
End of Life Software: Risks, Dangers & What to Do Next
Understanding what to do when you have EOL software becomes crucial to the security of your organization. So, what happens when your system reaches EOL?
When software reaches EOL, it means that program will no longer be supported by the developer and there will be no more updates. Without updates and bug fixes, this software becomes vulnerable to hackers and cybercriminals.
Nothing lasts forever. This applies to software and infrastructure. Legacy solutions and applications are a reality for most organizations from small to medium size businesses and definitely for the enterprise world. For any company investing in cloud initiatives, end of life (EOL) becomes even more complex.
What Is End of Life (EOL)?
Sooner or later everything we use reaches its tipping point and a technological expiry date. End of life (EOL) is when the manufacturer stops developing and servicing the product. This can include discontinuing technical support, upgrades, bug fixes, and most importantly, security fixes.
A few risks you want to look out for if your business is running EOL software are:

How Do I Know if My Software Is Reaching End of Life?
The best way to determine if your software is reaching end of life is to consult the software vendor or developer directly. They can provide you with precise information about the end of life date for the version of the software you are using, and any available options for transitioning to another version or product. Additionally, you can typically find this information online through the vendor’s website.
Examples of EOL Software Still in Popular Use
While EOL software is no longer maintained or supported by its original developers, it is used by organizations all over the world. Here is a snapshot of some of the more popular software solutions that are still in use today:
- Microsoft Windows XP: Despite being released more than 15 years ago, Windows XP is still widely used due to its simplicity and low hardware requirements. It is considered by many to be one of the most reliable and stable operating systems ever released.
- Mozilla Firefox: Mozilla Firefox is a cross-platform web browser released back in 2004. Although it was officially discontinued in 2017, it remains popular among web users due to its customizability and features.
- Adobe Flash: Adobe Flash was a multimedia platform used to create interactive web content. It was discontinued in 2020 but is still widely used to play older Flash-based games and videos.
- Java 6: Java 6 was released in 2006 and was widely used in business applications. Although it was officially discontinued in 2018, it is still widely used in many corporate environments.
- Microsoft Office 2003: Microsoft Office 2003 was the last version of the popular productivity suite before the introduction of the ribbon interface. Although it was officially discontinued in 2013, it is still widely used due to its familiar interface.
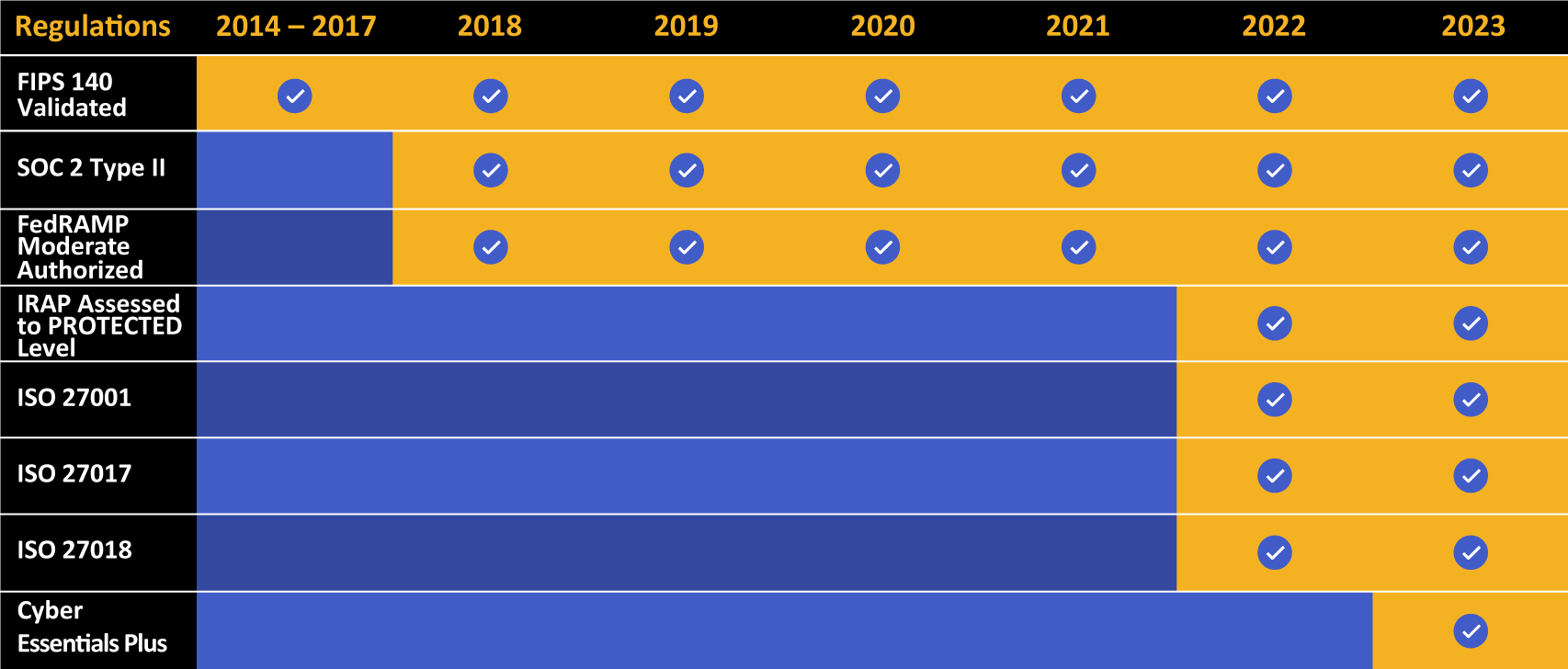
Kiteworks touts a long list of compliance and certification achievements.
Operational Risks Can Cause Business Interruption
While discussing EOL with business stakeholders you often hear the argument that the legacy system or application is super critical for the business and it has operated without any problems for many years. Why change a system that is reliable and currently operating?
These stakeholders eventually see that EOL components become less and less reliable over time and more prone to failures. They tolerate these conditions until something goes really wrong.
Software nearing EOL also impacts usability. We live in a fast-developing world where new standards emerge and make old ones obsolete. People suddenly find themselves in a situation where the critical web application still works but web browsers no longer support the old encryption in transit methods used by the web application. If these risks materialize, they can cause business interruption, driving up costs and creating client unhappiness.
Security Risks Can Damage Your Reputation
Cybersecurity risk is widely understood given cyberattacks and data breaches are reported in the press every day. This does not mean that everyone takes the appropriate remediation efforts to address them.
As mentioned, end of life technology receives no security updates, bug fixes, or patches; it is dead in the eyes of the manufacturer. That means your security is completely compromised, not only for the system or software that is EOL, but also potentially for any others that connect to it.
In the worst-case scenario, your EOL system or software can be hacked and data stolen. Such cybersecurity incidents are embarrassing, putting your reputation and customer trust on the line.
How WannaCry Exploited End of Life Vulnerabilities in Windows
To put all this into perspective, consider a real-life example. WannaCry exploited Windows XP’s End of Life by using a vulnerability in the XP operating system. The attackers used a file called EternalBlue, which allowed the malware to spread from system to system without user interaction. The malware then encrypted the user’s data and demanded a ransom, payable in bitcoin, to unlock it. The vulnerability was patched for more recent Windows operating systems, but since support for Windows XP ended in 2014, it remained open to exploitation.
Compliance Risks Can Result in Hefty Fines
Regulatory scrutiny is on the rise, therefore compliance with regulatory requirements is no longer an option. GDPR, PCI, SOX or HIPAA are prominent examples, and they require that all technologies used must be supported.
Compliance risks on EOL systems are similar to cybersecurity risks. By failing compliance requirements with legacy systems or software, a business can face hefty fines, particularly in the event of a data breach.
Support Risks Can Increase Maintenance Costs
The longer EOL technologies are kept past their supported life cycle, the higher the costs increase for keeping them running. Over time, businesses have fewer people who are familiar with the legacy technology and are incapable of supporting it. When support demand exceeds supply, maintenance costs increase in parallel with the risks of a security or compliance event.
Mitigating Risk for End of Life Technologies
Organizations can mitigate the risk associated with end of life technologies by taking a proactive approach with their vendor vendor risk management program. It is important for example to stay aware of technology changes and plan for them before the technology becomes outdated. This can include researching new technologies or new versions of existing technology, developing a timeline for the transitioning to a new technology or version, training staff on new features and capabilities, and creating budget plans for the transition. Additionally, organizations should consider buying technology with longer life cycles and that can support upgrades, as this will help to extend the life of the technology. Finally, organizations should consider investing in backup systems or redundant systems in case of any problems or delays in the transition to the new technology.
Operating end of life systems and software may be tempting but the financial, security, and compliance risks far exceed the benefits. All serious technology providers provide plenty of advanced notice prior to sunsetting an obsolete technology. Businesses that adhere to these announcements and move off of legacy technologies save more than investment dollars. They may also save their reputations and customer loyalty. Remaining or relying on EOL technology is just not worth the risk.
Additional Resources
- Report Benchmark Your Sensitive Content Communications Privacy and Compliance
- Blog Post What Is a Private Content Network?
- Blog Post Kiteworks Utilizes Its Own Private Content Network