Reduce Third Party Sharing Risks
Control and Visibility | Secure Data Access
- Share data stored in file shares, ECM systems, and public cloud storage services with third parties through a secure, compliant channel
- Govern third party sharing of cloud storage data with full visibility and control
- Know who has custody of sensitive enterprise data
- Keep legacy ECM data storage safely behind the network firewall and avoid data migration
- Enforce role-based sharing policies while honoring source permissions, locking, and versioning
Share Your File, Not Your OneDrive
OneDrive for Business | Secure Data Access
- Now you can lock down risky OneDrive external sharing
- Share sensitive OneDrive files with third parties through secure, governed Kiteworks folders, email, and other channels
- Manage external users without forcing them to use Microsoft Office 365 accounts
- Exert full administrative control over employee sharing privileges
- Full audit trail feeds into central, normalized syslog

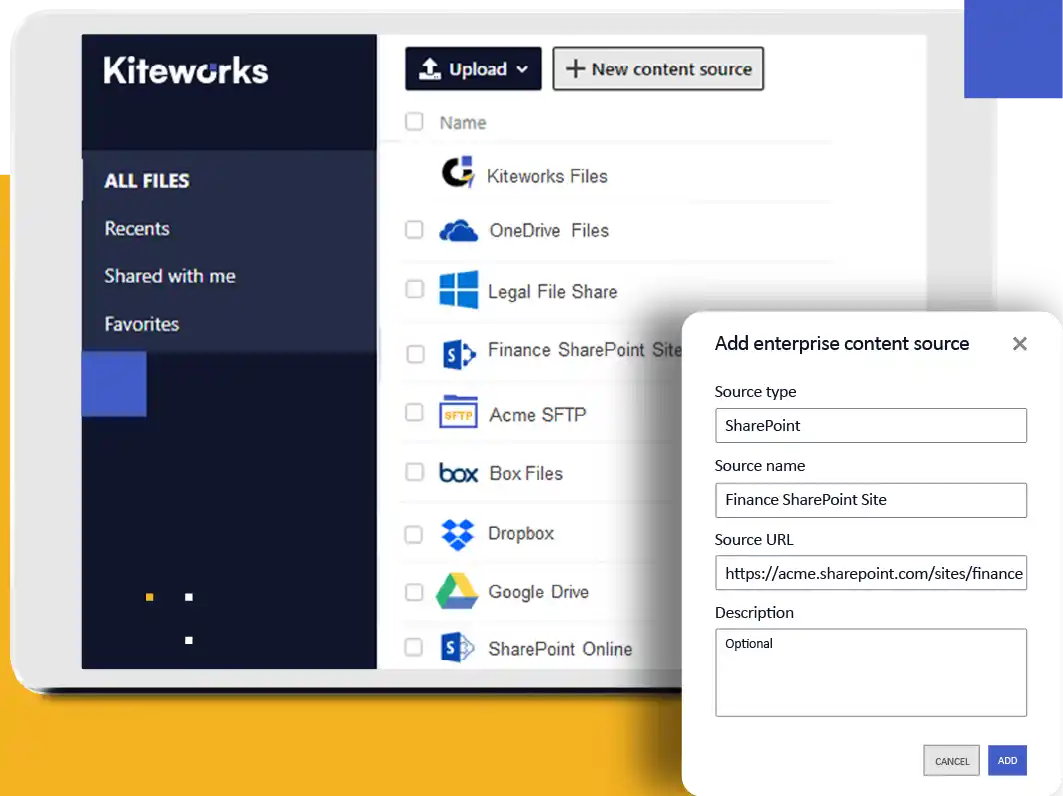
Secure and Unify Enterprise Data Access
ECMs | Secure Data Access
- Self-serve access to enterprise data under IT policy control
- No need for migration or a hard-to-govern VPN
- Users navigate folders as if in the ECM user interface
- Users search for data within SharePoint and file shares
Supported Enterprise Content Management (ECM) sources
- MS SharePoint
- MS Windows file shares and home shares
- SFTP
- Build custom integrations with MANAGED FILE TRANSFER (MFT) ORAPIs
Control Consumer Cloud File Sharing
Govern Shadow IT | Secure Data Access
- Give employees a compliant alternative to Dropbox
- Access public cloud storage through a secure, governed channel
- Enforce compliance and audit of downloads
Covers most popular cloud storage sources
- Microsoft OneDrive for Business
- Microsoft SharePoint Online
- Box
- Dropbox
- Google Drive

Frequently Asked Questions
Secure data access refers to the process of securely retrieving and viewing data or documents from various storage systems or applications, such as Salesforce, NetSuite, Oracle, etc. This involves implementing security measures to ensure only authorized individuals or systems can access specific data. These measures may include user authentication, access controls, encryption, audit logs, and other security protocols. Secure data access entails having a secure and restricted pathway for retrieving and accessing files. This ensures data integrity, confidentiality, and availability, and minimizes the risk of unauthorized access or data breaches. This concept is crucial in today’s business environment where sensitive information is often stored in different platforms and systems, and it forms a significant part of an organization’s overall data security strategy.
Secure data access is an integral part of ensuring data privacy. Features like access control, data protection, audit logs, policy enforcement, and others help businesses set, enforce, track, and report where personally identifiable and protected health information, financial data, intellectual property, and other sensitive data is stored, as well as who has access to it, and what they’re doing with it (downloading, editing, sharing, printing, etc.). This granular level of visibility allows businesses to show auditors and regulators they have a firm handle on their sensitive data and have protections in place protect that data from unauthorized access.
Secure data access helps businesses protect their sensitive information from unauthorized access in many different ways. For example, secure data access can require employees and trusted partners to authenticate their identities before they access certain sensitive information. Businesses may also employ multi-factor authentication prior to accessing sensitive information. Once a user’s identity is confirmed, access controls can be used to ensure employees and partners only have access to the files they need, but not others. Systems with secure data access also monitor and log who is accessing what data and when to help identify any suspicious activity. These and other security features allow organizations to significantly lessen the risk of sensitive information being accessed by unauthorized individuals.
You can securely share data stored in enterprise repositories like SharePoint, OneDrive, Box, and others with third parties by using a platform that offers secure and compliant channels for sharing. Ensure that the platform allows you to enforce role-based sharing policies, maintain source permissions, and provide visibility and control over who has access to sensitive enterprise data. The platform should also contain security features like access controls, multi-factor authentication, encryption of all data in transit and at rest, data loss prevention (DLP) integrations, and others.
Businesses can ensure they have protected their sensitive information from unauthorized access in several different ways. Examples include, but are not limited to: strong user authentication, role-based access controls, data encryption, a secure network featuring firewalls, VPNs, and other security protocols, anti-malware software, data loss prevention (DLP) tools, and finally secure content management systems that can control access to sensitive documents, track changes, and see who has viewed a document.
FEATURED RESOURCES

Kiteworks Enterprise Connect: Secure, Unified Access to Your Content Repositories

Capability Brief: Secure Managed File Transfer (MFT)

