
Protect Sensitive Content With Maximum Security
Kiteworks offers single-tenant hosting and data sovereignty so Australian government agencies and private sector companies have a true private content network for sharing and storing sensitive content. The Kiteworks platform, including the content you store and share, is entirely hosted within Australia while a separate AWS virtual private cloud (VPC) is utilized for all processing. Because Kiteworks is FedRAMP compliant, we can provide a dedicated server that ensures your sensitive content is isolated from all other customers on Amazon Cloud. You control the encryption keys, so only you can access the files (Kiteworks does not have access to your content). Lastly, comprehensive reporting and audit logs provide a comprehensive, detailed look at who is accessing your content and with whom they’re sharing it.
Protect Information Integrity With a Proven Defense-in-Depth Approach
Kiteworks’ layered defense strategy uses multiple security measures to protect the integrity of the information you store and share. This includes: least-privilege defaults and role-based access controls, secure data storage and transmission, user activity monitoring, and multi-factor authentication. You configure your own policy and security controls so Kiteworks meets your unique security requirements. Your content is protected by a hardened virtual appliance with WAF and network firewalls, automated alerting and intrusion detection, unified logging for rapid event response, and security integrations like ATP, DLP, SSO, LDAP, HSM, and others.


Maximize Uptime and Protection With Premium Support
Powering the PCN is Kiteworks’ secure cloud hosting with premium support that includes patching and update services, named service representatives, enhanced service-level agreements (SLAs), and other high-touch services. Highly qualified Kiteworks support engineers address system errors, loss of functionality, configuration issues, feature requests, and more, available via telephone or remote system access 24 hours a day, seven days a week. Tightened SLA and priority case handling, with one-hour turnaround time for Level 1 or Critical Priority issues. Annual health check and deployment review, including storage capacity, file consistency, contention, deadlocks, database consistency, memory utilization, and CPU utilization, help you maximize the value of your Kiteworks deployment. Lastly, Kiteworks support engineers apply all software updates and security patches per an agreed-to schedule.
Reap Additional Rewards Beyond IRAP With Kiteworks
Kiteworks’ IRAP assessment does much more than enhance your security posture and build trust with your customers. Using Kiteworks can be considered a best practice for sharing sensitive content securely and in compliance. Kiteworks, in fact, complies with GDPR, SOC 2, ISO 27000 standards, FIPS 140-2, NIST 800-171, Cyber Essentials Plus, and SSAE-16 and supports many other data privacy regulations and standards, including HIPAA, CMMC, ITAR, GxP, NIS 2, NIST CSF, and others. Because Kiteworks is engineered from the ground up with an emphasis on security, your organization can demonstrate to your own customers that security is a top priority. In this current threat landscape, marked by an ever-increasing number of risks and attacks, organizations that prioritize security and data privacy often enjoy a distinct competitive advantage.

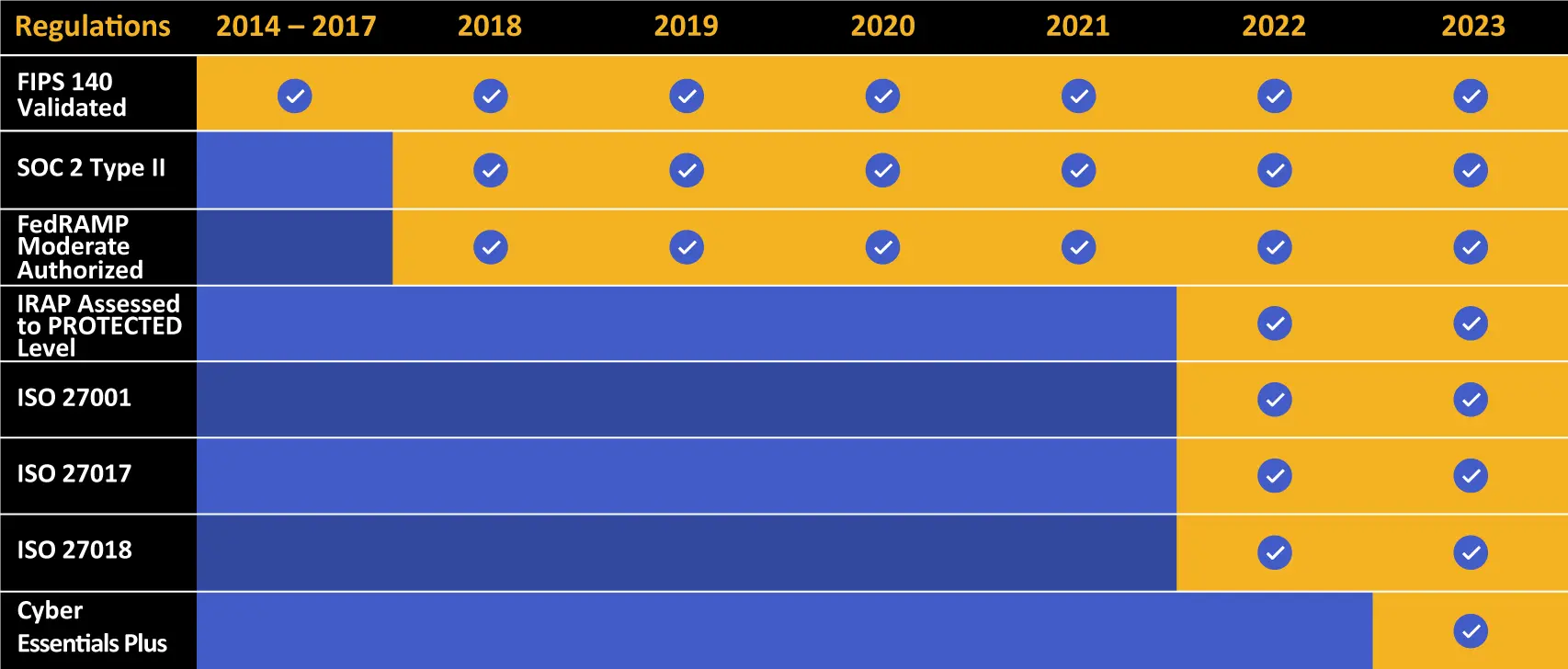
Kiteworks touts a long list of compliance and certification achievements.
Frequently Asked Questions
The Information Security Registered Assessors Program (IRAP) attests to the ability of private and public organizations to meet cybersecurity requirements in Australia. IRAP assessors help businesses doing work for the Australian government by independently assessing their cybersecurity posture. They identify risks and suggest mitigation measures. This helps ensure that those businesses have the right security policies and controls in place to meet Australian Government Information Security Manual (ISM) requirements.
IRAP compliance is important because it ensures that organizations doing business in Australia are taking the necessary steps to protect sensitive data and prevent cyberattacks. IRAP compliance helps organizations demonstrate their commitment to information security, which is critical for protecting sensitive content like customer data as well as building trust with customers and partners.
Organizations that provide services to the Australian government or store sensitive data belonging to Australian citizens need to comply with the Information Security Registered Assessors Program (IRAP). This includes businesses that handle credit card information, private patient information, financial or tax records, or intellectual property. Government agencies, critical infrastructure providers, and high-risk professions such as legal and accounting firms are among those that must comply with IRAP.
Organizations can achieve IRAP compliance by working with a registered assessor to undergo an assessment of their information security posture. The assessment will evaluate an organization’s compliance with the Australian Government Information Security Manual (ISM), as well as other relevant security standards and regulations. If the assessor deems the organization compliant with the ISM, the organization is recognized for achieving a specific level of assessment, e.g., “assessed to PROTECTED level.”
Yes. IRAP in fact is often considered to be a more rigorous and comprehensive standard than other information security regulations, such as the Australian Privacy Principles or the Payment Card Industry Data Security Standard (PCI DSS). As a result, compliance with IRAP can be used to demonstrate compliance with other regulations that may be less comprehensive or stringent. However, it is important to note that each regulatory body may have its own specific requirements and standards for compliance, so organizations should consult with their legal and compliance teams to ensure that they are meeting all necessary requirements.
FEATURED RESOURCES

Kiteworks’ IRAP-assessed Private Content Network Gives MinterEllison an Advantage

Kiteworks Supports Essential Eight Implementation for Australian Organizations
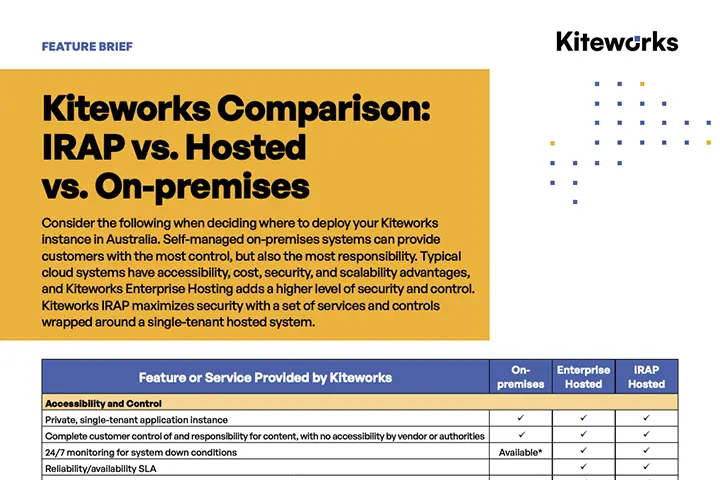
IRAP vs. Kiteworks Hosted vs. On Premises Deployment Comparison

MinterEllison: Protecting Sensitive Data in Compliance With IRAP

