
DFARS 252.204-7012 Compliance: Everything Defense Contractors Need to Know
As the defense industry faces an ever-growing number of cyber threats, compliance with Defense Federal Acquisition Regulation Supplement, or DFARS 252.204-7012 is crucial to ensure the protection of sensitive data, maintain national security, and safeguard the interests of the Department of Defense.
In this post, we will explore the basics of DFARS 252.204-7012, its implications for defense contractors, and the essential steps required for compliance. Let’s delve into the world of cybersecurity in defense contracting and learn more about this vital regulation.
What Is DFARS 252.204-7012?
DFARS 252.204-7012 is a regulation that mandates defense contractors to implement adequate cybersecurity measures to protect controlled unclassified information (CUI). CUI refers to sensitive information that requires safeguarding but is not classified. The regulation applies to all defense contractors, subcontractors, and suppliers that handle, store, or transmit CUI on behalf of the DoD.
The impact of DFARS 252.204-7012 on defense contracts is significant, as failure to comply with the regulation can lead to the loss of existing contracts, disqualification from future contracts, and other financial and legal repercussions. Therefore, defense contractors must take this requirement seriously and strive for compliance to maintain their business relationships with the DoD.
DFARS 252.204-7012 Compliance Requirements
The following are the key DFARS 252.204-7012 requirements that defense contractors must meet for compliance:
| 1. | Safeguarding of Controlled Unclassified Information | Contractors must implement adequate security measures to protect CUI, which includes confidentiality, integrity, and availability of information. |
| 2. | Cyber Incident Reporting | Contractors must report any cyber incident to the DoD within 72 hours of discovery. |
| 3. | Security Assessment | Contractors must conduct a thorough security assessment of their information systems and submit a summary of the assessment to the DoD. |
| 4. | Compliance With NIST SP 800-171 | Contractors must comply with the National Institute of Standards and Technology (NIST) Special Publication (SP) 800-171, which outlines the security requirements for protecting CUI in non-federal information systems and organizations. |
| 5. | Flow Down Requirements | Contractors must ensure that their subcontractors also comply with the DFARS 252.204-7012 regulation. |
Table 1.1: DFARS 252.204-7012 Compliance Requirements
Failure to comply with DFARS 252.204-7012 can result in severe consequences. First, noncompliance suggests a contractor’s or subcontractor’s systems, applications, or procedures are unsecure, which exposes CUI to unauthorized access. Second, noncompliance can lead to a contractor or subcontractor losing access to government contracts and other penalties. To mitigate these risks, defense contractors must prioritize compliance by investing in necessary resources and establishing robust cybersecurity measures that adhere to the regulation’s guidelines.
What’s the Difference Between NIST SP 800-171 and DFARS 252.204-7012?
The National Institute of Standards and Technology Special Publication 800-171, or NIST SP 800-171, is a set of guidelines that provide the framework for implementing the cybersecurity requirements outlined in DFARS 252.204-7012. The guidelines contain 110 security controls, divided into 14 families, and are designed to enhance the protection of CUI.
Compliance with NIST SP 800-171 is critical for defense contractors subject to DFARS 252.204-7012, as adherence to these guidelines demonstrates a contractor’s commitment to protecting sensitive information and their ability to meet the DoD’s cybersecurity requirements.
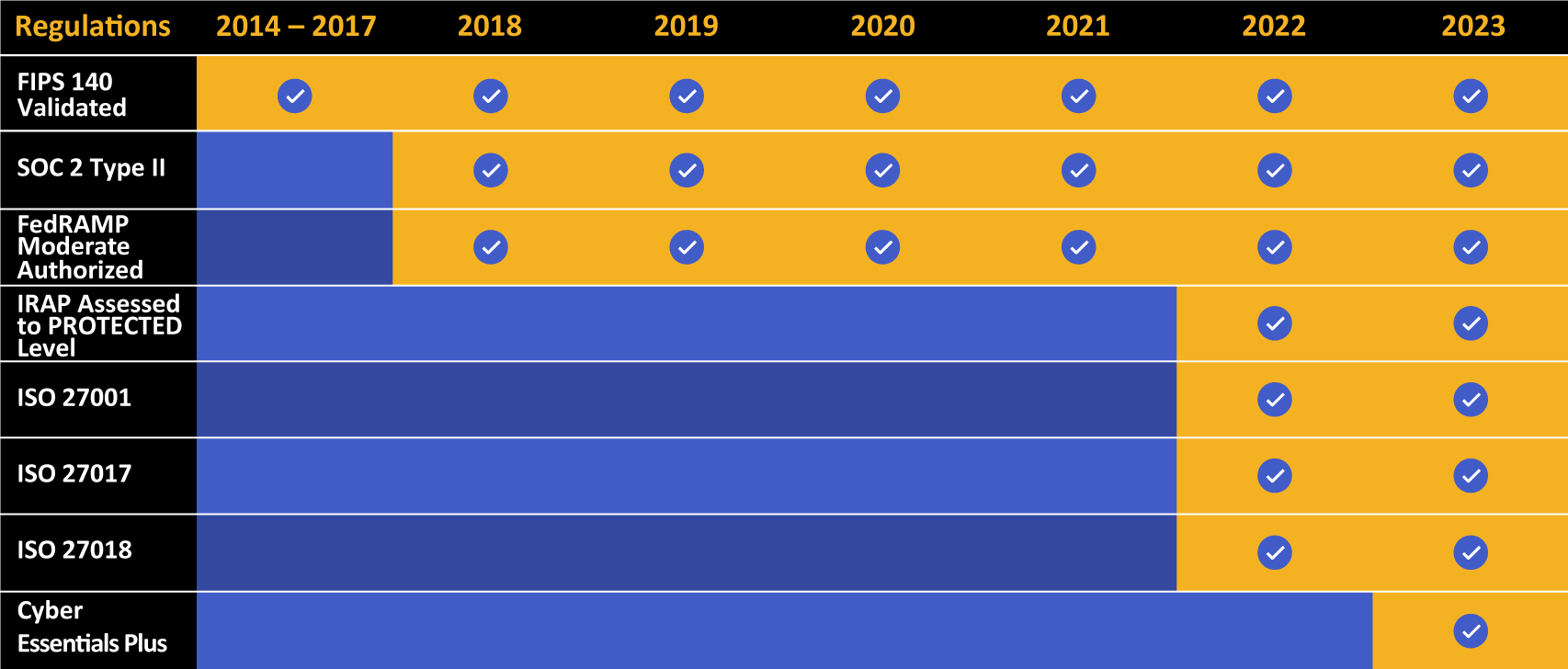
Kiteworks touts a long list of compliance and certification achievements.
What’s the Difference Between CMMC and DFARS 252.204-7012?
Cybersecurity Maturity Model Certification (CMMC) is a forthcoming cybersecurity certification that will further bolster the DoD’s efforts to protect its sensitive information. Once implemented, CMMC 2.0 will require defense contractors to obtain a specific level of certification (CMMC Level 1, CMMC Level 2, or CMMC Level 3), depending on the sensitivity of the information they handle and the complexity of their contracts with the DoD.
CMMC is designed to strengthen the cybersecurity posture of the Defense Industrial Base (DIB) by establishing a unified standard for mitigating cyber risks. It complements and builds upon the requirements of DFARS 252.204-7012, making it essential for defense contractors to stay informed about the developments in this area.
Preparing for DFARS 252.204-7012 Compliance
Defense contractors must be fully compliant with DFARS 252.204-7012 to protect sensitive government information, which is critical to national security. The process of achieving compliance may vary depending on the size and complexity of the contractor’s organization. Generally, the process can take several months and can be complicated, requiring the implementation of new policies, procedures, and controls. It may also involve significant costs, such as the acquisition of new hardware and software or the hiring of external consultants. Fulfilling each of the five core requirements—identifying covered defense information, implementing security requirements, assessing and documenting compliance, reporting cyber incidents, and flowing down requirements—may also have different timelines and challenges. Regardless, contractors must take the necessary steps to ensure DFARS 252.204-7012 compliance to avoid severe penalties such as the loss of government contracts or legal liability.
| Step 1 | Develop a Plan of Action and Milestones (POA&M) | The first step toward compliance is developing a robust plan of action and milestones (POA&M). The POA&M is a structured document that outlines the security measures that contractors will take to meet the requirements of DFARS 252.204-7012. The POA&M should include the timelines for implementing security controls and mitigating vulnerabilities, the responsible personnel, and the resources required for each action item. It should also include a follow-up plan for monitoring and updating the security measures. |
| Step 2 | Generate a System Security Plan (SSP) | To comply with DFARS 252.204-7012, defense contractors must have a system security plan (SSP) in place. The SSP is a comprehensive document that outlines the security controls that contractors have implemented to protect sensitive government information. The SSP should detail the security measures for both the contractor’s network and the network of any subcontractors who handle government information. The SSP should describe the procedures for identifying and mitigating vulnerabilities, the personnel responsible for implementing the security controls, and the processes for testing and evaluating the effectiveness of the security measures. Additionally, the SSP should include an incident response plan that outlines the procedures for responding to security breaches, including reporting incidents to the government. |
| Step 3 | Conduct Self-assessments and Third-party Assessments | DFARS 252.204-7012 requires defense contractors to conduct self-assessments and receive a third-party assessment to verify the effectiveness of their security controls. Self-assessments involve reviewing the security measures outlined in the SSP and identifying any deficiencies or vulnerabilities. If any deficiencies or vulnerabilities are identified, contractors must develop and implement a plan to remediate them. The results of self-assessments and third-party assessments should be included in the POA&M and used to guide the contractor’s ongoing security efforts. |
Table 1.2: DFARS 252.204-7012 Compliance Requirements
DFARS 252.204-7012 Compliance Challenges for Defense Contractors
Complying with DFARS 252.204-7012 can be challenging for defense contractors, as it often requires significant investments in cybersecurity infrastructure, employee training, and compliance management. Some common challenges include budget constraints, lack of cybersecurity expertise, and difficulties aligning internal processes with the regulation’s requirements.
To overcome these challenges, defense contractors should adopt best practices such as conducting a thorough assessment of their current cybersecurity measures, creating a comprehensive implementation plan, and seeking external support from experts in the field. Success in this area can lead to improved cybersecurity, a stronger reputation within the defense industry, and increased opportunities for business growth.
The Role of Third Party Assessor Organizations in DFARS 252.204-7012 Compliance
Third Party Assessor Organizations (C3PAOs) are independent organizations that evaluate defense contractors’ compliance with DFARS 252.204-7012 and NIST SP 800-171. They play a crucial role in ensuring that contractors adhere to the regulations and maintain the necessary level of cybersecurity.
The assessment process typically involves a review of a contractor’s cybersecurity measures, an evaluation of their compliance with NIST SP 800-171, and the provision of recommendations for improvement. The timeline for assessments can vary but generally takes several months to complete.
C3PAOs evaluate the effectiveness of the contractor’s security controls and provide a report outlining any deficiencies or vulnerabilities. Contractors must remediate any deficiencies or vulnerabilities identified during the audit and provide evidence of compliance to the government.
How Much Does DFARS 252.204-7012 Compliance Cost?
DFARS 252.204-7012 compliance can be costly, as it often requires significant investments in cybersecurity infrastructure, personnel training, and ongoing maintenance. However, the financial and operational impact of noncompliance can be much more severe, making it crucial for defense contractors to prioritize this area.
Strategies for minimizing the cost of compliance include conducting a thorough assessment of current cybersecurity measures, implementing cost-effective improvements, and seeking external support. Investing in compliance is a wise decision for defense contractors, as the long-term benefits of protecting sensitive information and maintaining a strong relationship with the DoD far outweigh the costs.
Kiteworks Helps Contractors Achieve DFARS 252.204-7012 Compliance
DFARS 252.204-7012 compliance is a critical requirement for defense contractors that handle and share CUI sensitive information with the U.S. government. This regulation mandates compliance with NIST SP 800-171, which outlines specific cybersecurity controls that contractors and subcontractors must implement to protect CUI.
The Kiteworks Private Content Network helps defense contractors meet their DFARS 252.204-7012 compliance requirements. Kiteworks is FedRAMP Authorized to Moderate Level Impact, and meets all the security requirements listed in NIST 800-171. This allows government contractors to share and transfer CUI with government agencies with the highest levels of security and compliance. Additionally, Kiteworks supports nearly 90% of CMMC 2.0 Level 2 requirements out of the box, the highest level for sensitive content communications platforms in the industry.
The Kiteworks Private Content Network is a unified, secure, and easy-to-use communications platform that provides end-to-end encryption, access controls, encryption key ownership, and visibility into all file activity, namely who sent what to whom, when, and how. Kiteworks consolidates all third-party communication channels, including secure email, file sharing, managed file transfer (MFT), secure file transfer protocol (SFTP), web forms, and more so that every sensitive file sent, received, or shared is centrally controlled, protected, monitored, and tracked.
Integrations with enterprise applications, enterprise content management (ECM) systems, and security tools ensure personally identifiable information and protected health information (PII/PHI), financial statements, contracts, intellectual property, and other sensitive information is accessed and shared securely.
Every file upload, download, and share is logged for eDiscovery and regulatory compliance. In fact, Kiteworks supports a range of other regulations and standards, including International Traffic in Arms Regulations (ITAR), the General Data Protection Regulation (GDPR), SOC 2, the Federal Information Security Management Act (FISMA), FIPS 140-2, and Export Administration Regulations (EAR).
For more information on the Kiteworks platform, schedule a custom demo today.
Additional Resources
- Blog Post What Are Data Compliance Standards?
- Blog Post Secure File Transfer for Defense Contractors: Ensuring Confidentiality and Integrity
- Blog Post NIST 800-171 Compliant File Sharing—What You Need to Know
- Blog Post A Roadmap for CMMC 2.0 Compliance for DoD Contractors
- Webinar Making the Journey to CMMC 2.0 by Protecting FCI and CUI