.
Reduced Security Risks
With enhanced data security and privacy measures, agencies can minimize the potential risks associated with data breaches and unauthorized access, safeguarding sensitive information and maintaining compliance with data protection regulations.
Increased Trust and Confidence in Cloud Services
FedRAMP authorization serves as a stamp of approval for CSPs, signifying that their cloud services meet the rigorous security standards federal agencies require. This increases trust and confidence in the cloud services offered by these providers, making it easier for agencies to adopt and leverage cloud-based solutions for their operations.
Facilitated Cloud Adoption
As trust in cloud services grows, federal agencies are more likely to adopt and implement cloud-based solutions, increasing operational efficiency, scalability, and cost savings.
Streamlined Vendor Selection and Procurement
With a centralized repository of authorized CSPs, federal agencies can quickly identify and select cloud service providers that meet their security requirements. This streamlines the vendor selection process and simplifies procurement, ensuring agencies can access secure and compliant cloud services.
Efficient Decision-making
The centralized repository of authorized CSPs enables agencies to make informed decisions when selecting cloud service providers, reducing the time spent evaluating and comparing potential vendors and ensuring a faster procurement process.
Navigating the FedRAMP Authorization Process
Achieving FedRAMP compliance is a multi-step process that requires CSPs to adhere to stringent security requirements. The following steps outline the path to FedRAMP authorization:
Step 1: Preparation and Documentation
A CSP must develop a comprehensive documentation set, including a System Security Plan (SSP), detailing how their cloud service meets the security controls outlined in the FedRAMP framework. This documentation is the foundation for the security assessment process and demonstrates the CSP’s commitment to maintaining a secure environment for sensitive content communication.
Step 2: Security Assessment and Testing
Once the documentation is complete, the CSP must undergo a thorough security assessment conducted by a FedRAMP-approved Third Party Assessor Organization (3PAO). The 3PAO will evaluate the CSP’s security controls and create a Security Assessment Report (SAR) that documents the findings.
Step 3: Review and Authorization
The Joint Authorization Board (JAB), consisting of representatives from the Department of Defense (DoD), Department of Homeland Security (DHS), and General Services Administration (GSA), reviews the CSP’s documentation and SAR. Suppose the JAB determines that the cloud service meets the necessary security requirements. In that case, they will grant an Authorization to Operate (ATO), signifying that the cloud service complies with FedRAMP standards and can be used by federal agencies.
Step 4: Continuous Monitoring and Maintenance
Once a CSP has achieved FedRAMP authorization, it must continually monitor its security posture to ensure ongoing compliance. This includes regular security assessments, updates to security documentation, and prompt reporting of any security incidents to the appropriate federal agencies.
Key FedRAMP Authorization Considerations for Federal Agencies and CSPs
Both federal agencies and CSPs must consider several factors when navigating the FedRAMP authorization landscape. These include:
Understanding the Different Levels of FedRAMP Authorization
FedRAMP offers three levels of authorization based on the sensitivity of the data being processed, stored, or transmitted by a cloud service. Each class has specific security requirements and controls tailored to address the risks of handling different data types.
FedRAMP Low: Basic Security Controls for Low-impact Data
FedRAMP Low is designed for cloud services that handle low-impact data, defined as data that poses minimal risk to an organization if compromised. These cloud services must implement basic security controls to maintain a secure environment for processing, storing, and transmitting low-impact data.
Examples of FedRAMP Low Use Cases
FedRAMP Low use cases involve cloud services that manage data with minimal security risks if compromised. These services implement basic security controls to provide a secure environment for processing, storing, and transmitting non-sensitive data. The following examples illustrate typical FedRAMP Low use cases:
1. Public Websites With Non-sensitive Information:
Cloud services hosting publicly accessible websites that do not contain sensitive or classified information ensure that even in the case of a security breach, the impact on the organization would be minimal. Examples include informational websites, blogs, and promotional content that do not require users to input personal or sensitive data.
2. Collaboration Tools for Non-sensitive Projects:
Cloud-based collaboration tools that facilitate communication and file sharing for projects that do not involve sensitive data ensure secure and efficient collaboration without exposing critical information. Examples of these tools include project management software, messaging apps, and file-sharing platforms used for non-sensitive business operations.
3. Basic Content Management Systems:
Cloud-based content management systems that handle non-sensitive data allow organizations to create, edit, and store content securely without risking sensitive information. Examples include website builders, content publishing platforms, and document management systems that do not store or process sensitive data.
FedRAMP Moderate: Comprehensive Security Controls for Moderate-impact Data
FedRAMP Moderate is designed for cloud services that handle moderate-impact data, defined as data that could cause significant harm to an organization if compromised. These cloud services must implement comprehensive security controls to maintain a secure environment for processing, storing, and transmitting moderate-impact data.
Examples of FedRAMP Moderate Use Cases
FedRAMP Moderate use cases involve cloud services that manage data with a significant security risk if compromised. These services implement comprehensive security controls to provide a secure environment for processing, storing, and transmitting sensitive, unclassified data. The following examples illustrate typical FedRAMP Moderate use cases:
1. Email and File Sharing Services Handling Sensitive but Unclassified Information
Cloud services that manage email and file sharing for sensitive but unclassified data ensure secure communication and storage of sensitive content while maintaining compliance with federal regulations. Examples include email platforms with encryption capabilities, fast, secure file sharing and secure file transfer services, and document management systems that handle sensitive, unclassified information.
2. Human Resources Information Systems
Cloud-based human resources systems that handle team member data, benefits, and payroll information ensure sensitive team member data security and privacy. Examples include applicant tracking systems, benefits administration platforms, and payroll processing software that store and process employees’ personal and financial information.
3. Enterprise Resource Planning and Other Financial Management Systems
Cloud-based financial management systems that handle sensitive financial data, such as budgeting, forecasting, and reporting, ensure the security and privacy of critical financial information. Examples include accounting software, expense management platforms, and financial analysis tools that process sensitive financial data and transactions.
FedRAMP High: Stringent Security Controls for High-impact Data
FedRAMP High is designed for cloud services that handle high-impact data, which could cause catastrophic harm to an organization or individuals if compromised. These cloud services must implement stringent security controls to maintain a secure environment for processing, storing, and transmitting high-impact data.
Typical Use Cases for FedRAMP High
FedRAMP High use cases involve cloud services that manage data with the highest level of a security risk if compromised. These services implement stringent security controls to provide a secure environment for processing, storing, and transmitting high-impact data. The following sections elaborate on typical FedRAMP High use cases, providing examples and valuable data:
Law Enforcement Systems
These cloud services handle sensitive data related to law enforcement operations, such as criminal investigations, evidence management, and intelligence gathering. Examples include case management systems, digital evidence platforms, and criminal intelligence databases that store and process susceptible information.
A federal law enforcement agency may use a cloud-based case management system to securely manage sensitive information related to ongoing investigations securely, ensuring that only authorized personnel can access the data and that it is protected from unauthorized access or tampering.
Electronic Health Records and Health Records Management Systems
Cloud-based health records management systems manage personally identifiable information and protected health information (PII/PHI), such as medical histories, treatment plans, and prescription information, ensuring the security and privacy of critical health information. Examples include electronic health records (EHR) systems, health information exchanges, and patient portals that store and process sensitive patient data.
A government healthcare organization may use a cloud-based EHR system to securely store and manage patient records, ensuring that sensitive health information is protected from unauthorized access and that healthcare providers can access the necessary data to provide adequate care.
National Security Systems
Cloud services handling national security data manage sensitive information about a nation’s defense, intelligence, and critical infrastructure. Examples include secure communication platforms, intelligence analysis tools, and systems supporting military operations that process classified or top-secret information.
A national security agency may use a cloud-based secure communication platform to exchange classified information with other agencies or allied nations, ensuring that the data is protected from interception or unauthorized access and that only authorized individuals can access the information.
Demonstrate FedRAMP Compliance With the Kiteworks FedRAMP Authorized Private Content Network
The Kiteworks Private Content Network offers federal agencies and enterprise businesses a FedRAMP authorized platform that controls, protects, and tracks sensitive content, whether it’s shared via email, file sharing, web forms, managed file transfer (MFT), SFTP, or APIs. Kiteworks is available as a FedRAMP virtual private cloud, featuring a dedicated server isolated from all other Amazon Web Services (AWS) customers on Amazon Cloud, and supported within the United States by U.S. citizens.
Kiteworks secure email provides an additional layer of protection for traditional email. Kiteworks offers comprehensive email security for the confidential emails and file attachments employees share internally and externally. Password-protected links, as well as end-to-end encryption, ensure sensitive information is protected for the entirety of an email’s journey, including through network firewalls. In addition to FIPS 140-2 encryption, outgoing emails are scanned by your data loss prevention (DLP) solution, and inbound emails are scanned by your advanced threat protection (ATP) and content disarm and reconstruction (CDR) solutions. Kiteworks’ Microsoft Outlook Plugin lets users share confidential emails and attachments—with no file size limitation—securely, by letting your organization apply its role-based security policies to protect your emails and the content they contain. The platform’s ease of use does not compromise its security, ensuring users can seamlessly exchange emails while maintaining compliance with FedRAMP standards.
Kiteworks MFT boasts a design focused on simplicity, security, and governance, offering organizations a scalable and dependable solution for configuring policies and partner workflows. Employees can access files stored in various locations, such as folders, file shares, repositories, and cloud stores, and transfer them automatically or manually. The onboarding process for file transfer partners is swift and efficient. Administrators can easily manage, monitor, and recover transfers using an intuitive, graphical operations dashboard. With options for a virtual appliance cluster or hosted service, Kiteworks MFT features a hardened virtual appliance vault and built-in layered defense. This enables administrators and SOC analysts to monitor, track, and document every file transfer, ensuring compliance with regulatory and audit requirements.
Kiteworks SFTP provides enterprise organizations with a compliant file transfer mechanism with MFT functionality on dedicated cloud servers for extra security. Kiteworks hardened SFTP servers protect the sensitive files organizations transfer with solid encryption and integrations with single sign-on (SSO), multi-factor authentication (MFA), advanced threat protection (ATP), data loss prevention (DLP), and security information and event management (SIEM) solutions. Administrators apply granular policy controls for internal users and role-based permissions for external users to protect sensitive files from unauthorized access. Organizations also get complete visibility into their file transfers, including file access, user access, and file movement, supported by advanced analytics and audits.
Kiteworks also offers secure file sharing, critical for organizations handling sensitive content with trusted third parties. Shared files are encrypted both at rest and in transit, so they stay protected from unauthorized access or interception. Users can share files directly from their cloud storage or local systems, and the recipient’s access can be controlled based on predefined policies and timelines. This includes options for view-only access, download restrictions, and folder/file expiration dates so sensitive content doesn’t remain accessible after a project has concluded. Moreover, real-time visibility, tracking, and reporting capabilities allow administrators to monitor file sharing activities, enhancing the transparency and control over the shared content.
Finally, Kiteworks helps organizations transfer sensitive files in compliance with numerous data privacy regulations and standards, including GDPR, Cybersecurity Maturity Model Certification (CMMC), International Traffic in Arms Regulations (ITAR), Information Security Registered Assessors Program (IRAP), UK Cyber Essentials Plus, HIPAA, and many more.
To learn more about Kiteworks’ secure file transfer capabilities, schedule a custom demo today.
Additional Resources
- eBook Learn More About FedRAMP Private Cloud: The Gold Standard for Sensitive Content Communications
- Brief Kiteworks Comparison: On-premises vs. Hosted vs. FedRAMP
- Blog Post SFTP for FedRAMP: Compliance and Authorization Solutions
- Blog Post Navigate FedRAMP for the Private Sector: Kiteworks FedRAMP Authorized Solution Benefits Commercial Businesses, Too
- Blog Post Learn How to Use Managed File Transfer With FedRAMP Compliance