Remaining Consistent With 13 Areas of the Security Policy
Complying with CJIS can be challenging due to the strict security requirements for protecting sensitive criminal justice information, necessitating robust access controls, encryption, auditing, and incident response measures across all systems and communications.
Incident Response Tools for Prompt Potential Data Violations
Complying with CJIS incident response requirements can be challenging, as organizations must promptly detect, report, and investigate any potential data violations. The CJIS Security Policy mandates timely reporting of incidents and preservation of evidence for analysis, containment, and recovery. Organizations must have robust mechanisms in place to identify and respond to unauthorized access attempts and potential data exfiltration.


Detect Breaches and Unauthorized Access With Strong Auditing and Accountability
The CJIS Security Policy requires comprehensive logging and monitoring of sensitive information to detect potential breaches and unauthorized access. Organizations must have granular access controls and permissions in place to reduce risks.
Verify Permissions With Strict Access Control
Implementing and managing granular access controls to secure sensitive criminal justice information requires strict control over who can access sensitive data, ensuring that only authorized individuals have appropriate permissions. Organizations must have secure storage, role-based policies, and effective monitoring mechanisms in place to protect sensitive information from unauthorized access and potential breaches.


Verify Identities via Identification and Authentication
Ensuring strong identification and authentication mechanisms to comply with CJIS requirements mandates robust authentication measures to verify user identities and prevent unauthorized access. Organizations must implement complex password policies, multi-factor authentication, and secure single sign-on (SSO) capabilities.
Complying With Support From Kiteworks
Incident Response via Robust Audit Logs
Kiteworks supports CJIS compliance by providing anomaly detection and real-time monitoring capabilities. Utilizing advanced AI technology, Kiteworks detects suspicious events and triggers alerts through email notifications and audit logs. This enables organizations to quickly identify and respond to incidents, ensuring compliance with CJIS standards for mandatory reporting of data violations. Kiteworks also preserves evidence for thorough analysis and containment
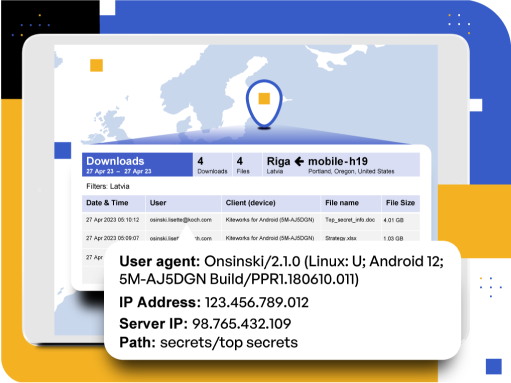
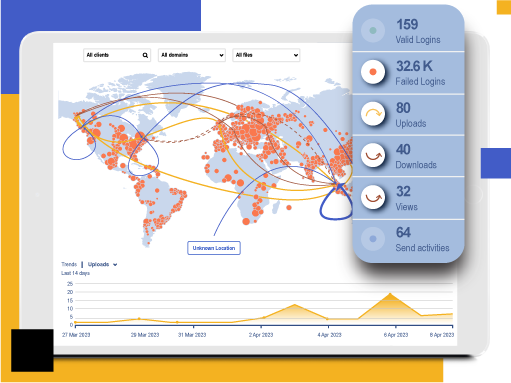
Auditing and Accountability With Real-time Monitoring
Kiteworks assists with CJIS compliance by offering robust auditing and accountability features. The platform maintains detailed logs of data access, transfers, and user activities, ensuring transparency and accountability. Real-time monitoring identifies potential breaches promptly, while granular access controls enforce permissions and roles. Customizable reporting options generate detailed reports for audits, compliance assessments, and investigations, supporting organizations in maintaining security and compliance.
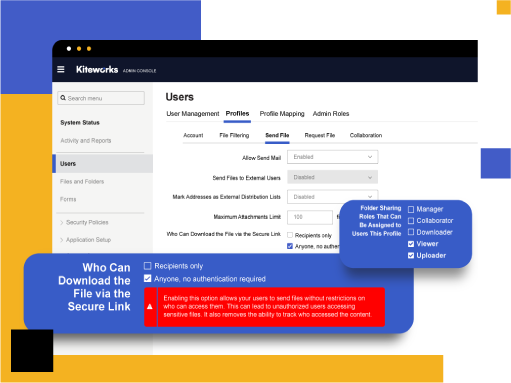
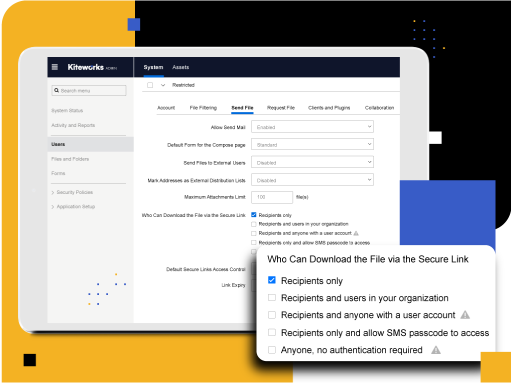
Granular Access Controls Protect Sensitive Data
Kiteworks simplifies CJIS compliance by providing comprehensive access control features. The platform offers secure storage, role-based policies, secure email and shared folders, built-in audit logging, and a CISO Dashboard for effective monitoring and management. These features ensure that sensitive information is protected from unauthorized access, helping organizations maintain CJIS compliance.
Identify and Authenticate Easily With Password Policies and MFA
Kiteworks supports CJIS compliance by providing advanced identification and authentication features. Administrators can set policies for password complexity, geofencing, and domain whitelisting/blacklisting, as well as enforce password changes during login. Granular multi-factor authentication and SSO policies can be applied by role and location using various methods like RADIUS, SAML 2.0, Kerberos, authenticator apps, PIV/CAC, and SMS. These features help organizations detect and respond to security incidents, manage vulnerabilities, and maintain CJIS compliance.
Frequently Asked Questions
CJIS compliance requires organizations to promptly detect, report, and investigate any potential data violations. The CJIS Security Policy mandates timely reporting of incidents and preservation of evidence for analysis, containment, and recovery. Organizations must have robust mechanisms in place to identify and respond to unauthorized access attempts and potential data exfiltration.
CJIS compliance requires maintaining detailed audit logs and ensuring accountability for data access and user activities. The CJIS Security Policy mandates comprehensive logging and monitoring of sensitive information to detect potential breaches and unauthorized access. Organizations must have granular access controls and permissions in place to reduce risks.
To comply with CJIS requirements, organizations must implement and manage granular access controls to secure sensitive criminal justice information. This includes strict control over who can access sensitive data, ensuring that only authorized individuals have appropriate permissions. Organizations must have secure storage, role-based policies, and effective monitoring mechanisms in place to protect sensitive information from unauthorized access and potential breaches.
CJIS compliance mandates strong identification and authentication mechanisms to verify user identities and prevent unauthorized access. Organizations must implement complex password policies, multi-factor authentication, and secure single sign-on (SSO) capabilities. These measures should be applied across multiple systems and user roles to ensure consistent security.
To protect sensitive criminal justice information and meet CJIS requirements, organizations must implement a comprehensive set of security measures, including encryption, access controls, auditing, and incident response capabilities. A secure environment for storing, sharing, and managing sensitive data is essential to ensure compliance with the strict security requirements outlined in the CJIS Security Policy.
FEATURED RESOURCES

What You Need to Know About Sensitive Content Security and Compliance in 2024

How Federal Agencies Can Comply With the Data Requirement in Executive Order 14028

CISA Security-by-Design and Default: Requirements & Kiteworks Features

CMMC Mapping: Sensitive Content Communications for CMMC 2.0 Compliance

FedRAMP Private Cloud: 5 Reasons Why Security-first Businesses Choose FedRAMP
