Introduction
As we navigate the complex landscape of cybersecurity in 2024, the increasing frequency and severity of data breaches are undeniable. In the first half of this year alone, cybercriminals have compromised over a billion records, affecting multiple sectors, including telecommunications, healthcare, finance, and government. These incidents have not only exposed the vulnerabilities within our digital infrastructures but have also underscored the urgent need for robust cybersecurity strategies to protect sensitive data.
Introduction
Dear Readers,
As we navigate the complex landscape of cybersecurity in 2024, the increasing frequency and severity of data breaches are undeniable. In the first half of this year alone, cybercriminals have compromised over a billion records, affecting multiple sectors, including telecommunications, healthcare, finance, and government. These incidents have not only exposed the vulnerabilities within our digital infrastructures but have also underscored the urgent need for robust cybersecurity strategies to protect sensitive data.
The “Top 11 Data Breaches in 1H 2024” report leverages the Kiteworks Risk Exposure Index to provide a detailed analysis of the most significant breaches that occurred in the first half of the year. Our findings reveal several alarming trends, from the rising prevalence of ransomware attacks to the vulnerabilities associated with third-party interactions and internal errors. This report highlights the critical importance of managing sensitive content communications across all sectors, especially as organizations increasingly rely on multiple communication tools and third-party services, which can create numerous entry points for cyber threats.
At Kiteworks, we are committed to helping organizations mitigate these risks by providing actionable insights and recommendations. The Risk Exposure Index, featured in this report, is a strategic tool designed to help organizations evaluate and prioritize data breaches based on their severity and potential impact. By employing this comprehensive framework, organizations can better allocate resources, strengthen their security postures, and enhance their overall resilience against future breaches.
We hope this report provides valuable guidance as you continue to safeguard your sensitive information. Together, we can build a more secure digital future.
Sincerely,
Patrick Spencer
Patrick Spencer, Ph.D.
VP of Corporate Marketing and Research
Kiteworks
Overview of Data Breaches in 1H 2024
The first half of 2024 saw a significant increase in the number and scale of data breaches, reflecting the growing sophistication and determination of cybercriminals worldwide. According to data from the Identity Theft Resource Center (ITRC),1 the top 10 data breaches during this period compromised over a billion records across various sectors, including telecommunications, healthcare, finance, technology, and government agencies. These incidents range from ransomware attacks and supply chain vulnerabilities to accidental data leaks, highlighting the diverse tactics employed by cybercriminals and the widespread vulnerabilities across different industries. ITRC’s top 10 failed to include the National Public Data breach, which exposed as many as 2.9 billion data records associated with 1.3 million people. Thus, we added National Public Data to our report.
Findings in Kiteworks 2024 Sensitive Content Communications Privacy and Compliance Report further emphasize the critical nature of managing sensitive data across all sectors.2 The report underscores the challenges organizations face in protecting sensitive content as they increasingly rely on multiple communication tools and third-party interactions, which can create numerous vulnerabilities. For example, the report found that those with 10 or more communication tools experienced 3.55x more data breaches than the average number reported by the entire respondent cohort.
Key Trends in Data Breaches
When one looks underneath the hood of the Top 11 Data Breaches in 1H 2024, several different takeaways emerge:
- Ransomware Attacks: Ransomware continues to be a prevalent method of attack, targeting organizations across various sectors. High-profile breaches such as those involving Change Healthcare and MediSecure show the devastating impact ransomware can have, not only by disrupting operations but also by compromising sensitive data. These attacks have resulted in significant financial losses and operational disruptions, emphasizing the need for robust ransomware defense strategies.
- Massive Scale of Data Exposure: The volume of data exposed in breaches has escalated, with incidents involving millions of records becoming more common. For instance, AT&T suffered two major breaches that together compromised over 180 million customer records, including personal information and call logs. Similarly, the breach at Snowflake affected multiple companies and exposed hundreds of millions of records, illustrating the far-reaching threat of supply chain attacks in today’s interconnected digital landscape (corroborated by the findings in Verizon’s 2024 Data Breach Investigations Report where 15% of all attacks in the past year were connected to the supply chain).3
- Vulnerabilities Across Multiple Sectors: Data breaches are not confined to any one sector; instead, they impact a wide range of industries, each facing unique vulnerabilities. Sectors such as healthcare, finance, and technology are particularly at risk due to the sensitive nature of the data they handle and well represented in the top 10 data breaches in ITRC’s 1H 2024 report. The lack of governance tracking and controls as well as advanced security capabilities are key reasons. For example, the Kiteworks report highlights that 57% of organizations cannot track, control, and report on external content sends and shares.
- Emerging Threats From Third-party Risks and Internal Errors: Beyond external attacks, third-party risks and internal errors have also emerged as significant threats. The breaches at Kaiser and USPS, where sensitive information was inadvertently shared with advertisers, highlight the growing concern over internal data governance and the risks associated with third-party interactions. Tracking and controlling the flow to and from all the third parties with which organizations exchange data is difficult, with two-thirds of organizations reporting they exchange sensitive content with over 1,000 third parties.4
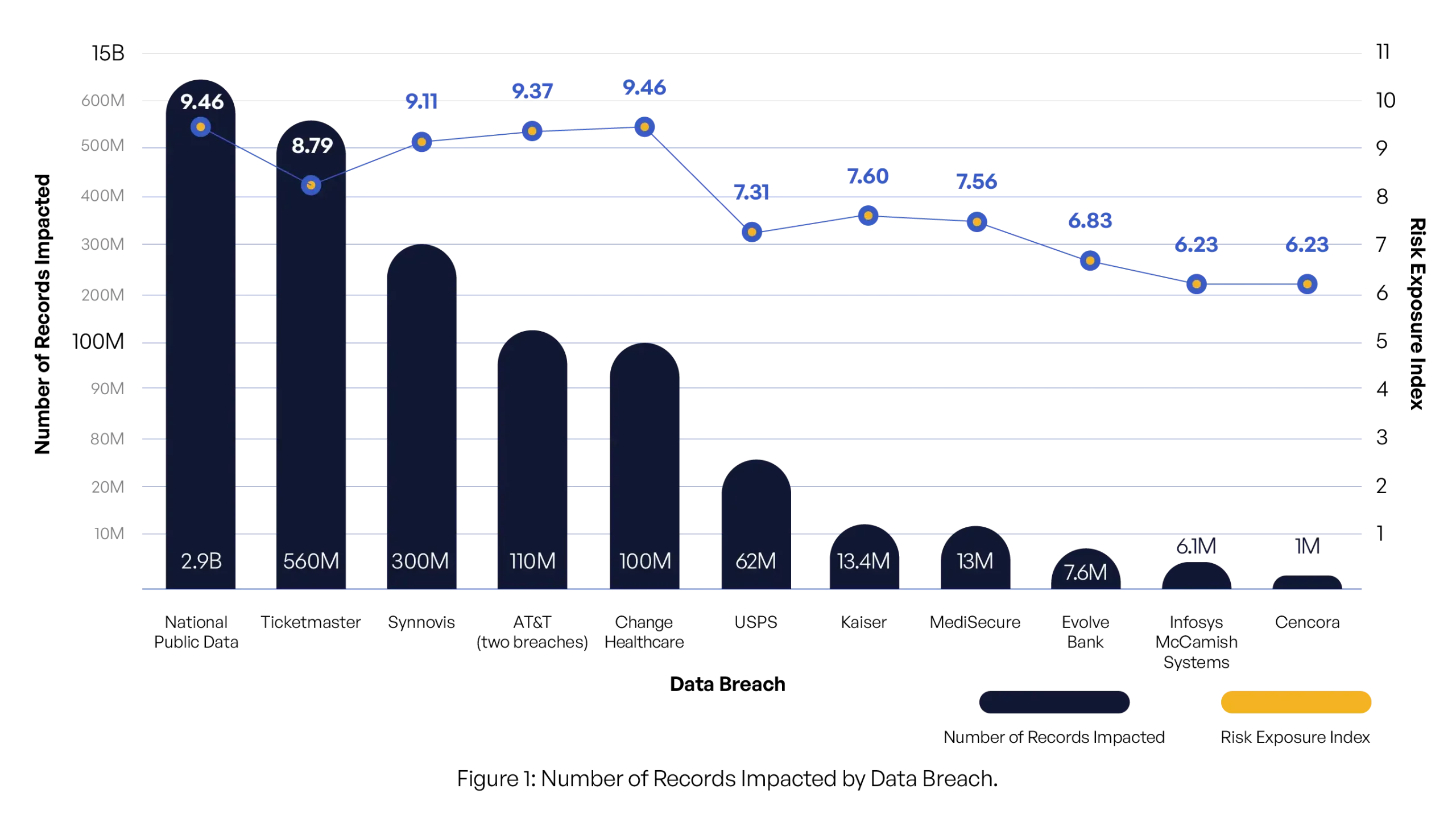
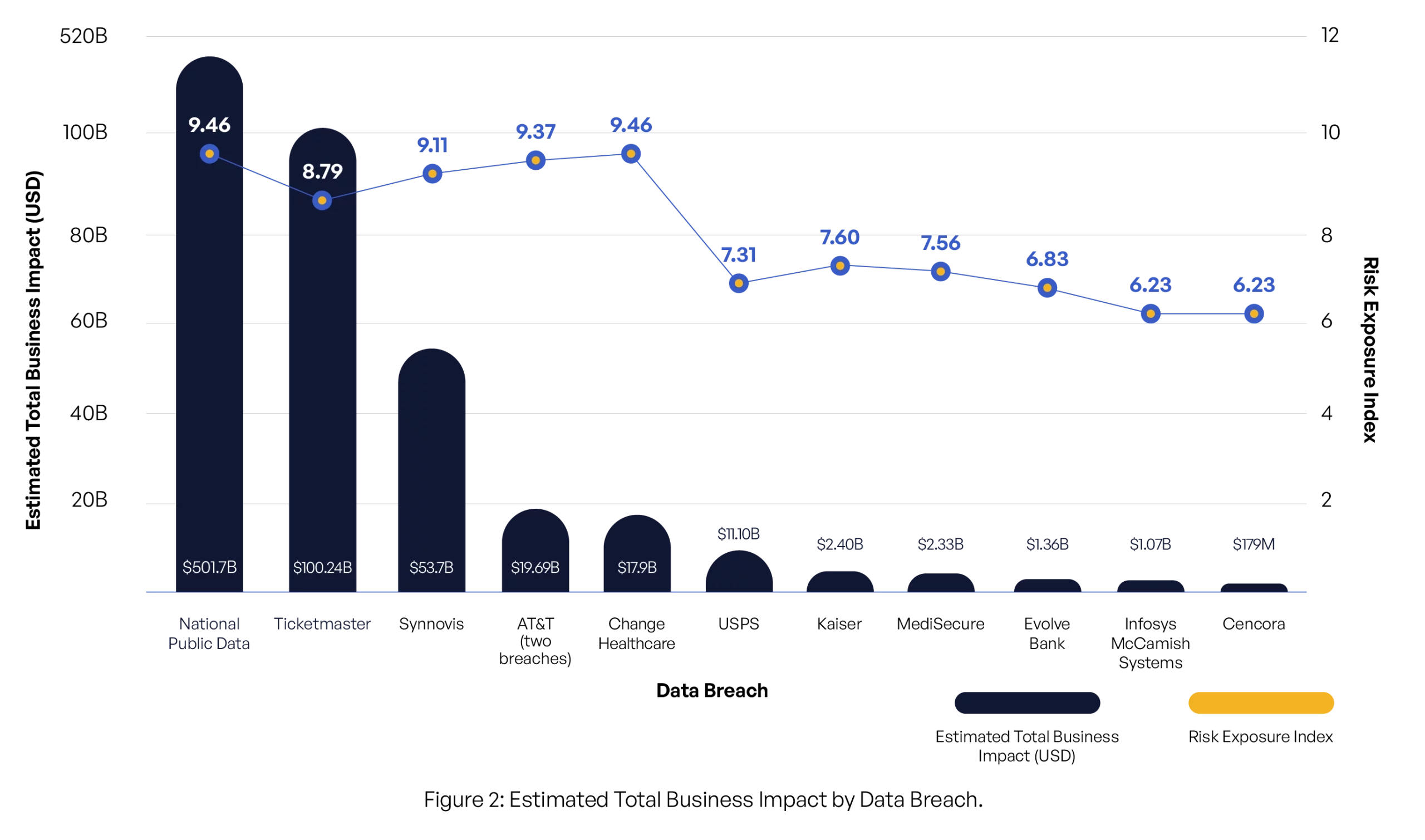
Data Breach Details
| Data Breach | Risk Exposure Index | Number of Records Impacted | Estimated Total Business Impact (USD) | Type of Data Converted | Regulatory Compliance Violations | Ransomware Demand |
|---|---|---|---|---|---|---|
| Change Healthcare | 9.46 | 100,000,000 | $17,900,000,000 | Personal, medical, billing information | HIPAA, HITECH Act, California CMIA, Texas Medical Records Privacy Act, HIPAA Security Rule, HIPAA Privacy Rule | Yes, unknown amount |
| National Public Data | 9.46 | 2,900,000,000 | $501,700,000,000 | Personal, social security numbers | FTC Act, GDPR, various US state data privacy laws such as CCPA | No |
| AT&T (two breaches) | 9.37 | 110,000,000 | $19,690,000,000 | Phone numbers, call records, personal information | FCC Regulations (CPNI), FTC Act, CCPA, NY SHIELD Act, GDPR, Telecommunications Act | Yes, undisclosed amount |
| Synnovis | 9.11 | 300,000,000 | $53,700,000,000 | Patient interaction data | UK Data Protection Act 2018, GDPR, NIS Regulations, UK NHS Data Security and Protection Toolkit | Yes, $50 million demanded |
| Ticketmaster | 8.79 | 560,000,000 | $100,240,000,000 | Full names, addresses, email addresses, phone numbers, payment card data | PCI DSS, FTC Act, CCPA, Massachusetts Data Breach Notification Law, GDPR | No |
| Kaiser | 7.60 | 13,400,000 | $2,398,600,000 | Website search terms, health information | HIPAA, HITECH Act, California CMIA, FTC Act, GDPR (if EU residents are involved) | No |
| MediSecure | 7.56 | 13,000,000 | $2,327,000,000 | Personal and health data | Australian Privacy Act, Healthcare Identifiers Act, state-specific health data regulations | Yes, unknown amount |
| USPS | 7.31 | 62,000,000 | $11,098,000,000 | Postal addresses, tracking data | CCPA, FTC Act, various state data breach notification laws, GDPR (if applicable) | No |
| Evolve Bank | 6.83 | 7,600,000 | $1,360,400,000 | Personal information | CCPA, GLBA (Gramm-Leach-Bliley Act), FTC Safeguards Rule, state financial data protection laws | Yes, unknown amount |
| Cencora | 6.23 | 1,000,000 | $179,000,000 | Health data | HIPAA, FDA regulations, state-specific medical privacy laws (e.g., California CMIA, Texas Medical Records Privacy Act) | No |
| Infosys McCamish Systems | 6.23 | 6,078,263 | $1,074,000,000 | Social security numbers, medical information, financial data | CCPA, GLBA, FTC Act, state insurance data protection laws, HIPAA (if applicable) | Yes, unknown amount |
Cost of Data Breaches
The increasing frequency and severity of data breaches underscore the urgent need for organizations to adopt advanced cybersecurity measures. IBM’s 2024 Cost of a Data Breach Report reveals the global average cost of a data breach rose by 10% over the past year, reaching $4.88 million.
The financial impact of data breaches on companies extends beyond immediate costs associated with detection, escalation, and notification. There are significant direct costs, such as regulatory fines, legal settlements, forensic investigations, and customer notification expenses. Organizations that fail to comply with data protection regulations like the General Data Protection Regulation (GDPR) or the Health Insurance Portability and Accountability Act (HIPAA) can face substantial fines. For example, as of March 1, 2024, the total sum of GDPR fines recorded was around €4.48 billion (USD 4.96 billion), an increase of €1.71 billion over the prior year. At the same time, the average cost of a GDPR violation increased from approximately €500,000 in 2019 to €4.4 million (USD 4.4 million) in 2023.
In addition to these global or national regulations, regional or state-level data privacy regulations such as the California Consumer Protection Act (CCPA) add greater complexity and challenges for businesses with operations in those locations.
Risk Factors Involved in Data Breaches
Volume and Type of Data Exposed
The risk factors associated with data breaches are significantly influenced by the volume and type of data exposed. In the first half of 2024, breaches varied widely in terms of the types of records compromised. Personal data is certainly a major target, with Verizon reporting that nearly 60% of data breaches involved personally identifiable information (PII), including names, addresses, social security numbers, and financial information such as credit card details.7 Health records, including sensitive patient information, were also highly targeted, particularly in breaches affecting healthcare organizations where the exposure of protected health information (PHI) added another layer of risk due to regulatory requirements like HIPAA.
Number of Victims
The scope of impact of a data breach is often determined by the number of affected individuals and entities. In the first half of 2024, several breaches affected millions of individuals across various sectors. For instance, breaches in the telecommunications and healthcare sectors had widespread effects, impacting tens of millions of customers and patients.
Sensitivity of Exposed Data
The sensitivity level of the data exposed is a critical factor in determining the severity and impact of a data breach. High-sensitivity data, such as social security numbers, health records, and financial information, poses a greater risk than low-sensitivity data like email addresses or general business information. Breaches involving high-sensitivity data are more likely to result in severe consequences, such as identity theft, financial fraud, and other malicious activities. In instances where sensitive financial information or health records are involved, resulting regulatory action and higher remediation costs due to the stringent requirements around data protection for these types of data is much greater.
Methods of Breach
Methods used in data breaches have evolved, reflecting the increasing sophistication of cybercriminal tactics. Common methods include ransomware attacks, phishing campaigns, insider threats, and exploiting vulnerabilities in third-party services or software. Ransomware remains a prevalent attack vector, where attackers encrypt data and demand a ransom for its release, often causing significant operational disruptions and financial losses.
Phishing attacks also continue to be a leading cause of breaches, leveraging social engineering techniques to deceive employees into disclosing sensitive information or granting unauthorized access. Exploiting vulnerabilities in third-party services or supply chain attacks is a growing trend. Specifically, breaches originating from third-party vulnerabilities can have extensive impacts, as they often involve multiple organizations and affect entire networks of business partners and customers. This trend underscores the need for robust third-party risk management practices and regular vulnerability assessments.
Discover the Risk Exposure Score of a Data Breach
Evaluate a data breach through the lens of six risk elements and generate a Risk Exposure Index Score to determine the overall risk of data breach. Get a score in less than one minute.
Development of the Risk Exposure Index
Introducing the Risk Exposure Index
The Risk Exposure Index is a strategic tool developed to evaluate and prioritize data breaches based on their severity and potential impact. In an era where data breaches are becoming increasingly frequent and complex, organizations face significant challenges in assessing the risk each breach poses to their operations, reputation, and regulatory compliance. The Risk Exposure Index aims to provide a standardized framework for quantifying and comparing the risks associated with different data breaches. By utilizing this index, organizations can prioritize their cybersecurity measures, allocate resources more effectively, and enhance their overall security posture by focusing on the most critical threats.
How the Risk Exposure Index Works
The Risk Exposure Index goes beyond traditional metrics such as the number of records exposed, or the financial cost incurred. Instead, it incorporates a range of factors to provide a more nuanced understanding of breach severity. These factors may include the type of data compromised, the extent of exposure, the potential for regulatory penalties, and the long-term impact on brand reputation. By aggregating these elements into a single, comprehensive score, the index allows organizations to objectively assess the severity of each breach and make informed decisions on where to focus their mitigation efforts.
Methodology for the Risk Exposure Index
The methodology for calculating the Risk Exposure Index involves several criteria, each contributing to the overall risk score of a breach. These criteria are carefully selected to provide a holistic view of the risks associated with a breach and include the following:
- Number of Records Exposed: This criterion assesses the volume of data compromised during a breach. The greater the number of records exposed, the higher the risk score, as larger breaches typically have more severe consequences, including increased potential for identity theft, fraud, and reputational damage.
- Estimated Financial Impact: This criterion evaluates the potential financial losses resulting from a breach, including direct costs such as fines, legal fees, and remediation expenses, as well as indirect costs like loss of business and reputational harm. Breaches with a higher estimated financial impact receive a higher score, reflecting the significant economic burden they impose on organizations.
- Ransomware Involvement: Given the rising threat of ransomware attacks, this criterion specifically accounts for breaches involving ransomware. Ransomware attacks are particularly disruptive, often causing significant operational downtime and requiring substantial recovery efforts. Breaches involving ransomware receive a higher score due to the complexity and severity of the response required.
- Data Sensitivity: The sensitivity of the data exposed during a breach is a critical factor in determining its risk level. Breaches involving highly sensitive data, such as protected health information (PHI) or financial records, are assigned higher scores. This reflects the increased risk of regulatory penalties, legal actions, and the need for comprehensive remediation efforts to protect affected individuals.
- Severity of the Breach: This criterion considers the overall impact of the breach on the affected organization, including operational disruption, customer trust, and long-term reputational damage. The severity is assessed based on the extent of the breach, the data involved, and the effectiveness of the organization’s response. More severe breaches are assigned higher scores to reflect their broader implications.
- Number of Regulations Impacted: This criterion evaluates the regulatory landscape affected by the breach. Breaches that violate multiple regulations, such as GDPR, HIPAA, or CCPA, receive higher scores. This reflects the complexity of managing compliance across different jurisdictions and the potential for multiple fines and legal actions.
Normalization Process and Score Adjustment
To ensure that the Risk Exposure Index provides a fair and consistent measure of breach severity, a normalization process is applied to adjust scores to a standardized 1-10 scale. This process involves several steps:
- Data Collection and Initial Scoring: Each breach is assessed against the six criteria outlined above, and an initial score is assigned for each criterion based on predefined ranges. For example, breaches exposing more than 10 million records may receive a maximum score for the “Number of Records Exposed” criterion.
- Weight Assignment: Each criterion is assigned a weight based on its relative importance in determining the overall risk level. For instance, “Data Sensitivity” and “Estimated Financial Impact” may be weighted more heavily than “Number of Records Exposed” to reflect their critical impact on the organization’s security posture and compliance requirements.
- Score Aggregation: The weighted scores for each criterion are aggregated to calculate a total risk score for each breach. This total score represents the overall severity of the breach based on the combination of all risk factors.
- Normalization: The total scores are then normalized to fit within a standardized 1-10 scale. This is achieved by applying a mathematical formula that adjusts the scores based on the maximum and minimum scores observed across all breaches. The normalization process ensures that the index provides a consistent and comparable measure of breach severity, regardless of the underlying data.
- Final Score Assignment: The normalized scores are reviewed and validated to ensure accuracy and consistency. Each breach is then assigned a final Risk Exposure Index on the 1-10 scale, with higher scores indicating more severe breaches that require immediate attention and action.
By employing this rigorous methodology, the Risk Exposure Index offers a reliable and actionable framework for assessing and managing data breach risks, enabling organizations to enhance their cybersecurity strategies and better protect their sensitive data from evolving threats.
Analysis of the Top 11 Data Breaches Based on the Risk Exposure Index
Following is the corrected ranking of the top 10 data breaches in the first half of 2024, based on their Risk Exposure Index
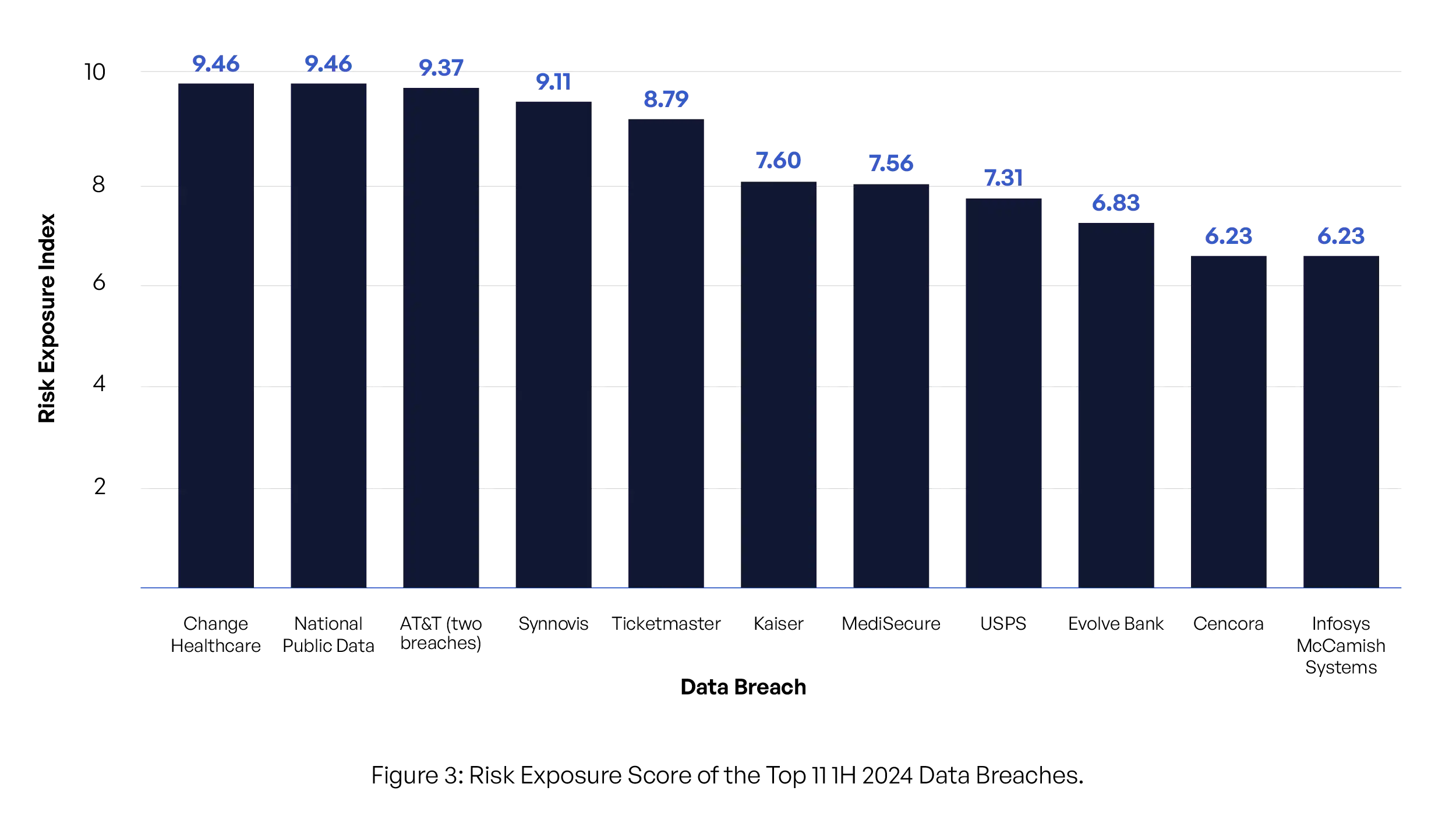
1. Change Healthcare (Risk Exposure: 9.46)
Description of the Incident: Change Healthcare experienced a ransomware attack that led to the theft of sensitive health data, including personal, medical, and billing information affecting 100 million records.
Impact Analysis: The breach had a severe financial impact, with costs associated with ransom payments, system restoration, and legal fees. Operational disruptions were significant, affecting patient care across various healthcare facilities. The reputational damage was extensive, resulting in a loss of trust among patients and partners.
Risk Exposure Breakdown:
Records Exposed:
100,000,000
Estimated Financial Impact:
$17,900,000,000
Data Sensitivity (1-5): 5
Financial Impact (1-5): 4
Regulatory Compliance (1-5): 5
2. National Public Data (Risk Exposure: 9.46)
Description of the Incident: The breach occurred on December 23, 2023. National Public Data, a data broker specializing in background checks and fraud prevention services, indicated that 2.9 billion records belonging to 1.3 million people were breached.
Impact Analysis: The information breached included social security numbers, names, email addresses, phone numbers, and mailing addresses.
Risk Exposure Breakdown:
Records Exposed:
2,900,000,000
Estimated Financial Impact:
$501,700,000,000
Data Sensitivity (1-5): 5
Financial Impact (1-5): 5
Regulatory Compliance (1-5): 4
3. AT&T (Risk Exposure: 9.37)
Description of the Incident: This breach involved the theft of 110 million customer records, including phone numbers, call records, and personal information, due to unauthorized access.
Impact Analysis: Significant financial costs arose from regulatory fines and customer notification expenses. The breach caused operational impacts, including service disruptions and heightened scrutiny of AT&T’s data-handling practices. Reputational damage led to decreased customer trust and increased churn.
For the second AT&T data breach, while the exact number of data records is not explicitly stated, it is reasonable to estimate that the total number of compromised data records across both breaches is significantly higher than 110 million, potentially in the billions given the nature of call and text records over a six-month period for such a large customer base.
Risk Exposure Breakdown:
Records Exposed:
110,000,000
Estimated Financial Impact:
$19,690,000,000
Data Sensitivity (1-5): 3
Financial Impact (1-5): 5
Regulatory Compliance (1-5): 5
4. Synnovis (Risk Exposure: 9.11)
Description of the Incident: Synnovis, a U.K. pathology lab, was targeted by a ransomware attack, compromising data related to 300 million patient interactions and disrupting medical services.
Impact Analysis: Financial impact included costs for service restoration and potential regulatory fines. The operational impact was substantial, with many medical procedures postponed, causing a critical incident in the healthcare sector. Reputational damage affected trust within the healthcare community.
Risk Exposure Breakdown:
Records Exposed:
300,000,000
Estimated Financial Impact:
$53,700,000,000
Data Sensitivity (1-5): 1
Financial Impact (1-5): 5
Regulatory Compliance (1-5): 4
5. Ticketmaster (Risk Exposure: 8.79)
Description of the Incident: The breach at Snowflake, affecting Ticketmaster, exposed 560 million customer records, including full names, addresses, email addresses, phone numbers, and payment card data.
Impact Analysis: Financial impacts included remediation costs and potential lawsuits. Operational impacts involved disruptions to customer services and enhanced security monitoring. Reputational damage affected Snowflake and its clients, raising concerns about cloud security.
Risk Exposure Breakdown:
Records Exposed:
560,000,000
Estimated Financial Impact:
$100,240,000,000
Data Sensitivity (1-5): 2
Financial Impact (1-5): 5
Regulatory Compliance (1-5): 5
6. Kaiser (Risk Exposure: 7.60)
Description of the Incident: Kaiser inadvertently shared private health information of 13.4 million patient records with advertisers due to tracking codes used on its website.
Impact Analysis: Financial impacts included regulatory fines and legal settlements. Operational impacts involved overhauling data governance and privacy practices. The breach caused significant reputational damage and raised concerns about data privacy.
Risk Exposure Breakdown:
Records Exposed:
13,400,000
Estimated Financial Impact:
$2,398,600,000
Data Sensitivity (1-5): 5
Financial Impact (1-5): 4
Regulatory Compliance (1-5): 5
7. MediSecure (Risk Exposure: 7.56)
Description of the Incident: MediSecure, an Australian prescriptions provider, suffered a ransomware attack compromising the personal and health data of nearly 13 million Australians.
Impact Analysis: Financial costs included ransom payments and legal fees. Operational impacts were significant, disrupting healthcare services and leading to insolvency. Reputational damage eroded trust among customers and partners.
Risk Exposure Breakdown:
Records Exposed:
13,000,000
Estimated Financial Impact:
$2,327,000,000
Data Sensitivity (1-5): 5
Financial Impact (1-5): 4
Regulatory Compliance (1-5): 3
8. USPS (Risk Exposure: 7.31)
Description of the Incident: USPS shared postal addresses of logged-in users with advertisers like Meta, LinkedIn, and Snap through tracking codes.
Impact Analysis: The breach resulted in financial costs from fines and settlements. Operational impacts included changes to data governance practices. Reputational damage resulted in increased scrutiny and concerns about privacy practices.
Risk Exposure Breakdown:
Records Exposed:
62,000,000
Estimated Financial Impact:
$11,098,000,000
Data Sensitivity (1-5): 1
Financial Impact (1-5): 4
Regulatory Compliance (1-5): 5
9. Evolve Bank (Risk Exposure: 6.83)
Description of the Incident: Evolve Bank, a banking-as-a-service provider, experienced a ransomware attack compromising the personal information of over 7.6 million people.
Impact Analysis: Financial impacts included ransom payments and regulatory fines. Operational disruptions were substantial, affecting customer services and leading to heightened security measures. Reputational damage was significant, affecting customer trust.
Risk Exposure Breakdown:
Records Exposed:
7,600,000
Estimated Financial Impact:
$1,360,400,000
Data Sensitivity (1-5): 3
Financial Impact (1-5): 3
Regulatory Compliance (1-5): 3
10. Infosys McCamish Systems (Risk Exposure: 6.23)
Description of the Incident: The breach involved the exposure of social security numbers, medical information, and financial data, impacting 6.1 million records.
Impact Analysis: Financial impacts included regulatory fines and costs associated with breach notification. Operational impacts involved enhanced security measures and improved data protection practices. Reputational damage affected customer trust and partner relationships.
Risk Exposure Breakdown:
Records Exposed:
6,078,263
Estimated Financial Impact:
$1,074,000,000
Data Sensitivity (1-5): 5
Financial Impact (1-5): 2
Regulatory Compliance (1-5): 5
11. Cencora (Risk Exposure: 6.23)
Description of the Incident: The data breach involved the exposure of sensitive health data that included patient health records and other confidential medical data, impacting approximately 1 million records. This supply chain attack affected data records for at least 27 pharmaceutical and biotechnology companies.
Impact Analysis: The breach led to significant financial costs, including regulatory fines and the expenses associated with notifying affected individuals and implementing additional cybersecurity measures to prevent future breaches. The financial implications also extended to legal fees and potential settlements with impacted parties.
Risk Exposure Breakdown:
Records Exposed:
1,000,000
Estimated Financial Impact:
$179,000,000
Data Sensitivity (1-5): 5
Financial Impact (1-5): 2
Regulatory Compliance (1-5): 5
Using the Risk Exposure Index
Our Risk Exposure Index takes into account more than just the number of records exposed or the number of victims impacted. This comprehensive approach provides a clearer understanding of the true severity and potential impact of each breach. While a larger number of exposed records can indicate a significant breach, it does not necessarily mean that the risk exposure is higher. Several factors contribute to a breach’s risk score, which can sometimes result in a breach with fewer records having a higher risk score than one with more records.
1. Nature and Sensitivity of the Data Involved
The type of data compromised is a critical factor influencing the Risk Exposure Index. For example, the breach at Change Healthcare, which involved 100 million records, primarily affected personal, medical, and billing information. This type of data is highly sensitive, leading to severe implications, such as the irreversible loss of health data, which elevates the risk exposure despite a smaller number of records compared to other breaches. Similarly, the Cencora breach, with only 1 million records exposed, also scored high on the risk scale due to the sensitivity of the health data involved, demonstrating that the nature of the data is often more crucial than the volume of data.
2. Regulatory and Compliance Implications
Regulatory implications can significantly impact the overall risk exposure of a breach. For instance, the AT&T breach, which involved 110 million records, had a substantial risk exposure not only because of the number of records but also due to the potential violations of multiple regulations, including the FCC Regulations, FTC Act, and CCPA. These regulatory violations can lead to significant fines and penalties, increasing the breach’s overall risk score. In contrast, a breach involving a larger number of records, such as Ticketmaster with 560 million records, might have a lower risk exposure if the compromised data does not invoke as severe regulatory consequences.
3. Potential Impact Beyond Immediate Losses
The long-term consequences of a data breach, such as identity theft, financial fraud, or reputational damage, are also considered in the Risk Exposure Index. The Synnovis breach, which involved 300 million records of patient interaction data, is an example where the long-lasting impact on patient services and trust resulted in a high risk score. Even though the number of records was lower than the Ticketmaster breach, the potential for sustained harm to patients and healthcare services significantly heightened the risk exposure. This example shows that the index accounts for the broader implications of a breach beyond the immediate loss of data.
4. Ransomware and Extortion Factors
The presence of ransomware demands can also elevate a breach’s risk score, regardless of the number of records exposed. The Synnovis breach, for example, faced a $50 million ransomware demand, which contributed to its high risk score. Even with fewer records involved than the Ticketmaster breach, the additional costs and risks associated with ransom demands, including potential double extortion and recovery expenses, increase the breach’s overall risk exposure.
5. The Impact of Data Sensitivity and Potential for Identity Theft
The impact of data sensitivity is evident in breaches such as those experienced by companies like Change Healthcare and Synnovis, where data types involved included highly sensitive medical and personal information. The potential for misuse, such as identity theft and financial fraud, significantly contributes to the higher risk exposure of these breaches, even when compared to breaches involving a greater volume of less sensitive data, such as the one experienced by Ticketmaster.
Concluding Thoughts
Our analysis of the top 11 data breaches in the first half of 2024 reveals several critical insights into the evolving landscape of cybersecurity threats:
- Diverse Attack Vectors and Rising Sophistication: Cybercriminals continue to employ a variety of attack methods, from ransomware and unauthorized access to inadvertent data sharing, each with unique implications for security strategies. This diversity in attack vectors underscores the importance for organizations to adopt a multi-layered security approach that addresses a wide range of potential threats.
- Significant Impact of Ransomware: Ransomware attacks, particularly those targeting high-value sectors like healthcare and finance, have proven to be both disruptive and costly. Breaches such as those involving Change Healthcare and Synnovis have demonstrated the severe operational, financial, and reputational damages that can result. Organizations must prioritize robust ransomware defenses, including advanced threat detection, rapid response capabilities, and comprehensive data backup strategies.
- High Sensitivity and Volume of Exposed Data: Data breaches involving large volumes of sensitive information, especially personal and financial data, have consistently resulted in higher risk scores due to their potential for identity theft, financial fraud, and regulatory penalties. This highlights the need for enhanced data protection measures, particularly for organizations, such as National Public Data, that handle sensitive data across multiple communication tools and platforms.
- Third-party and Supply Chain Vulnerabilities: Several breaches, such as those affecting AT&T and Ticketmaster, have highlighted the vulnerabilities associated with third-party vendors and supply chain partners. This emphasizes the critical need for continuous monitoring and robust management of third-party relationships to mitigate risks associated with extended networks.
- Regulatory Compliance and Legal Repercussions: The analysis shows that data breaches often result in violations of multiple regulations, leading to substantial fines and legal consequences. Organizations must strengthen their compliance frameworks and data governance practices to avoid regulatory infractions and associated financial penalties.
- Holistic Risk Assessment: The report findings underscore the importance of considering multiple factors when assessing the risk exposure of a data breach. It is not solely about the number of records breached or the immediate financial cost; the true risk is often shaped by a combination of elements, including the sensitivity of the compromised data, the potential for regulatory violations, and the broader implications for long-term reputational damage.
- Contextual Impact of Breach Type and Data Sensitivity: Findings highlight that the type of breach and the sensitivity of the data involved are critical factors influencing the overall risk exposure. For instance, a breach involving a small number of highly sensitive records, such as social security numbers or medical records, can have more severe consequences than a breach involving a large volume of less sensitive data. This demonstrates that organizations must assess the context and content of the data breached, not just the quantity, to understand the potential impacts fully.
Actionable Recommendations
- Adopt Hardened Security Postures: Organizations should enhance their cybersecurity frameworks with hardened security measures tailored to protect sensitive content communications. This includes deploying advanced security capabilities such as intrusion detection and prevention systems, secure communication channels, and continuous threat monitoring to prevent unauthorized access and mitigate potential breaches.
- Implement Advanced Encryption Techniques: To ensure the privacy and security of sensitive data, organizations should utilize advanced encryption methods for data at rest, in transit, and in use. Encrypting sensitive content communications helps prevent unauthorized access and data breaches, ensuring compliance with regulatory requirements and safeguarding sensitive information.
- Deploy Next-gen Digital Rights Management (DRM): Organizations should implement robust digital rights management strategies to control and monitor access to sensitive content. This includes defining access rights, tracking document usage, and applying controls to prevent unauthorized sharing or misuse of sensitive information, thereby reducing the risk of data breaches and ensuring compliance with data protection regulations.
- Enhance Third-party Risk Management Practices: Regularly assess and monitor the security practices of third-party vendors and partners to mitigate risks associated with extended networks. This includes enforcing stringent security requirements for third-party interactions and implementing secure communication protocols to protect sensitive data shared with external entities.
- Focus on Data Sensitivity and Compliance: Strengthen data protection practices by prioritizing the security of highly sensitive information through access controls, encryption, and comprehensive monitoring. Ensure compliance with data privacy regulations by regularly auditing data-handling practices and maintaining robust governance frameworks to protect sensitive content communications.
Future Outlook
As cyber threats continue to evolve in complexity and scope, organizations must remain vigilant and proactive in their cybersecurity efforts. The growing reliance on digital platforms and third-party services will likely increase the attack surface, making comprehensive risk management more critical than ever. By leveraging tools like the Risk Exposure Index and adopting a forward-looking approach to cybersecurity, organizations can better protect themselves against future breaches and minimize potential impacts.

Risk Exposure Index Algorithm
Scoring Criteria
- Number of Records Exposed:
- Over 100,000,000: 6 points
- 10,000,001-100,000,000: 5 points
- 1,000,001-10,000,000: 4 points
- 100,001-1,000,000: 3 points
- 10,001-100,000: 2 points
- 1-10,000: 1 point
- Estimated Financial Impact:
- Over $10,000,000,000: 6 points
- $1,000,000,001-$10,000,000,000: 5 points
- $100,000,001-$1,000,000,000: 4 points
- $10,000,001-$100,000,000: 3 points
- $1,000,001-$10,000,000: 2 points
- $1-$1,000,000: 1 point
- Ransomware Involvement:
- Yes: 1 point
- No: 0 points
- Data Sensitivity:
- 5 points (Extremely Sensitive Data): Breaches involving highly confidential information such as social security numbers, medical records, biometric data, or highly confidential corporate data that could cause severe harm or irreparable damage if exposed.
- 4 points (Highly Sensitive Data): Breaches involving more sensitive information like financial details (credit card numbers, bank account details), health information, or data that could lead to identity theft or fraud.
- 3 points (Sensitive Data): Breaches involving personally identifiable information (PII) like email addresses, phone numbers, or other personal details that could potentially be used for phishing or spam.
- 2 points (Moderate Sensitivity): Data that includes non-public, less sensitive information such as names, addresses, or contact information that can be easily obtained but does not pose a significant risk if exposed.
- 1 point (Low Sensitivity): Breaches involving data that is not sensitive or publicly available, such as generic or anonymized datasets that do not contain any PII or sensitive personal data.
- Severity:
- 5 points (Critical Impact): Catastrophic impact with severe financial repercussions, major public health risks, widespread identity theft, or a severe reputational blow leading to a lasting loss of trust.
- 4 points (High Impact): Significant consequences, including extensive identity theft, fraud cases, substantial financial losses, or regulatory fines.
- 3 points (Moderate Impact): Moderate harm, such as limited financial losses or reputational damage, some identity theft cases, or moderate regulatory scrutiny.
- 2 points (Low Impact): Minor disruptions, minimal financial impact, or limited exposure with no significant harm to individuals or organizational operations.
- 1 point (Minimal Impact): Breaches with little to no impact on the organization or individuals, perhaps due to timely containment or lack of valuable data exposure.
- Number of Regulations Impacted:
- 5 or more regulations: 5 points
- 4 regulations: 4 points
- 3 regulations: 3 points
- 2 regulations: 2 points
- 1 regulation: 1 point
Algorithm Details
- Sum up the points from all six criteria.
- Divide the sum by 2.8 to normalize the score to a 1-10 scale.
- Round the result to two decimal places.

Legal Disclaimer:
This research report includes findings derived with the assistance of algorithmic analysis and artificial intelligence (AI) technologies. Please note the following:
Experimental Nature: The AI and algorithmic methods used in this research are experimental. While we have made efforts to ensure accuracy, we cannot guarantee the complete reliability or efficacy of these technologies.
Not Professional Advice: The findings presented in this report do not constitute professional, legal, financial, or any other form of expert advice. Readers should not rely solely on these results for making important decisions.
Potential for Errors: Despite our best efforts, the AI and algorithms used may contain errors, biases, or inaccuracies. The results should be interpreted with caution and verified independently where critical.
Limitations of AI: The AI systems used have inherent limitations and may not account for all variables or specific circumstances relevant to individual cases.
Human Oversight: While AI and algorithms were utilized, human researchers have reviewed and interpreted the results. However, this does not guarantee the absence of errors or biases.
No Liability: We disclaim all liability for any losses, damages, or consequences that may arise from the use or misuse of the information presented in this report.
Continuous Development: AI and algorithmic technologies are rapidly evolving. The methods used in this research may be subject to future improvements or revisions.
By accessing and using this research report, you acknowledge that you have read, understood, and agreed to these terms and conditions.
- “2023 Data Breach Report,” Identity Theft Resource Center, January 2024.
- “Cost of a Data Breach Report 2024,” IBM, July 2024.
- “2024 Data Breach Investigations Report,” Verizon, April 2024.
- “Privacy in Practice 2024,” ISACA, January 2024.
- “Cost of a Data Breach Report 2024,” IBM, July 2024.
- “Enforcement Tracker Database,” CMS, accessed September 2, 2024.
- “2024 Data Breach Investigations Report,” Verizon, May 2024.