
Data Sovereignty for Higher Education Institutions
In today’s digital age, data has become a critical asset for institutions across various sectors, including higher education. As universities and colleges collect and store vast amounts of data, it becomes imperative to address the concept of data sovereignty. Understanding the importance of data sovereignty and its applications within the higher education context can greatly benefit these institutions. This article delves into the concept of data sovereignty, its role in higher education, challenges in implementation, strategies for achieving data sovereignty, and the future of data sovereignty in higher education.
What Data Compliance Standards Matter?
Data Sovereignty Explained
Data sovereignty refers to the concept of an organization maintaining ownership and control over the data it collects and stores. It is about ensuring that data remains within the jurisdiction and control of the institution that owns it, rather than being subject to external influences. In an era where privacy and security are paramount, data sovereignty takes center stage as a crucial element in safeguarding sensitive information.
Data sovereignty goes beyond just physical storage location. It encompasses legal, regulatory, and technological aspects that protect data integrity, availability, and confidentiality. By understanding and implementing data sovereignty practices, higher education institutions can safeguard their data and ensure compliance with relevant laws and regulations, like the United States’ Family Educational Rights and Privacy Act (FERPA).
Definition and Importance of Data Sovereignty
Data sovereignty refers to the principle that data is subject to the laws and regulations of the jurisdiction in which it is stored or processed. It signifies the institution’s control over its data, providing the freedom and flexibility to determine how and where the data is stored, accessed, and utilized.
Ensuring data sovereignty is essential for higher education institutions due to several reasons. Firstly, it safeguards the privacy and confidentiality of sensitive information, such as student records, research data, and intellectual property. By maintaining control over their data, institutions can prevent unauthorized access and data breaches.
Secondly, data sovereignty enables institutions to comply with legal and regulatory requirements specific to each country or region. By having jurisdictional control over data, institutions can ensure compliance with data protection laws, intellectual property rights, and government regulations.
Lastly, data sovereignty enhances the institution’s ability to leverage its data for research, analysis, and decision-making purposes. Institutions can efficiently manage and analyze data without concerns about data privacy, access restrictions, or latency issues.
Data Sovereignty in the Context of Higher Education
Higher education institutions generate and handle large volumes of sensitive data, including student information, research data, and academic records. Ensuring data sovereignty in the higher education context is crucial for several reasons.
Firstly, student information, including personal and academic data, must be protected to maintain privacy and comply with data protection regulations. With data sovereignty, institutions can establish robust systems and protocols to protect student information from unauthorized access, breaches, and misuse.
Secondly, research data represents a valuable asset for higher education institutions. Protecting research data through data sovereignty ensures integrity and confidentiality, promoting innovation, collaboration, and academic excellence.
Moreover, data sovereignty plays a vital role in facilitating international collaborations. Higher education institutions often collaborate with international partners, students, and researchers worldwide. Data sovereignty ensures that data generated, managed, and shared across borders complies with the applicable laws and regulations of each participating jurisdiction.
Moreover, data sovereignty plays a vital role in facilitating international collaborations. Higher education institutions often collaborate with international partners, students, and researchers worldwide. Data sovereignty ensures that data generated, managed, and shared across borders complies with the applicable laws and regulations of each participating jurisdiction.
In total, data sovereignty is a critical concept for higher education institutions. It provides control, privacy, and compliance with legal and regulatory requirements. By embracing data sovereignty, institutions can protect sensitive information, foster innovation, and facilitate international collaborations, ultimately contributing to academic excellence and advancement.
Data Sovereignty’s Role in Higher Education
Data sovereignty plays a pivotal role in higher education, enabling institutions to enhance research capabilities and protect student information effectively.
Higher education institutions are constantly striving to push the boundaries of knowledge through research. Research is a driving force in these institutions, contributing to advancements in various disciplines. However, conducting research involves handling vast amounts of data, which can be sensitive and valuable. Ensuring data sovereignty provides researchers with confidence that their data is secure and protected, fostering a conducive environment for innovation, collaboration, and knowledge creation.
By implementing robust data governance frameworks, institutions can confidently store, share, and access research data, both internally and externally, while maintaining data security and compliance. These frameworks include measures such as encryption, access controls, and regular audits to ensure that research data remains confidential and protected from unauthorized access or breaches. With data sovereignty in place, researchers can focus on their work without worrying about the security and integrity of their data.
Enhancing Research Capabilities
Research is a driving force in higher education institutions, contributing to advancements in various disciplines. Ensuring data sovereignty provides researchers with confidence that their data is secure and protected, fostering a conducive environment for innovation, collaboration, and knowledge creation. By implementing robust data governance frameworks, institutions can confidently store, share, and access research data, both internally and externally, while maintaining data security and compliance.
Moreover, data sovereignty enables institutions to leverage the power of data analytics and artificial intelligence (AI) in research. With secure and sovereign data, researchers can harness the potential of these technologies to analyze large datasets, identify patterns, and gain valuable insights. This, in turn, leads to more accurate and impactful research outcomes, benefiting not only the institution but also the broader academic community and society as a whole.
Furthermore, data sovereignty facilitates collaboration between institutions and researchers across geographical boundaries. With secure data storage and sharing mechanisms in place, researchers can collaborate seamlessly, regardless of their physical location. This opens up opportunities for interdisciplinary research, bringing together experts from different fields to tackle complex problems and drive innovation.
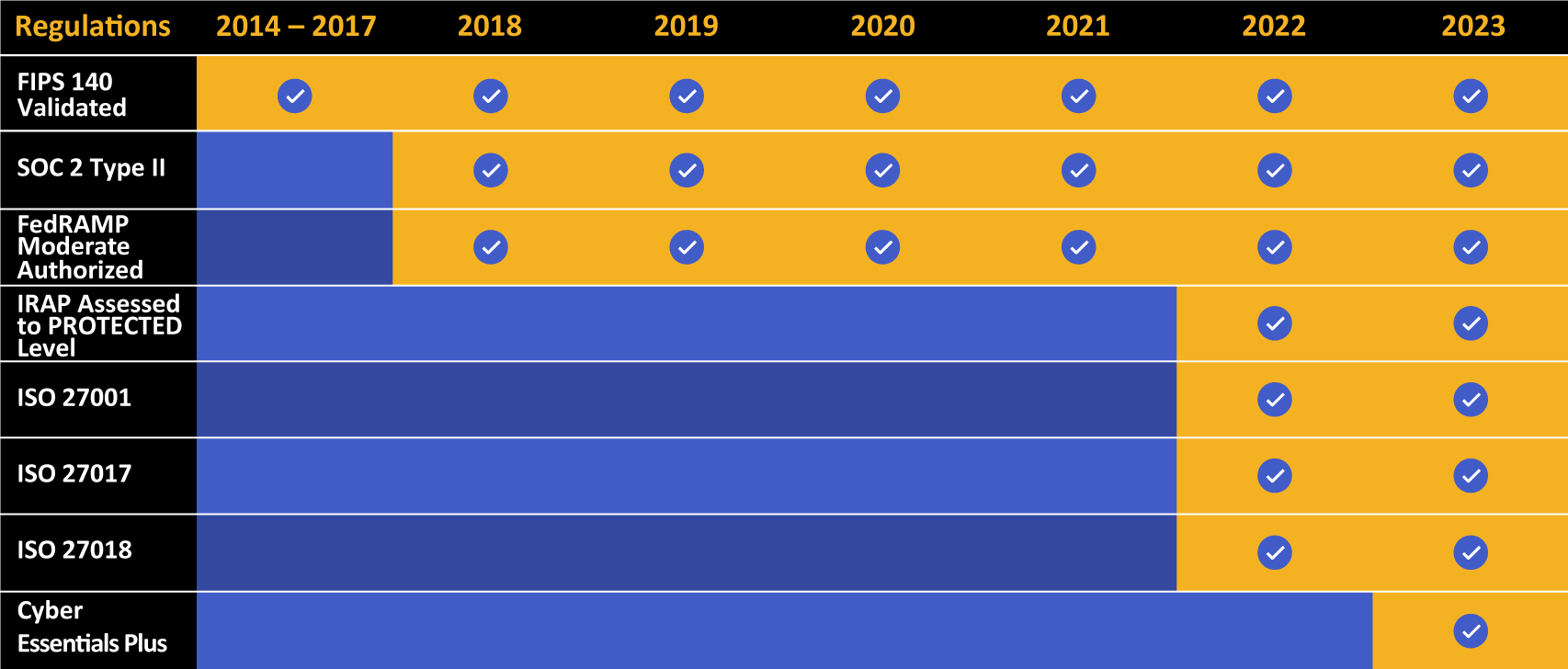
Kiteworks touts a long list of compliance and certification achievements.
Protecting Student Information
Higher education institutions are entrusted with vast amounts of sensitive student information, including personal details, educational records, and financial data. Data sovereignty is instrumental in protecting this information from unauthorized access, breaches, and misuse. By implementing comprehensive data protection measures and protocols, institutions can safeguard student information, ensuring compliance with laws, regulations, and ethical standards.
Data sovereignty allows institutions to tailor their security measures to suit the unique requirements of the student population they serve. For example, institutions can implement multi-factor authentication systems to ensure that only authorized individuals can access student information. They can also employ data encryption techniques to protect data at rest and in transit, making it virtually impossible for unauthorized parties to decipher the information.
In addition to protecting student information from external threats, data sovereignty also helps institutions maintain data integrity and prevent internal data breaches. By implementing strict access controls and monitoring mechanisms, institutions can ensure that only authorized personnel have access to student data. Regular audits and assessments can also be conducted to identify and address any vulnerabilities in the data protection infrastructure.
In conclusion, data sovereignty plays a crucial role in higher education by enhancing research capabilities and protecting student information. By implementing robust data governance frameworks, institutions can foster an environment of innovation and collaboration while ensuring the security and integrity of research data. Furthermore, data sovereignty enables institutions to safeguard sensitive student information from unauthorized access and breaches, ensuring compliance with laws and regulations. As technology continues to evolve, data sovereignty will remain a critical aspect of higher education, enabling institutions to navigate the complex landscape of data management and security.
Challenges in Implementing Data Sovereignty
While data sovereignty holds immense benefits for higher education institutions, it also comes with its share of challenges.
Legal and Regulatory Hurdles
Implementing data sovereignty practices requires institutions to navigate complex legal and regulatory landscapes. Different jurisdictions may have varying laws and regulations governing data privacy, protection, and cross-border data transfers. Complying with these requirements can be challenging, especially for institutions operating in multiple countries or collaborating with international partners. Institutions need to establish a robust legal framework that ensures compliance while allowing them to maintain data sovereignty.
Technological Constraints
Implementing data sovereignty necessitates the use of sophisticated technological infrastructure and tools. This can be challenging for institutions that lack adequate resources or face technological limitations. Additionally, migrating data to a secure infrastructure while minimizing disruptions and ensuring accessibility can be a complex task. Institutions need strategic planning, investment, and coordination among various stakeholders to overcome these technological constraints.
Strategies for Achieving Data Sovereignty
To achieve data sovereignty, higher education institutions can implement several strategies.
Developing a Comprehensive Data Governance Framework
A comprehensive data governance framework forms the foundation for successful data sovereignty implementation. This involves developing policies, procedures, and protocols that encompass data collection, processing, storage, access, and sharing. The framework should address legal and regulatory requirements while taking into account the unique needs of the institution and the stakeholders involved. Regular audits, training programs, and awareness campaigns can ensure consistent adherence to the framework and help maintain data sovereignty.
Leveraging Technology for Data Protection
Technological advancements offer solutions to address data sovereignty challenges effectively. Institutions can invest in secure storage solutions, encryption techniques, access management systems, and data backup mechanisms to protect data and ensure data sovereignty. Implementing identity and access management protocols ensures that only authorized individuals have access to specific data sets. Furthermore, regular updates, patches, and security enhancements of software and hardware infrastructure are essential to maintain data integrity and safeguard data sovereignty.
The Future of Data Sovereignty in Higher Education
The landscape of data sovereignty in higher education continues to evolve, driven by emerging trends and innovations.
Emerging Trends and Innovations
Technologies such as blockchain and distributed ledger systems hold immense potential in supporting data sovereignty efforts. These technologies offer secure and decentralized storage solutions, ensuring data integrity and transparency. By leveraging emerging technologies, institutions can build robust data ecosystems that enhance data sovereignty, streamline data management processes, and foster trust among stakeholders.
Preparing for the Future: Recommendations for Higher Education Institutions
As the importance of data sovereignty in higher education grows, institutions must take proactive steps to ensure they are prepared for the future. This includes conducting regular audits and assessments to identify potential vulnerabilities and opportunities for improvement. Collaborative efforts with industry experts, policymakers, and regulatory bodies can help institutions navigate complex legal and regulatory frameworks effectively.
In addition, investing in ongoing training programs for faculty, staff, and students on data privacy, security, and data sovereignty best practices can cultivate a culture of data protection and awareness. By developing strong partnerships with technology vendors and service providers, institutions can stay updated on the latest advancements and solutions in data sovereignty.
Kiteworks Helps Higher Education Institutions Comply with Data Sovereignty Requirements
Data sovereignty plays a vital role in safeguarding sensitive information, enhancing research capabilities, and ensuring compliance with legal and regulatory requirements in higher education institutions. While challenges exist, implementing comprehensive data governance frameworks and leveraging technology can pave the way for successful data sovereignty implementation. By embracing emerging trends and adopting proactive measures, institutions can prepare themselves for the future, where data sovereignty will remain crucial to their success in the digital world.
The Kiteworks Private Content Network, a FIPS 140-2 Level 1 validated secure file sharing and file transfer platform, consolidates email, file sharing, web forms, SFTP and managed file transfer, so organizations control, protect, and track every file as it enters and exits the organization.
Kiteworks plays a crucial role in higher education institutions’ data sovereignty efforts. For example, Kiteworks’ encryption and access control features protect personal information during cross-border transfers, ensuring secure transmission.
Kiteworks’ extensive deployment options, including private, hybrid, and FedRAMP virtual private cloud, can be configured to store data in specific geographic locations. By storing data in specific locations, organizations can ensure that they are adhering to the data sovereignty laws of the countries in which they operate.
Kiteworks also supports data portability requirements by enabling users to securely access, transfer, and download their personal information. Kiteworks also provides organizations with the ability to establish opt-in mechanisms and procedures for data collection, detailed consent forms, and minor consent procedures. These features help organizations comply with consent requirements, which are a key aspect of data sovereignty.
Finally, Kiteworks’ detailed audit trail enables organizations to prove their compliance with data sovereignty laws to auditors.
With Kiteworks: control access to sensitive content; protect it when it’s shared externally using automated end-to-end encryption, multi-factor authentication, and security infrastructure integrations; see, track, and report all file activity, namely who sends what to whom, when, and how.
Finally demonstrate compliance with regulations and standards like GDPR, HIPAA, CMMC, Cyber Essentials Plus, IRAP, and many more.
To learn more about Kiteworks, schedule a custom demo today.
Additional Resources
- Brief Expand Visibility and Automate Protection of All Sensitive Email
- Brief Navigate the Digital Trifecta of Data Sovereignty, Cybersecurity, and Compliance With Kiteworks
- Blog Post Data Sovereignty and GDPR [Understanding Data Security]
- Video What Is Email Security? How to Protect Your Sensitive Content With Email Security
- Brief Secure Protocol Package: Strengthening Data Exchange With SFTP and SMTP