MFT Suite
Why Add:
- Compliant End-to-End Workflow Automation
- Comprehensive Connectivity
- Scalable, Resilient Architecture
Anatomy of an MFT Breach
This webinar, featuring Charles Carmakal, CTO and Board Advisor at Mandiant (Google Cloud), and Yaron Galant, Chief Product Officer at Kiteworks, explores the three most popular MFT attack vectors, the recent cyberattacks on MFT solutions by the cybercriminal group Clop, and three common misassumptions businesses make during an MFT breach.
Challenges With Legacy Managed File Transfer
Outdated Security Measures Expose Legacy MFT Platforms
Organizations risk sensitive data exposure, penalties, and litigation every time they use a managed file transfer solution with inadequate encryption, poor access controls, and insufficient audit logging. As businesses increasingly transfer sensitive data with trusted third parties, it’s imperative that a managed file transfer solution prioritizes data protection for maximum security. Effective data breach prevention requires an MFT solution with robust encryption methods, strict access control policies, and continuous monitoring of data transfers to mitigate unauthorized access.
Compliance Capabilities Are Insufficient in Traditional MFT Tools
Meeting compliance requirements for data protection regulations such as GDPR, HIPAA, PCI DSS, CCPA, and others is a major challenge for organizations utilizing managed file transfer solutions. Compliance necessitates the implementation of strict data protection policies, regular security assessments, and detailed auditing capabilities to track and manage data transfers effectively. A managed file transfer platform therefore must offer comprehensive logging and reporting tools to demonstrate compliance with regulatory standards, requiring organizations to regularly update their security practices and ensure their managed file transfer solutions can adapt to evolving compliance requirements.


Limited Scale in Legacy Managed File Transfer Products
As organizations grow, their data transfer needs evolve, requiring scalable managed file transfer solutions that can handle increased loads without compromising security or performance. Scalability challenges include managing larger volumes of data transfers, including large file sizes, ensuring the security of transferred data amidst growing traffic, and maintaining system performance. To overcome these challenges, organizations should invest in managed file transfer solutions that offer high availability, load balancing, and robust security features capable of adapting to changing data volumes and transfer requirements. Regular performance testing and capacity planning are crucial to ensure the managed file transfer system can scale securely and efficiently with the organization’s needs.
Legacy MFT Solutions Have an Atrocious User Experience
Legacy managed file transfer systems frequently suffer from convoluted and non-user-friendly interfaces, which can dramatically decrease productivity and increase the likelihood of user errors. These systems often require extensive training to navigate, and their lack of intuitive design can lead to improper file handling and security mishaps. The interfaces may not align with modern user experience standards, causing confusion and frustration among users accustomed to more streamlined, contemporary applications. To combat these issues, organizations should consider upgrading to managed file transfer solutions with cleaner, more intuitive user interfaces that promote efficiency, reduce the risk of error, and align with the user experience expectations of today’s workforce.


Inadequate Access Controls Imperil Legacy MFT Solutions
Legacy managed file transfer solutions frequently fall short in providing robust access controls, lacking comprehensive security features for both users and administrators. This deficiency can lead to unauthorized access to sensitive information, increasing the risk of data breaches. Modern, secure managed file transfer solutions implement granular administrative controls that prevent privileged users’ access to the underlying operating system, file systems, and databases. These solutions prevent the installation and execution of unauthorized code, creating strong barriers against insider threats and sophisticated attackers. They enable dynamic access controls, including multi-factor authentication (MFA), role-based access controls (RBAC), attribute-based access controls (ABAC), and administrative oversight of all file operations, ensuring sensitive data remains protected throughout its life cycle. These comprehensive access controls, combined with strict limitations on administrative privileges, are crucial for organizations aiming to safeguard their digital assets against both external and internal threats while complying with evolving data protection regulations.
Lack of Visibility in Legacy Managed File Transfer Platforms
Legacy managed file transfer platforms tend to suffer from a significant lack of visibility, lacking the centralized, advanced tracking and monitoring capabilities essential for contemporary data governance. Without the means to comprehensively audit file movement and access, organizations struggle to maintain oversight, making it nearly impossible to detect anomalies or breaches promptly. This opacity hinders compliance with data protection regulations that mandate strict monitoring and reporting procedures.

Kiteworks Secure Managed File Transfer Solution
Streamline and Secure Large-scale File Transfer Operations
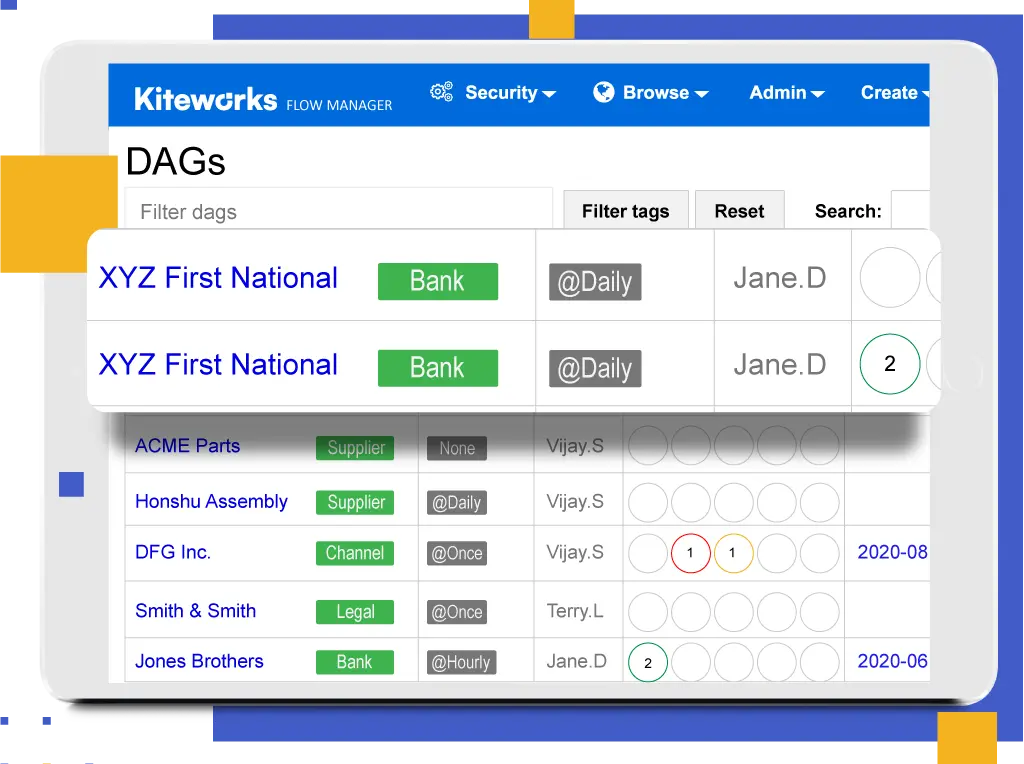
With Kiteworks Secure Managed File Transfer, organizations maximize end-to-end security with unique vault-to-vault transfers. They can access data wherever it’s stored: in folders, file shares, repositories, and cloud stores. Trigger file transfers with scheduling, polling, or events, or start them manually. Onboard new trading partners and author MFT workflows simply and quickly. Finally, manage, monitor, and recover file transfers with a graphical operations dashboard.
LEARN MORE ABOUT KITEWORKS SECURE MANAGED FILE TRANSFER SERVER
Automate Secure and Flexible Business Processes
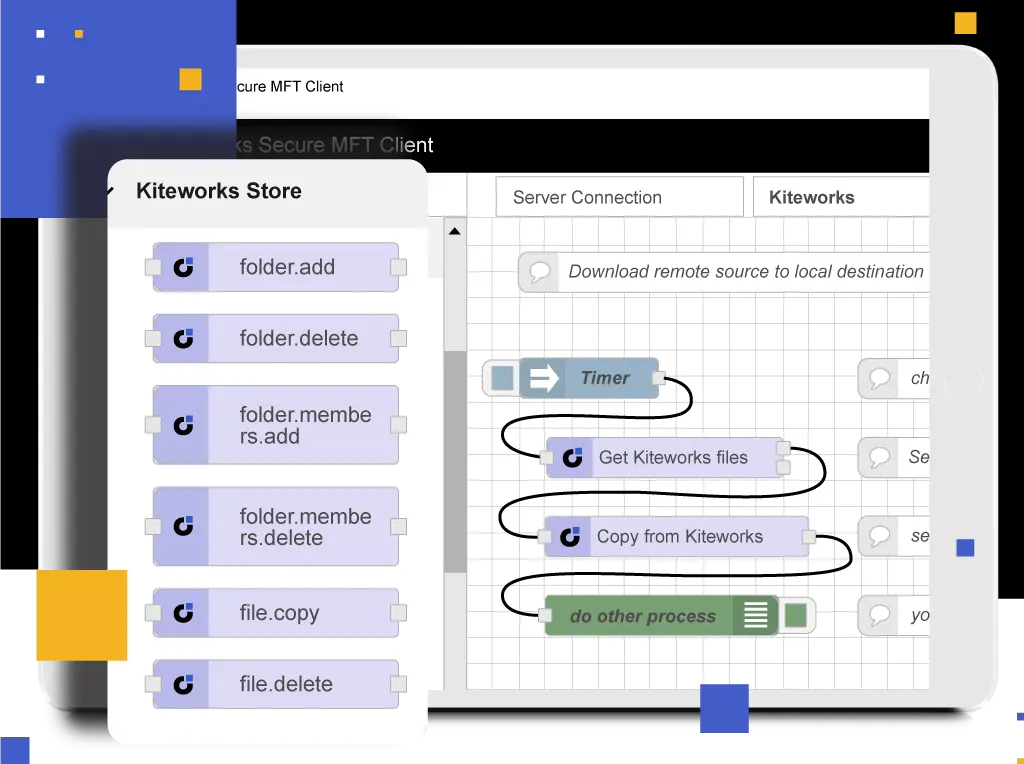
Kiteworks Secure Managed File Transfer enables organizations to make departmental file transfer processes simple, foolproof, and compliant. Leverage a library of 2,000 connectors and workflow functions. Distribute throughout the organization, but manage centrally. Author visual workflows without coding.
LEARN MORE ABOUT KITEWORKS SECURE MANAGED FILE TRANSFER CLIENT
Protect Your Data From Advanced Persistent Threats With a Hardened Virtual Appliance
Go beyond protecting sensitive data with encryption protocols and storage. With Kiteworks Secure Managed File Transfer, organizations minimize their MFT attack surface by enclosing all system components in a hardened virtual appliance. Place a firewall around each server, default to most secure settings, shut off unnecessary ports, remove unnecessary code, and isolate traffic between tiers. Intrusion detection systems detect and alert on suspicious system modifications. Security is bolstered by Kiteworks’ secure development life cycle, regular penetration testing, and worldwide bounty program that eliminates bugs before they become vulnerabilities. Finally, one push of a button updates all the system components so organizations never miss a patch.
Set Granular Policy Controls to Prevent Data Breaches and Compliance Violations
Kiteworks Secure Managed File Transfer lets organizations prevent any malicious activity from insiders with the implementation of proper separation of duties and workflow-level access controls. Govern MFT end-users with appropriate role-based permissions and set data access policies to regulate where data and metadata are stored and prevent any exposure. Implement firewalls and other zone-savvy policies to further protect the data transfer. Link to a DLP system to block and log any sensitive transfers, use an ATP system to quarantine any potential malware, and introduce CDR to deliver only malware-free data. Finally, meet industry standards such as NIST 800-53, PCI DSS, and ISO 27001, 27017, and 27018 with ease.
LEARN MORE ABOUT KITEWORKS GRANULAR POLICY CONTROLS AND REGULATORY COMPLIANCE CAPABILITIES
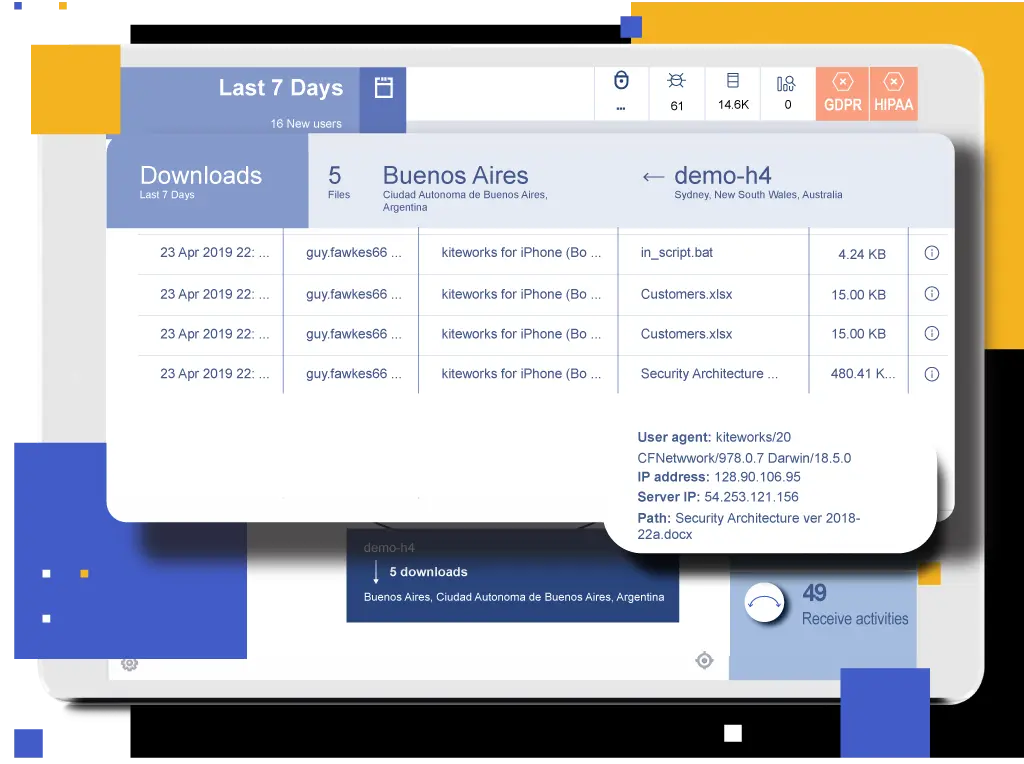
See All Data Entering and Leaving the Enterprise
Kiteworks’ security analytics arms organizations with complete visibility into what’s happening with their sensitive data. See all sensitive information entering and leaving the organization in a standardized log of all transactions involving Secure Managed File Transfer, secure email, secure file sharing, secure web forms, and application programming interfaces (APIs). Understand who’s transferring what to whom, when, where, and how. Detect suspicious MFT activity and take action on data anomalies. Create custom dashboards and reports in a SIEM tool, or utilize the Kiteworks Splunk App. Lastly, pass audits and comply with industry regulations.
Prevent Leaks and Breaches With AV, DLP, CDR, and ATP
Organizations can significantly reduce the risk of a data leak, cyberattack, or compliance violation when they run each file through a gauntlet of security tools designed to detect and quarantine malicious code. The Kiteworks Private Data Network integrates with an organization’s security infrastructure to keep confidential information private. Scan outgoing data through your ICAP-compatible DLP deployment and enforce rules for logging and blocking transfers. Scan incoming files for viruses with Kiteworks’ embedded antivirus. Detect and quarantine unknown threats in inbound data with an ATP product such as Check Point SandBlast or FireEye Malware Analysis (AX) and Detection on Demand. Finally, eliminate malware in incoming data using CDR products like Forcepoint ZT CDR.
LEARN MORE ABOUT PROTECTING YOUR SENSITIVE DATA WITH KITEWORKS SECURITY INTEGRATIONS
Leverage All Kiteworks Communication Channels
It’s much easier to see, control, and protect the sensitive data organizations send and receive when they consolidate their third-party communications. With Kiteworks, organizations securely access enterprise data in file shares, home shares, SharePoint, other on-premises enterprise content management (ECM) systems, and cloud shares such as Microsoft OneDrive, Google Drive, and Box. Set and enforce file sharing privileges based on user roles. All file activity is tracked and recorded in a comprehensive audit trail.
LEARN MORE ABOUT HOW KITEWORKS UNIFIES THIRD-PARTY COMMUNICATION CHANNELS
Frequently Asked Questions
Managed file transfer (MFT) is a software solution that helps organizations securely transfer information, typically large volumes of files on a scheduled, or recurring, basis. It enables an end-to-end file transfer process that supports secure file transfer between different systems and networks, or systems and people. Modern MFT solutions offer multiple features such as encryption, automation, and auditing to ensure secure file transfer. It also provides features to monitor, track, and control the transmission of sensitive files.
Secure managed file transfer refers to the process of securely and efficiently transferring files between systems, users, or organizations in a managed and controlled manner. Secure managed file transfer offers businesses a more secure option for managed file transfer. It’s specifically designed with the primary goal of protecting sensitive data against unauthorized access, data breaches, and compliance violations. It ensures data integrity, confidentiality, and compliance with various data privacy regulations and standards like PCI DSS, GDPR, HIPAA, and ISO 27001.
Managed file transfer (MFT) offers businesses several advantages over other forms of file transfer. These advantages include: increased security such as encryption and authentication; automation that saves time and money by streamlining processes; centralized management to maintain visibility and control over file transfers from a centralized platform; comprehensive audit logs that record all user activities; improved scalability so organizations can easily increase their file transfer capacity and throughput, enabling them to accommodate greater amounts of file transfers and data.
Managed file transfer (MFT) software solutions use a variety of security measures to protect data, including secure protocols, encryption, and authentication. In addition, access controls ensure that only authorized users can access the data. Depending on the platform, additional features like audit tracking, monitoring and alerting, and automated workflows may also be available.
Yes, many managed file transfer (MFT) solutions are designed to be compatible with existing systems and infrastructure. Depending on the solution and your specific requirements, managed file transfer can be used to securely transfer data between systems, or to integrate with existing workflows and processes.
FEATURED RESOURCES

Capability Brief: Secure Managed File Transfer (MFT)

Top 5 Advantages of Kiteworks Secure Managed File Transfer Capabilities Over Axway MFT

Best Secure Managed File Transfer Solutions for Enterprise

Kiteworks Snackable Bytes: Secure Managed File Transfer

Optimize File Sharing Governance, Compliance, and Content Protection