
3 Cost Amplifiers and Data Breach Risk in IBM’s 2023 Cost of a Data Breach Report
IBM’s 2023 Cost of a Data Breach Report provides critical insights into the shifting landscape of cybersecurity threats and the associated costs for organizations globally. Just as cybersecurity and risk management professionals use the Verizon Data Breach Investigations Report to pinpoint threat trends, the report from IBM, conducted by Ponemon Institute, is a bellwether on the financial, brand, and compliance impact of the resulting data breaches. The two reports provide all of us with a one-two punch and reliable telemetry for measuring risk posture.
Cost of Data Breaches and Measuring Sensitive Content Communications Privacy and Compliance
This year’s report from IBM, published for 18 consecutive years, introduces some significant developments in terms of attack vectors and cost implications that necessitate an examination. This blog post aims to review and summarize key takeaways from the report, focusing on the average cost of data breaches, the effect of varying security practices on these costs, the different types of data cybercriminals and rogue nation-states are targeting, and the rise of software supply chain attacks. Some of the most notable overarching insights include:
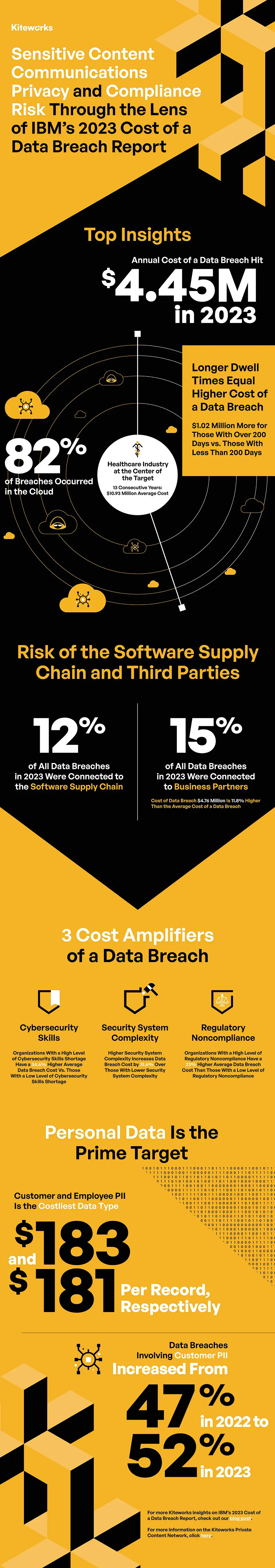
- The cost of data breaches hit an all-time high of US$4.45 million
- The healthcare industry led the pack again, 13th year in a row, suffering an average cost of US$10.93 million per data breach
- 82% of breaches involved data in cloud—public, private, or multiple environments
- The longer the dwell time, the higher the cost of a data breach: average cost difference between breaches that took over 200 days to find and resolve and those that took less than 200 days: US$1.02 million
- Only half of organizations are willing to spend more on security
At the same time, having just published our annual Sensitive Content Communications Privacy and Compliance Report, readers will likely find it interesting to evaluate some of our findings alongside those contained in the IBM report. The detailed analysis aims to delve into the key findings in the IBM report and to establish the parallels and divergences in their conclusions, thereby providing a comprehensive understanding of the current cybersecurity scenario.
Software Supply Chain Attacks
One of the most striking observations from IBM’s report was the incidence of software supply chain attacks as the source of data breaches. These attacks involve malicious actors infiltrating a software vendor’s network and manipulating the software to compromise its customers’ data or systems. While previously, threats were often thought of as external breaches directly targeting a company’s infrastructure, the new wave of attacks is more insidious.
The IBM report reveals the software supply chain was the source of 12% of data breaches this past year. This represents a marked shift in cyberattack methods and highlights the need for organizations to reassess their security measures across their software supply chains. Software supply chain attacks demonstrate how vulnerabilities in the digital ecosystem can cause widespread harm.
Notably, managed file transfer attacks, such as the ones on GoAnywhere and MOVEit, exemplify this new type of threat. These attacks can expose sensitive data across a multitude of industries, affecting hundreds or even thousands of companies simultaneously. It is essential that organizations review their software vendors’ security practices and consider implementing enhanced cybersecurity measures to protect against these emerging threats.
Business Partner/Third-party Attacks
Building on the findings around the software supply chain, the IBM report found that third-party business partners are also a significant data breach risk: 15% of organizations identified them as the source of a data breach. Business partner supply chain compromises had an average cost of US$4.76 million per data breach, 11.8% higher than the average cost of a data breach. One of the reasons, according to IBM, is the lengthy dwell time: It took an average of 233 days to identify and 74 days to contain business partner supply chain compromises. This is 37 days, or 12.8%, longer than the average data breach.
This certainly aligns with what we reported in the Kiteworks study. An astounding 84% said that at least some improvement is needed in their organization’s risk management of third-party communications. More than 4 in 10 said that significant improvement is needed, with some even saying they need an entire “do-over.”
Three Cost Amplifiers and Data Breach Risk
The IBM report shows that the global average cost of a data breach reached $4.45 million, marking a 15% increase over the past three years. The impact of various cost amplifiers on this average cost was also examined by Ponemon Institute. Comparisons were made between organizations with the highest and lowest levels of top-ranking cost amplifiers, offering insights into the financial repercussions of different levels of preparedness and responsiveness. The biggest cost amplifiers, according to the IBM report, were security system complexity, security skills shortage, and noncompliance with regulations. This finding resonates with the conclusion drawn by Kiteworks’ report, which revealed that cyber exploits have resulted in financial damage for 62% of organizations.
1. Security System Complexity and Data Breach Risk
Organizations with higher levels of security system complexity have higher risk, according to the IBM report. Organizations with low or no security system complexity experienced an average data breach cost of US$3.84 million. In contrast, those admitting to high levels of security system complexity saw an average cost of US$5.28 million—a 31.6% difference.
Findings in Kiteworks’ report uncovered similar findings when it comes to communication tools used to send and share sensitive content. Half of respondents in the survey said they share content with six or more channels. Managing these different communication tools is highly complex, which is exacerbated due to the large number of third parties with which sensitive content is changed; 90% share sensitive content with over 1,000 third parties, while 44% do so with over 2,500 third parties. Further, 85% of organizations use four or more systems to track, control, and secure sensitive content communications. The takeaway here: Just as the IBM report finds, complexity in sensitive content communications ratchets up risk.
2. Cybersecurity Skills and Data Breach Risk
The IBM report identifies a difference of US$1.58 million (34.6%) between high levels and low levels of security skills shortage. A high level of security skills shortage led to an average cost of US$5.36 million, US$910,000 higher than the average data breach cost. The report suggests that investing in skills development and ensuring a well-staffed security team can significantly reduce the cost of data breaches.
These findings suggest a clear need for investing in skills development and ensuring a well-staffed security team, a perspective that is further supported by the Kiteworks report. The Kiteworks report elaborates on how organizations struggle to measure and manage security and compliance risks, mainly due to inadequate governance and security, which can likely be linked to a lack of skilled personnel.
3. Regulatory Compliance and Data Breach Risk
The digital world is firmly planted in an era of compliance. This demands a rethink of cybersecurity, digital rights management, and regulatory compliance. According to the IBM report, organizations with a high level of noncompliance with regulations exhibit US$5.05 million in the average cost of a data breach, compared to US$4.01 million for those with low levels of compliance with regulations—a 23% difference of US$1.04 million.
Transitioning to the Kiteworks report, it’s important to consider that risk around sensitive content communications isn’t only confined to data breaches, but also revolves heavily around compliance. Many associate compliance with government regulation, and indeed, global companies operating in multiple jurisdictions are subjected to a wide array of such regulations. But it’s not only laws and regulations that define compliance requirements. Industry-specific mandates, such as PCI DSS for entities processing payment card transactions, also come into play.
With all these compliance requirements in place, preparations for audits become a routine part of the risk management or IT security teams’ calendar. These audits can also follow a cyber incident, reinforcing the potential business risks that a failed audit can present. Survey data offers a glimpse into the state of compliance risk management for sensitive content communications, with approximately a quarter of the respondents acknowledging that no improvement is needed in either measuring or managing compliance risk.
Breach Identification
In terms of breach identification, 40% of breaches were identified by a benign third party or outsider, while 33% were detected by internal teams and tools. Interestingly, 27% of breaches were disclosed by the attacker, often as part of a ransomware attack.
Breaches disclosed by attackers had an average cost of US$5.23 million, which was a 19.5% or US$930,000 difference over the average cost of breaches identified through internal security teams or tools of US$4.30 million. Breaches identified by an organization’s own security teams and tools were significantly less expensive, costing nearly US$1 million less than incidents disclosed by the attacker. This information emphasizes the importance of robust internal security measures for early detection and mitigation of breaches.
Data Type and Breach Cost
When it came to the type of data compromised, customer and employee personally identifiable information (PII) were the costliest, with an average cost of US$183 and US$181 per record, respectively. In contrast, the least expensive record type to have compromised was anonymized customer data, costing organizations US$138 per record.
An increase was noted in the percentage of breaches involving customer PII, from 47% in 2022 to 52% in 2023, while the compromised employee PII also rose from 26% in 2021 to 40% in 2023. This suggests a targeting of more valuable data types, further emphasizing the need for businesses to strengthen their cybersecurity measures.
The risk pinpointed by the IBM report is confirmed by findings in the Kiteworks report. Over half of the participants placed PII, PHI, and legal documents in the top three. Regional variations reflected different regulatory concerns. For instance, in Europe and Asia Pacific, where GDPR and similar laws prevail, PII is prioritized. North Americans, where HIPAA is a significant compliance requirement, showed more concern about PHI. Interestingly, in the Middle East, intellectual property (IP) was perceived as a much bigger risk, with 60% ranking it among the top three.
Industry-specific variations were also noted, although most were expected or understandable. There was greater concern about legal documents in financial services, higher education, and healthcare sectors. Mergers and acquisitions (M&A) took precedence in law firms, professional services, and pharmaceutical/life sciences companies. Financial documents were a more significant point of emphasis in local government, while PHI was more critical in energy and utilities companies and federal government agencies. In contrast, healthcare sectors showed less concern for PHI, presumably due to already having robust protection measures in place.
Aligning Key Takeaways From the Two Reports
Findings of IBM’s 2023 Cost of a Data Breach Report highlight the ongoing challenges businesses face in securing their data and networks. Software supply chain attacks, security skills shortages, and system complexities, among other factors, significantly affect the cost of a data breach. As cyber threats continue to evolve, it’s vital for businesses to stay ahead by investing in their cybersecurity infrastructure and practices, ensuring they can respond effectively to any breach scenario.
When findings from the IBM report are read alongside those from Kiteworks’ 2023 Sensitive Content Communications Privacy and Compliance Report, some interesting insights and takeaways emerge. Personal PII and PHI data is a target, and as the complexity of communication systems used to send and share that data increases, so does the risk. Adherence to regulatory compliance is having a positive risk impact according to the IBM report. As the number of data privacy and cybersecurity regulations increase and their complexity grows, organizations need to ensure they have the right technology tools in place to manage their risk.
Organizations seeking assistance in managing their sensitive content communication security and compliance risk can schedule a custom-tailored demo of the Kiteworks Private Content Network.
Additional Resources
- Brief How Kiteworks Hardened Virtual Appliance Adds Multiple Security Layers
- Brief How to Achieve Zero Trust Security With Kiteworks
- Brief Why You Absolutely, Positively Need the Most Modern and Secure MFT Solution
- Blog Post 4 File and Email Communication Takeaways From the Verizon 2023 DBIR
- Blog Post Why It Is Time for a Digital Rights Management “Do-over”
- Brief Top 6 Reasons to Add Email Protection Gateway to Your Kiteworks Deployment