Granular Access Controls and Comprehensive Auditing for HIPAA Privacy Compliance
Kiteworks offers granular access controls and role-based permissions for precise user management, ensuring HIPAA Privacy Rule compliance. Enhanced security is achieved through specific access rights based on job functions. Comprehensive auditing and reporting provide valuable audit logs, meeting HIPAA requirements and identifying potential risks. Kiteworks ensures reliable data backup and recovery using redundant, geographically distributed centers, maintaining patient information’s availability and integrity. With Kiteworks, experience enhanced privacy, compliance, and effective safeguarding of patient information in a secure, collaborative environment.
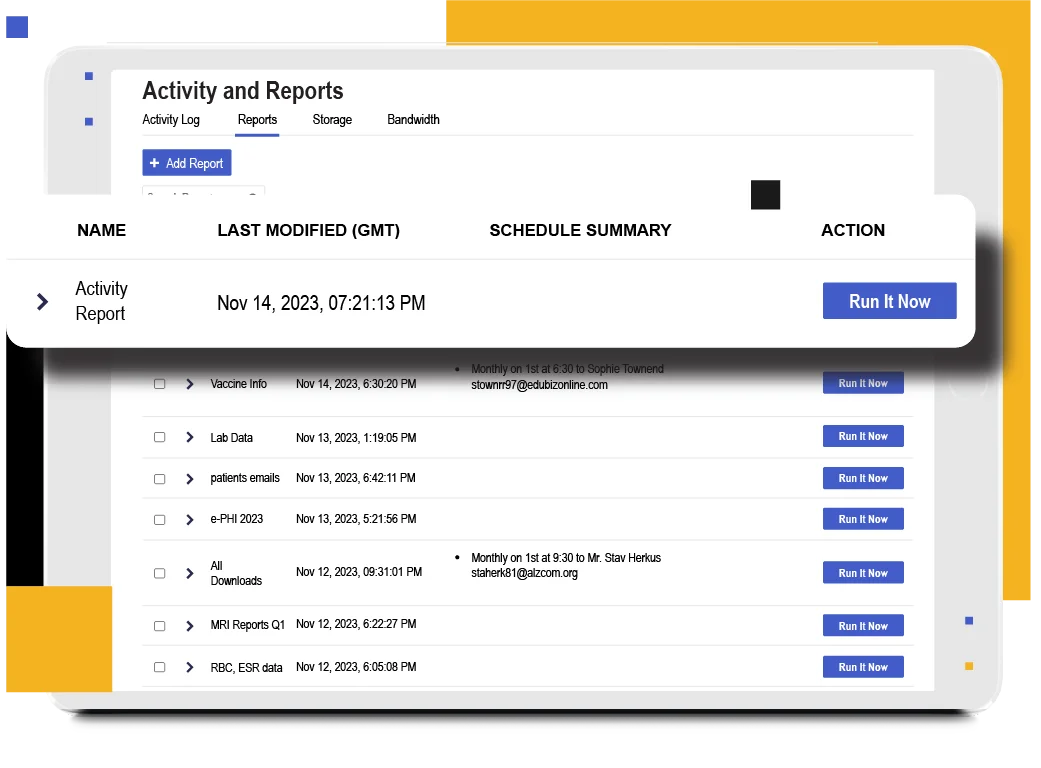
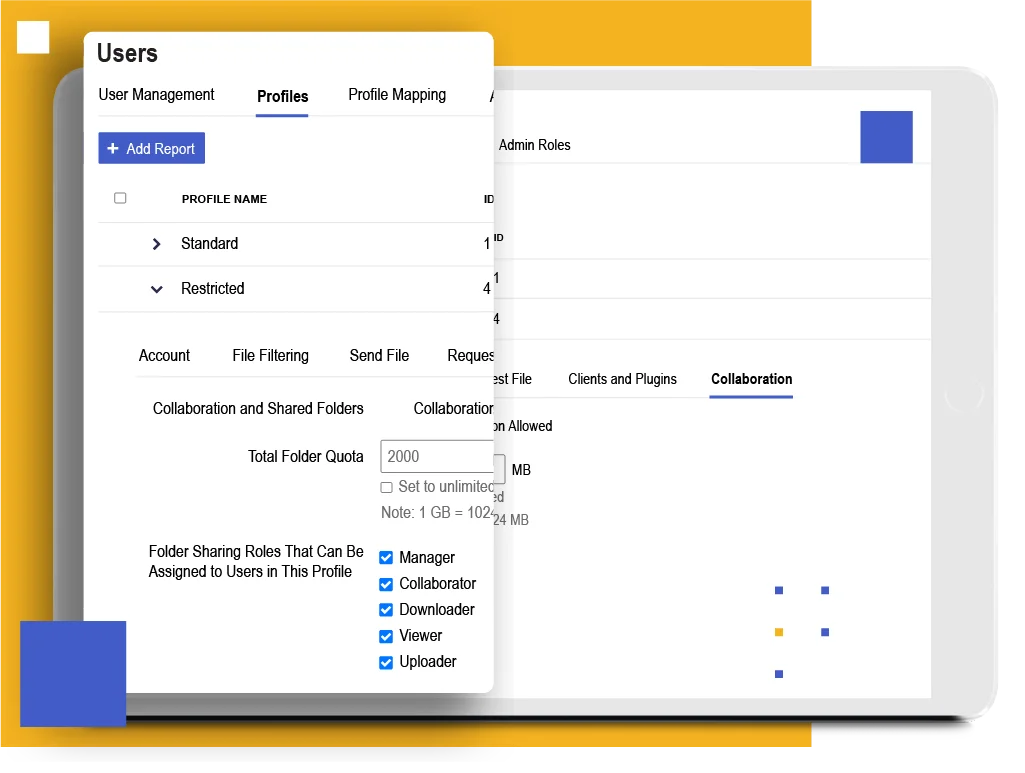
Robust Safeguards for Secure Patient Data Protection
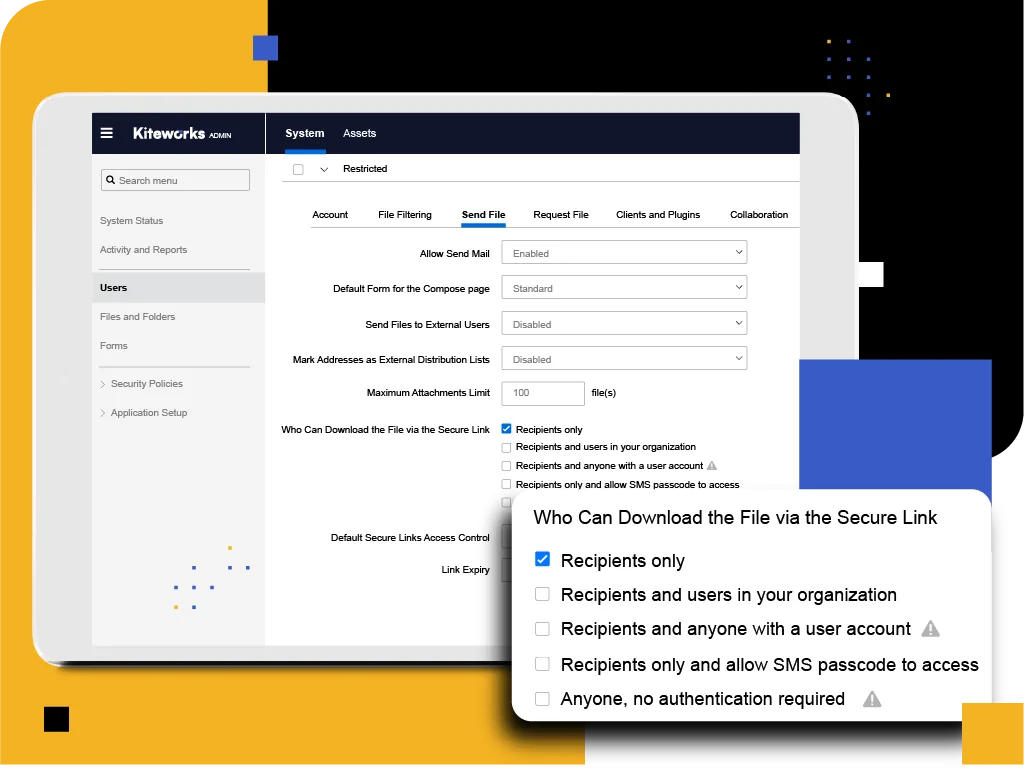
Kiteworks delivers robust HIPAA Security Rule safeguards, including centralized user access, permission management, and activity monitoring tools. The platform supports customized security policies and procedures, empowering healthcare organizations to establish tailored security programs. Secure data access to patient data from any device minimizes unauthorized access and physical device theft risks. Kiteworks ensures data security through encryption for data in transit and at rest, utilizing SSL/TLS and AES-256 protocols, which effectively helps organizations meet technical safeguards requirements and protect patient data.
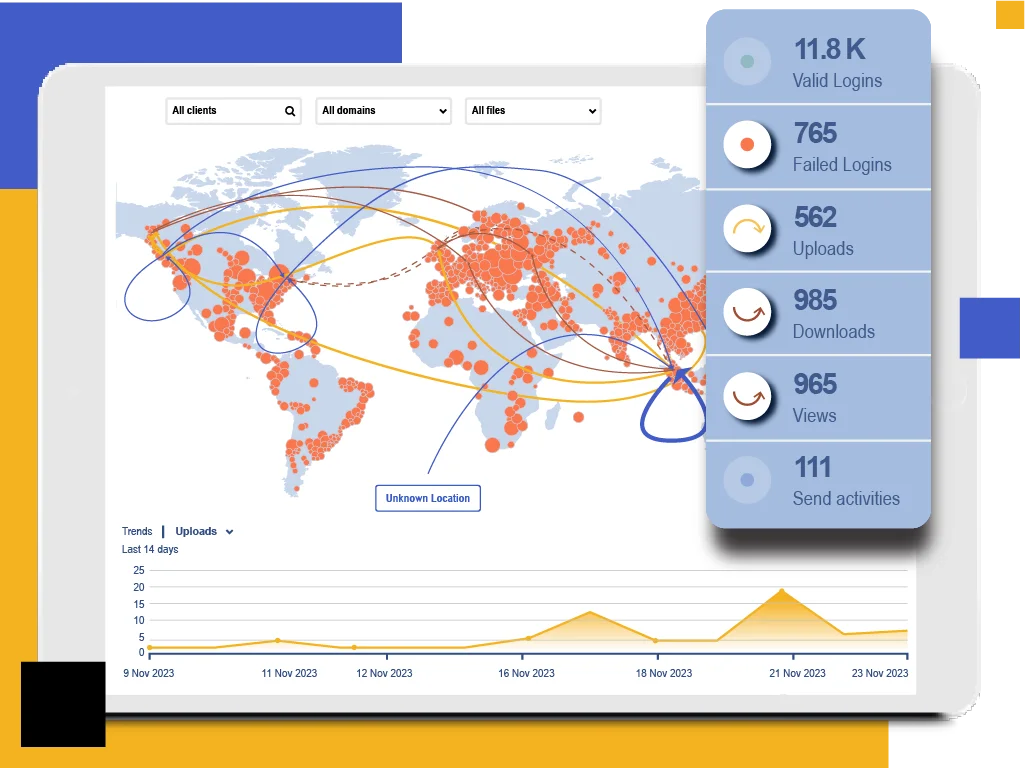
Rapid Incident Detection and Response
Enforce advanced security features and monitoring tools to help healthcare organizations detect and respond rapidly to potential security incidents. The platform offers real-time notifications and alerts and comprehensive auditing and reporting capabilities, enabling organizations to identify and investigate potential breaches promptly. It includes a secure mobile container that can be wiped remotely in the event of a lost or stolen device. This helps ensure compliance with the HIPAA Breach Notification Rule and minimize the impact of unauthorized access or disclosure of patient information (PII/PHI).
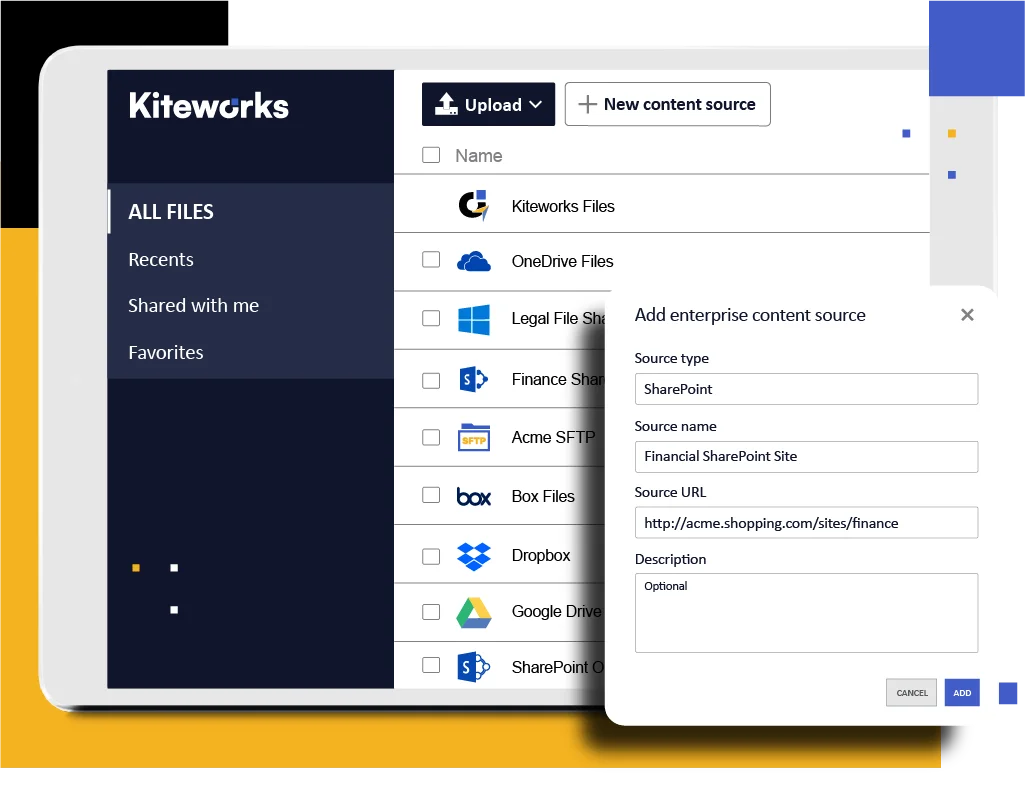
Streamlined Collaboration With Business Associates
Facilitate secure collaboration, control, and file sharing between healthcare organizations and their business associates. By providing a Private Data Network for exchanging sensitive information, Kiteworks supports compliance with the HIPAA Omnibus Rule. This ensures that patient information remains protected and that covered entities and business associates meet compliance obligations.
Enhanced Privacy Controls for Genetic Information
Implement zero-trust data exchange policies and enhanced privacy controls by the Final Rule for GINA to protect genetic information. The platform ensures limited access to sensitive genetic information, preventing unauthorized use or disclosure. Kiteworks enables healthcare organizations to securely manage file transfer and protect genetic information by offering granular access controls and secure communication channels while complying with GINA and the HIPAA Privacy Rule.
HIPAA Compliance FAQs
HIPAA requires end-to-end encryption, access controls, and audit trails when sharing personally identifiable and protected health information (PII/PHI) between healthcare providers. You must ensure only authorized personnel access patient data and maintain comprehensive audit logs of all sharing activities. Kiteworks provides automated end-to-end encryption, role-based permissions, and detailed audit logs that track all PHI exchanges. Kiteworks’ Private Data Network features Kiteworks secure collaboration, ensuring protected PHI exchange between covered entities while ensuring HIPAA compliance with both HIPAA Privacy and Security Rules for inter-provider patient data sharing.
Yes, with proper mobile device management solutions that include remote wipe capabilities and secure containers for patient data. HIPAA requires immediate action to prevent unauthorized personally identifiable and protected health information (PII/PHI) access when devices are lost or stolen. Kiteworks provides secure mobile containers with remote wipe capabilities in the event a device is compromised, completely removing patient data and preventing unauthorized access to PHI. This rapid response capability helps healthcare organizations demonstrate HIPAA compliance as well as adherence to HIPAA Breach Notification Rule requirements while protecting patient privacy.
The HIPAA Omnibus Rule requires covered entities to ensure their business associates implement appropriate safeguards for personally identifiable and protected health information (PII/PHI) through business associate agreements (BAAs) and secure data exchange platforms. You must monitor and audit business associate access to patient information. Kiteworks facilitates HIPAA compliance with Kiteworks secure collaboration, enabling healthcare organizations and their business associates to protects the PHI they exchange with granular access controls, comprehensive audit logs, and encrypted file sharing that supports HIPAA Omnibus Rule compliance and BAA requirements.
HIPAA requires comprehensive audit logs that track all personally identifiable and protected health information (PII/PHI) access, modifications, sharing activities, and user actions to demonstrate compliance and investigate potential breaches. These logs must include user identification, timestamps, and specific actions performed on patient data. Kiteworks provides detailed audit logs and reporting capabilities that track all user activities, including file access and data sharing events; namely who sent what to whom and when. These comprehensive logs help healthcare organizations meet HIPAA compliance requirements and quickly identify potential security incidents or unauthorized PHI access.
The GINA Final Rule and HIPAA Privacy Rule require enhanced privacy controls and zero trust security policies for genetic information with limited access and secure communication channels. Genetic data needs additional protections beyond standard personally identifiable and protected health information (PII/PHI) requirements. The Kiteworks Private Data Network provides granular access controls and secure file transfer capabilities specifically designed for sensitive genetic information. The platform ensures limited access to genetic data, prevents unauthorized disclosure, and provides secure communication channels while maintaining both GINA and HIPAA compliance
.
FEATURED RESOURCES

How To Protect PHI and Comply With HIPAA While Meeting Employee Vaccine Mandates
NYC Health + Hospitals: Protecting PHI While Improving Efficiency and Visibility

Navigating the American Data Privacy and Protection Act With Kiteworks’ Support

Sensitive Content Communications Privacy and Compliance in Healthcare

15 Use Cases for HIPAA Compliance and How Kiteworks Helps Satisfy Them
IT, SECURITY, PRIVACY, AND COMPLIANCE LEADERS AT THOUSANDS OF THE WORLD’S LEADING ENTERPRISES AND GOVERNMENT AGENCIES TRUST KITEWORKS















