Balancing Stringent Data Protection Requirements With Operational Efficiency
Meeting BDSG requirements presents significant challenges for organizations due to strict controls on special categories of data, extensive documentation demands, and comprehensive technical safeguards. Companies struggle to implement appropriate security measures while maintaining operational efficiency and demonstrating accountability through thorough record-keeping and audit logs.
The Compliance Balancing Act of Meeting Technical Requirements
Organizations face significant challenges when implementing BDSG compliance measures for special categories of personal data. The law demands precise technical controls that restrict processing to only legally permitted purposes while requiring comprehensive safeguards for data subjects’ rights. Companies must establish complex authorization frameworks, implement robust encryption systems, maintain detailed audit logs, and configure contextual access controls—all while ensuring operational efficiency isn’t compromised. The required risk assessments and impact evaluations add another layer of complexity, requiring specialized expertise and continuous monitoring.


Security-Privacy Balancing Act
Implementing appropriate technical and organizational safeguards under Section 22(2) requires organizations to make difficult trade-offs. Companies must evaluate the state of the art, implementation costs, and processing risks while ensuring robust protection for special categories of personal data. Organizations struggle to determine which specific measures—from pseudonymization and encryption to access restrictions and staff training—provide adequate protection without imposing excessive operational burdens.
Trapped in Documentation Overload
Meeting the BDSG’s tracking requirements creates significant operational strain for organizations. Companies must establish comprehensive systems that record who accessed, modified, or removed personal data while maintaining detailed processing logs and data transfer records. Teams must implement technical measures that capture all interactions with data, store these records securely, and make them readily available to authorities. This documentation burden diverts resources from core business functions while creating complex compliance challenges that demand constant attention and expertise.
Comprehensive Protection for Your Private Data Exchanges
Precision Protection Without Paralysis
Kiteworks tackles BDSG special data compliance through multi-layered defenses that balance security with usability. Zero-trust data exchanges control processing based on asset attributes, user profiles, and action types, preventing unauthorized handling of sensitive information. The platform’s robust authorization controls—including role-based and attribute-based access, least-privilege defaults, and administrative separation of duties—restrict special category data to appropriate personnel. Double encryption protects data at rest while comprehensive audit logs document all interactions. These integrated safeguards maintain compliant operations without sacrificing efficiency.
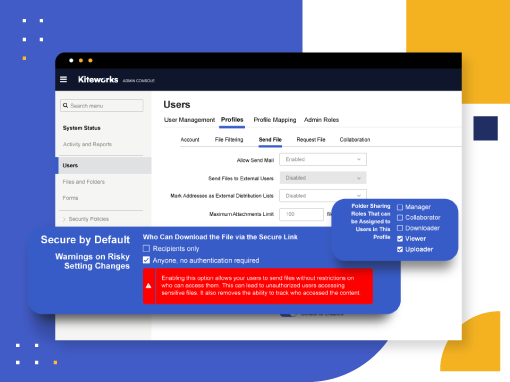
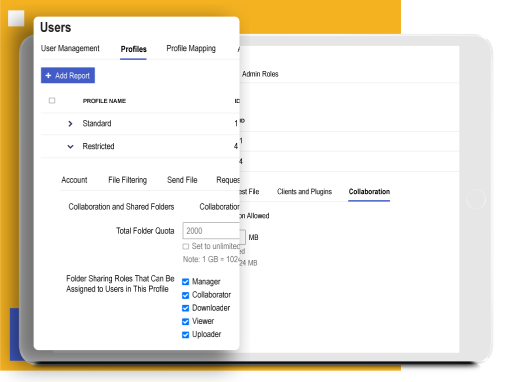
Layered Safeguards Without Complexity Overload
Kiteworks resolves Section 22(2) compliance challenges through integrated technical safeguards tailored to special category data protection. The platform combines robust authorization frameworks—including role-based and attribute-based access controls with least-privilege defaults—with precise collaboration permissions that limit data interactions based on user roles. This granular control extends across all data with customizable folder roles (Owner, Manager, Collaborator, Downloader, Viewer, Uploader), allowing organizations to implement appropriate safeguards without creating operational bottlenecks or excessive administrative overhead.
Complete Tracking, Simplified Auditing
Kiteworks addresses tracking mandates through its comprehensive audit logs with SIEM feeds, which create detailed records of every data interaction. The system logs all data actions—file uploads, edits, deletions, and sharing events—with specific user IDs, time stamps, and locations. These consolidated logs can be searched, filtered, sorted, and exported via syslog or Splunk Universal Forwarder for regulatory review. The dedicated auditor role provides access exclusively to the reports portal in the compliance console, enabling clean separation of duties while maintaining complete visibility for authorities.
Frequently Asked Questions
Kiteworks protects special categories of personal data through multi-layered security measures including zero-trust data exchanges, role-based access controls, and double encryption. These features restrict data access to authorized personnel only, prevent unauthorized processing, and maintain comprehensive audit logs—all essential for compliance with BDSG Section 22(2) requirements while still enabling necessary business operations.
Kiteworks provides comprehensive audit logs that capture every interaction with personal data, including who accessed, modified, shared, or deleted content, with time stamps and location data. These logs can be exported via SIEM feeds, searched, filtered, and utilized in compliance reports.
Kiteworks balances stringent security requirements with business efficiency through its granular permission system. The platform offers customizable folder roles (Owner, Manager, Collaborator, Downloader, Viewer, Uploader) and zero-trust data exchanges that automatically apply appropriate controls based on context, allowing organizations to maintain security without impeding legitimate work processes.
Kiteworks tracks all international transfers through its comprehensive audit logs, recording when files are shared across domains and geographic locations. The platform’s geofencing and IP address restrictions help enforce transfer limitations, while its hardened virtual appliance architecture provides the technical safeguards required for compliant cross-border data movements under BDSG provisions.
FEATURED RESOURCES

Partner Use Cases: Kiteworks Private Content Network Innovations

Top 10 Trends in Data Encryption: An In-depth Analysis on AES-256

Tyrol Military Command: Protecting PII and PHI in Transit and at Rest for GDPR
IT, SECURITY, PRIVACY, AND COMPLIANCE LEADERS AT THOUSANDS OF THE WORLD’S LEADING ENTERPRISES AND GOVERNMENT AGENCIES TRUST KITEWORKS