
CMMC 2.0 – What UK-Based DOD Contractors Need to Know
As a UK-based contractor or sub-contractor, you represent a crucial link in the DOD’s supply chain. CMMC, the Cybersecurity Maturity Model Certification programme, is designed to reinforce this supply chain and protect the information that enables the DOD’s warfighters.
The Defense Industrial Base (DIB) is “a target of more frequent and complex cyberattacks”. In order to protect sensitive US security information, the DOD has revitalised its CMMC programme with cybersecurity standards designed to meet these evolving threats.
In this blog, we explore CMMC 2.0 Level 2, tracking its evolution and summarising what contractors need to know about becoming CMMC 2.0 compliant.
CMMC 2.0 Compliance Roadmap for DoD Contractors
The Background for the CMMC Programme
The initial vision and basic features of the CMMC programme were introduced in September 2020 through an interim rule to the DFARS in the Federal Register. It outlined a framework which included a tiered model, assessments and implementation for contractors. Over the next year, the DOD collected feedback from cybersecurity and acquisition leaders within the DOD, as well as public comments, to help refine the policy.
This resulted in CMMC 2.0, the second iteration of the programme which was released in 2021, and is due to be enforced in 2025.
CMMC 1.0 vs CMMC 2.0
Both CMMC 1.0 and 2.0 were designed to safeguard controlled unclassified information (CUI) and federal contract information (FCI) within the DIB.
CMMC is the framework that outlines the cybersecurity requirements against which the DOD will assess and certify contractors. Any organisation that doesn’t meet these requirements will be unable to work with the DOD from 2025 onwards.
Based on the feedback, CMMC 1.0 was replaced with CMMC 2.0 to achieve the following goals:
- Reduce the cost of meeting CMMC requirements
- Increase trust in the CMMC assessment ecosystem
- Align CMMC requirements with other federal requirements and common standards
These updates streamlined the CMMC model, provided additional clarity, and reduced the regulatory burden to make it easier for contractors to comply with its requirements.
Some of the main differences relate to:
Maturity Levels
CMMC 1.0 outlined 5 maturity levels, which has since been reduced to 3 under CMMC 2.0, removing levels 2 and 4.
- Level 1: Foundational remains unchanged. It requires an annual self-assessment that has attestation from a corporate executive. It also encompasses the FCI safeguarding requirements from FAR Clause 52.204-21.
- Level 2: Advanced reorganised the previous Level 3 to align with the 14 domains that align with the families specified in NIST SP 800-171. It requires triennial third-party assessments for contractors that send, share, receive, and store critical national security information.
- Level 3: Expert combines the previous Levels 4 and 5. It aims to align with NIST SP 800-172 and will require triennial government-led assessments but is still in development.
Domain Structures
The CMMC 2.0 domain structures are much more comprehensive than those outlined in the CMMC 1.0 model. These additional domains are more specific to the daily operations of contractors and aim to create greater assurance of asset security.
Third-Party Assessors
CMMC 2.0 has introduced third-party assessors for certifying that DIB supply chain contractors are meeting the required standards. C3PAOs will be responsible for evaluating and issuing certificates at Level 2.
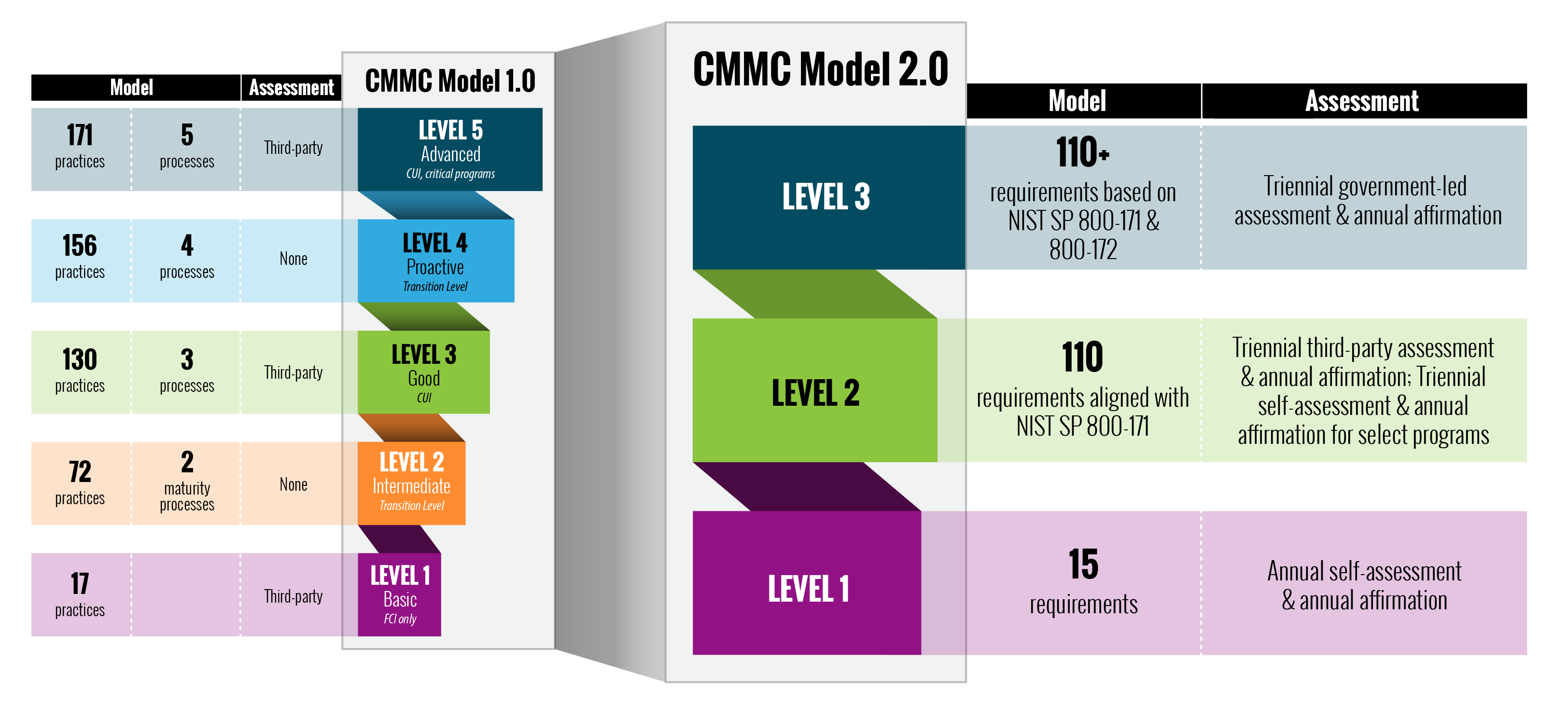
Figure 1: Source: US Department of Defense
How to Become CMMC 2.0 Compliant
Contractors and subcontractors currently working with or planning to work with the DOD must demonstrate compliance with CMMC 2.0 by 2025.
Overall, the requirements for Levels 1 and 2 CMMC 2.0 compliance fall into 14 different domains and consist of a total of 110+ controls (i.e. requirements) across these domains.
CMMC 2.0 compliance domains:
- Access control
- Audit and accountability
- Awareness and training
- Configuration management
- Identification and authentication
- Incident response
- Maintenance
- Media protection
- Physical protection
- Personnel security
- Risk assessment
- Security assessment
- System and communications protection
- System and information integrity
Get a checklist for CMMC compliance here
First, organisations must determine which tier they fall under so they can act appropriately.
Different levels of maturity will necessitate different actions for compliance. For example, if your bid or contract involves you handling CUI, controlled technical information (CTI), or ITAR/export-controlled data, you will fall under the Level 2 criteria.
Read our guide to Level 2 compliance
Next, organisations should follow these steps in preparation:
-
✓ Conduct a risk self-assessment
✓ Review and leverage existing NIST frameworks
✓ Create a POA&M and SSP
✓ Select a C3PAO
✓ Set a timeline and budget
✓ Implement tailored security controls
✓ Establish an incident response plan
✓ Monitor security controls performance and identify issues
✓ Document compliant actions
How Kiteworks Supports CMMC 2.0 Compliance
Kiteworks is a secure content communications platform that supports nearly 90% of Level 2 requirements out of the box. The platform is a FedRAMP Moderate Authorized Private Content Network (PCN) that helps defence contractors to control, track and secure the sharing of sensitive data internally and externally.
Consisting of multiple advanced security capabilities, from next-generation digital rights management (DRM) to managed file transfer, Kiteworks helps ensure you are compliant with CMMC 2.0 while also managing communications risks that may arise within your own supply chain and subcontractors.
Want to make sure you’re ready for CMMC 2.0? Read more about how to reduce CMMC compliance risks across your organisation and your supply chain.
FAQs
Compliance with NIST standards is integrated into CMMC 2.0 requirements. CMMC aligns with clauses such as FAR 52.204-21 and complements clauses such as DFARS 252.204-7012. Depending on their Level, contractors will conduct a self-assessment or a third-party assessment to determine whether the applicable NIST standard has been met.
Under CMMC 2.0, a Level 2 assessment will be conducted against the NIST SP 800-171 standard.
A CMMC C3PAO is a CMMC third-party assessor organisation (C3PAO) that has been certified by the CMMC accreditation body (CMMC-AB). A C3PAO will assess contractors and subcontractors to determine if they are compliant against CMMC standards and will provide the certification.
Their responsibilities include evaluating assessments, issuing certificates of adherence and recommending corrective actions as needed. The C3PAO must review and certify the contractor or subcontractor’s audit and self-assessment reports based on the DOD’s Cybersecurity Maturity Model.
Working with a CMMC third-party assessor organisation (C3PAO) provides several benefits for contractors seeking certification under CMMC 2.0 standards:
Expertise: a certified third-party assessor has extensive experience assessing cybersecurity programmes across multiple industries and can provide valuable insight into best practices for achieving compliance with CMMC 2.0 standards.
Objectivity: an independent third-party assessor provides unbiased feedback on a contractor’s security posture and provides practical recommendations to help you comply.
Cost Savings: working with a certified third-party assessor can save time and money compared to hiring internal staff or consultants who may not have expertise in assessing cybersecurity programmes.
Efficiency: a certified third-party assessor can quickly identify gaps in an organisation’s security posture, helping to achieve compliance in time for 2025.
Peace of mind: having an independent third-party assessor review a DOD supplier’s cybersecurity programme provides peace of mind, ensuring that organisations have taken all necessary steps toward achieving compliance with CMMC 2.0 standards.
Regulatory compliance refers to the adherence to laws, regulations, guidelines, and specifications relevant to an organisation’s business processes. Compliance is crucial for maintaining the company’s reputation, avoiding legal penalties, and ensuring the safety and security of operations.
Secure data communications features play a crucial role in regulatory compliance as they help protect sensitive data from unauthorised access. They empower defence contractors to share sensitive content internally and throughout their supply chain by email, file sharing, file transfer, and other channels, with the highest levels of security, access control, and accountability.
Features that will support CMMC 2.0 include:
- Secure file sharing
- End-to-end email encryption
- Secure file transfer protocol (SFTP)
- Managed file transfer (MFT)
- Digital rights management (DRM)
- Access control
- Unified logging and reporting
- Audit trails
Additional Resources
- Blog Post Essential CMMC 2.0 Controls List for Compliance
- Blog Post A Roadmap for CMMC 2.0 Compliance for DoD Contractors
- Blog Post Insights into CMMC Level 2 Requirements
- Blog Post CMMC Compliance Guidelines for UK Contractors
- Article Key Steps for CMMC Assessment Preparation