
Collaborate Securely Across Geographic Borders
Collaborating with colleagues, partners, and customers across geographic borders allows businesses to expand their market reach, reduce costs, gain access to distinct skills and expertise, and connect with diverse markets effectively. Organizations must, however, protect the data on which they collaborate. With Kiteworks, choose the encryption method that best suits your needs: S/MIME, OpenPGP, TLS encryption 1.2 for data in transit, AES-256 for data at rest, and FIPS 140-2 validated encryption cyphers. An email encryption gateway encrypts data at the email client or gateway, not plugins, and keeps data encrypted from sending client to receiving client for full, uninterrupted protection. Leverage granular access controls to set and enforce who can access PII and other sensitive data based on role and set expiration dates to ensure authorized users have access to data only for how long it’s needed.
Ensure Customer Data Stays Where It Belongs
It’s not enough for organizations to commit to storing PII where the data owner resides. Organizations must prove it or face noncompliance fines and penalties. With Kiteworks, organizations enforce geofencing by setting block-lists and allow-lists for IP address ranges. Customers can configure a distributed system to store a user’s data only in their home country. Ensure privacy in hostile countries with sole ownership of encryption keys. Finally, configure Kiteworks to demonstrate data sovereignty and geofencing whether it’s deployed on-premises, on IaaS, Kiteworks-hosted, FedRAMP, or hybrid cloud. Or use a Kiteworks private cloud to prevent risky comingling of data with other customers.

Comply With Regional Privacy Regulations
Persistent cyber threats, rampant misuse of personal data, gkw-flex-container kw-align-middle kw-padding-v-ming public awareness of data privacy rights, and other drivers have pressured governments to enforce robust data protection laws. Kiteworks enables organizations to comply with national, regional, and state data privacy laws. Granular access controls and role-based permissions ensure only authorized personnel have access to PII. See, track, and report on every file upload, download, send, or edit. A CISO Dashboard lets you see all files from all connected systems and all activity: who’s sending what to whom, when, and where. Feed activity syslogs into your SIEM solution, and with a single click, generate detailed compliance reports that provide visibility into a system’s configurations and security settings and flag any issues impacting compliance.
See Where PII Is Stored and Who Has Access to It
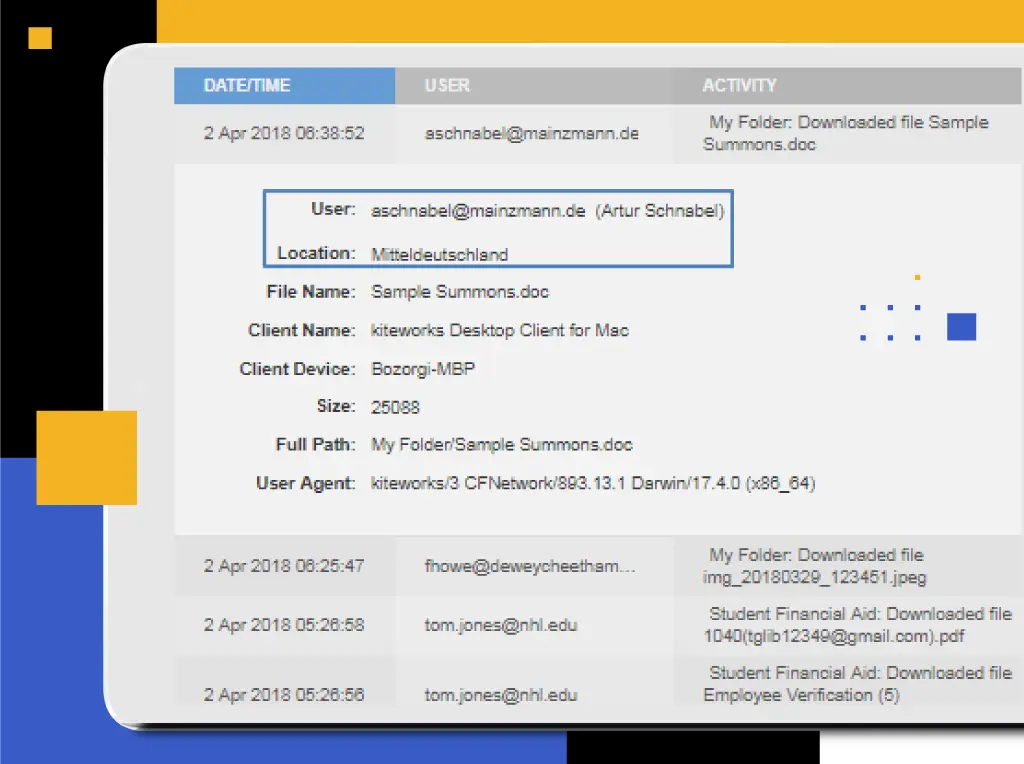
Unless you can see where PII, PHI, and other sensitive information is stored throughout the enterprise, you can’t protect it. You can’t control who can access it or what they do with it. In short, you can’t ensure it stays private. With Kiteworks, organizations have a comprehensive picture of all sensitive information going in, through, and out of the enterprise. See all files from all connected systems, whether on-premises or in the cloud. Visibility extends down to the file level, the closest you can get to the data. Set, enforce, track, and report on all file activity, including uploads, downloads, edits, shares, receipts, DLP and ATP scans, and more.

Comply With Data Portability Requirements
The EU’s GDPR, Australia’s CDR, Canada’s PIPEDA, California’s CCPA, and other data privacy laws contain data portability requirements, allowing individuals to obtain and reuse their personal data. Organizations that do not or cannot comply with data portability requirements face stiff penalties and reputational damage. Kiteworks supports data portability requirements by enabling the secure access, transfer, and download of a citizen’s personal information. PII is quickly discovered from a single pane of glass with visibility into all connected on-premises and cloud data sources. Establish opt-in mechanisms and procedures for data collection, detailed consent forms, and minor consent procedures. In addition, data remains protected during the portability process through secure file sharing, encryption, and access control features.
Frequently Asked Questions
Data sovereignty is the concept that data is subject to the laws, regulatory requirements, and governmental actions in the nation or region in which it is created, collected, stored, or processed. It is a concept that underpins many pieces of international data privacy and security laws, recognizing the importance of maintaining the integrity of data that is generated and used within a particular jurisdiction. Data sovereignty also helps to protect an individual’s right to privacy, as it sets clear boundaries on where and how their data can be used, and ensures that the data will be subject to the same level of protection regardless of where it is being processed, accessed, or stored.
Data sovereignty is closely related to the concept of data protection and privacy. When considering data sovereignty, organizations should consider how, and under whose laws, the data is being collected, stored, accessed, and processed. Additionally, organizations should consider if and how data can be transferred from one jurisdiction to another. Data sovereignty considerations also apply to the security of data and the organizations responsible for protecting it, including the levels of encryption used, access controls, and governance policies.
Data sovereignty helps organizations ensure that their customer data is handled in accordance with the local laws and regulations of the region or country in which it is created, collected, stored, or processed. It also helps to provide individuals with a level of assurance that their data is safeguarded and secure wherever it is stored.
Data sovereignty applies to all types of data, including personally identifiable information (PII), as well as other data related to the activities and operations of a business. It applies to data that is generated and stored within a given jurisdiction, regardless of what form the data takes (e.g., electronic or paper records). Additionally, data sovereignty may also apply to data that is transferred from one jurisdiction to another, and organizations should consider any data sovereignty implications prior to transferring any data.
Organizations must be aware of the laws, regulations, and governmental actions of the jurisdiction in which their data is created, collected, stored, and processed. They must ensure that their data is secured and compliant with the relevant laws, and they should ensure that they have the necessary processes, systems, and policies in place to protect the data and ensure that it is handled in accordance with data sovereignty requirements. Additionally, organizations must consider any data sovereignty implications prior to transferring any data.
FEATURED RESOURCES

Navigate the Digital Trifecta of Data Sovereignty, Cybersecurity, and Compliance With Kiteworks

Understanding Data Sovereignty: Regulations, Security, and Compliance in 2023
